Minimum Spanning Tree Union-Find Data Structure. Feb 28, 2018 CSCI211 - Sprenkle. Comcast wants to lay cable in a neighborhood. Neighborhood Layout
|
|
|
- Ernest Francis
- 5 years ago
- Views:
Transcription
1 Objec&ves Minimum Spanning Tree Union-Find Data Structure Feb, 0 CSCI - Sprenkle Started teasing out some algorithms. Laying Cable Focus on commonality: what should our final solution look like? Comcast wants to lay cable in a neighborhood Ø Reach all houses Ø Least cost Neighborhood Layout Cost of laying cable btw houses depends on amount of cable, landscaping, obstacles, etc. 9 Feb, 0 CSCI - Sprenkle
2 Minimum Spanning Tree (MST) Spanning tree: spans all nodes in graph Given a connected graph G = (V, E) with posi&ve edge weights c e, an MST is a subset of the edges T E such that T is a spanning tree whose sum of edge weights is minimized 0 G = (V, E) 9 9 T, Σ e T c e = 0 Feb, 0 CSCI - Sprenkle Examples Identify spanning trees and which is the minimal spanning tree. Graph A B C D Feb, 0 CSCI - Sprenkle
3 Examples Identify spanning trees and which is the minimal spanning tree. Graph A B A B MST: C D C D Other Spanning Trees: A B A B C D C D Feb, 0 CSCI - Sprenkle MST Applica&ons Network design Ø telephone, electrical, hydraulic, TV cable, computer, road Approxima&on algorithms for NP-hard problems Ø traveling salesperson problem, Steiner tree Indirect applica&ons Ø max bozleneck paths Ø image registra&on with Renyi entropy Ø learning salient features for real-&me face verifica&on Ø reducing data storage in sequencing amino acids in a protein Ø model locality of par&cle interac&ons in turbulent fluid flows Cluster analysis ~eppstein/gina/mst.html Feb, 0 CSCI - Sprenkle
4 Ideas for Solu&ons? Cayley's Theorem. There are n n- spanning trees Towards a solu&on Ø Where to start? can't solve by brute force 0 9 G = (V, E) Feb, 0 CSCI - Sprenkle Minimum Spanning Tree Given a connected graph G = (V, E) with posi&ve edge weights c e, an MST is a subset of the edges T E such that T is a spanning tree whose sum of edge weights is minimized 0 G = (V, E) 9 Why must the solution be a tree? Feb, 0 CSCI - Sprenkle T, Σ e T c e = 0 9
5 Minimum Spanning Tree Assume have a minimal solu&on that is not a tree, i.e., it has a cycle What could we do? Ø What do we know about the edges? Ø How does that change the cost of the solu&on? Feb, 0 CSCI - Sprenkle 9 Minimum Spanning Tree Proof by Contradic&on. Assume have a minimal solu&on V that is not a tree, i.e., it has a cycle Contains edges to all nodes because solu&on must be connected (spanning) Remove an edge from the cycle Ø Can s&ll reach all nodes (could go long way around ) Ø But at lower total cost Ø Contradic&on to our minimal solu&on Feb, 0 CSCI - Sprenkle 0
6 Greedy Algorithms All three algorithms produce a MST Prim's algorithm. Ø Start with some root node s and greedily grow a tree T from s outward Ø At each step, add cheapest edge e to T that has exactly one endpoint in T Ø Similar to Dijkstra s (but simpler) Kruskal's algorithm. Ø Start with T = φ Ø Consider edges in ascending order of cost Ø Insert edge e in T unless doing so would create a cycle Reverse-Delete algorithm. Ø Start with T = E Ø Consider edges in descending order of cost Ø Delete edge e from T unless doing so would disconnect T What do these algorithms have/do/check in common? Feb, 0 CSCI - Sprenkle What Do These Algorithms Have in Common? When is it safe to include an edge in the minimum spanning tree? Cut Property When is it safe to eliminate an edge from the minimum spanning tree? Cycle Property Feb, 0 CSCI - Sprenkle
7 Cut and Cycle Proper&es Simplifying assump&on: All edge costs c e are dis&nct MST is unique Cut property. Let S be any subset of nodes, and let e be the min cost edge with exactly one endpoint in S. Then MST contains e. Cycle property. Let C be any cycle, and let f be the max cost edge belonging to C. Then MST does not contain f. f C S e Cut Property: e is in MST Cycle Property: f is not in MST Let s try to prove these Feb, 0 CSCI - Sprenkle Cycles and Cuts Cycle. Set of edges in the form a-b, b-c, c-d,, y-z, z-a Cycle C = -, -, -, -, -, - Feb, 0 CSCI - Sprenkle
8 Cycles and Cuts Cycle. Set of edges in the form a-b, b-c, c-d,, y-z, z-a Cycle C = -, -, -, -, -, - Cutset. A cut is a subset of nodes S. The corresponding cutset D is the subset of edges with exactly one endpoint in S. Feb, 0 CSCI - Sprenkle Cut S = {,, } Cutset D = -, -, -, -, - Cycle-Cut Intersec&on Claim. A cycle and a cutset intersect in an even number of edges Cycle C = -, -, -, -, -, - Cut S = {,, } Cutset D = -, -, -, -, - Intersection = -, - What are the possibilities for the cycle? Feb, 0 CSCI - Sprenkle
9 Cycle-Cut Intersec&on Claim. A cycle and a cutset intersect in an even number of edges Proof sketch Cycle C = -, -, -, -, -, - Cut S = {,, } Cutset D = -, -, -, -, - Intersection = -, -. Cycle all in S. Cycle not in S. Cycle has to go from SàV-S and back (Cut) S Edges link to not-cut V - S Feb, 0 CSCI - Sprenkle Proving Cut Property: OK to Include Edge Simplifying assump&on: All edge costs c e are dis&nct. Cut property. Let S be any subset of nodes, and let e be the min cost edge with exactly one endpoint in S. Then the MST T* contains e. Pf.? Feb, 0 CSCI - Sprenkle 9
10 Proving Cut Property: OK to Include Edge Simplifying assump&on: All edge costs c e are dis&nct. Cut property. Let S be any subset of nodes, and let e be the min cost edge with exactly one endpoint in S. Then the MST T* contains e. Pf. (exchange argument) Ø Suppose there is an MST T* that does not contain e What do we know about T, by defn? What do we know about the nodes e connects? Feb, 0 CSCI - Sprenkle 9 Proving Cut Property: OK to Include Edge Cut property. Let S be any subset of nodes, and let e be the min cost edge with exactly one endpoint in S. Then the MST T* contains e. Pf. (exchange argument) Ø Suppose there is an MST T* that does not contain e Ø Adding e to T* creates a cycle C in T* Ø Edge e is in cycle C and in cutset corresponding to S there exists another edge, say f, that is in both C and S s cutset Which means? e Feb, 0 CSCI - Sprenkle 0 S f 0
11 Proving Cut Property: OK to Include Edge Cut property. Let S be any subset of nodes, and let e be the min cost edge with exactly one endpoint in S. Then the MST T* contains e. Pf. (exchange argument) Ø Suppose there is an MST T* that does not contain e Ø Adding e to T* creates a cycle C in T* Ø Edge e is in cycle C and in cutset corresponding to S there exists another edge, say f, that is in both C and S s cutset Ø T' = T* { e } - { f } is also a spanning tree Ø Since c e < c f, cost(t') < cost(t*) f Ø This is a contradic&on. S e Feb, 0 CSCI - Sprenkle Proving Cycle Property: OK to Remove Edge Simplifying assump&on: All edge costs c e are dis&nct Cycle property. Let C be any cycle in G, and let f be the max cost edge belonging to C. Then the MST T* does not contain f. Ideas about approach? Feb, 0 CSCI - Sprenkle
12 Cycle Property: OK to Remove Edge Cycle property. Let C be any cycle in G, and let f be the max cost edge belonging to C. Then the MST T* does not contain f. Pf. (exchange argument) Ø Suppose f belongs to T* Ø Dele&ng f from T* creates a cut S in T* Ø Edge f is both in the cycle C and in the cutset S there exists another edge, say e, that is in both C and S Ø T' = T* { e } - { f } is also a spanning tree Ø Since c e < c f, cost(t') < cost(t*) f Ø This is a contradic&on. S Feb, 0 CSCI - Sprenkle e Summary of What Just Proved Simplifying assump&on: All edge costs c e are dis&nct MST is unique Cut property. Let S be any subset of nodes, and let e be the min cost edge with exactly one endpoint in S. Then MST contains e. Cycle property. Let C be any cycle, and let f be the max cost edge belonging to C. Then MST does not contain f. f C S e Cut Property: e is in MST Cycle Property: f is not in MST Feb, 0 CSCI - Sprenkle
13 Prim s Algorithm [Jarník 90, Dijkstra 9, Prim 99] Start with some root node s and greedily grow a tree T from s outward. At each step, add the cheapest edge e to T that has exactly one endpoint in T. How can we prove its correctness? Feb, 0 CSCI - Sprenkle Prim s Algorithm: Proof of Correctness Ini&alize S to be any node Apply cut property to S Ø Add min cost edge (v, u) in cutset corresponding to S, and add one new explored node u to S S Ideas about implementation? Feb, 0 CSCI - Sprenkle
14 Looking Ahead Problem Set due Friday Feb, 0 CSCI - Sprenkle
CS 4407 Algorithms Greedy Algorithms and Minimum Spanning Trees
 CS 4407 Algorithms Greedy Algorithms and Minimum Spanning Trees Prof. Gregory Provan Department of Computer Science University College Cork 1 Sample MST 6 5 4 9 14 10 2 3 8 15 Greedy Algorithms When are
CS 4407 Algorithms Greedy Algorithms and Minimum Spanning Trees Prof. Gregory Provan Department of Computer Science University College Cork 1 Sample MST 6 5 4 9 14 10 2 3 8 15 Greedy Algorithms When are
Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times
 Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Spatial Chaining Methods for International Comparisons of Prices and Real Expenditures D.S. Prasada Rao The University of Queensland
 Spatial Chaining Methods for International Comparisons of Prices and Real Expenditures D.S. Prasada Rao The University of Queensland Jointly with Robert Hill, Sriram Shankar and Reza Hajargasht 1 PPPs
Spatial Chaining Methods for International Comparisons of Prices and Real Expenditures D.S. Prasada Rao The University of Queensland Jointly with Robert Hill, Sriram Shankar and Reza Hajargasht 1 PPPs
Text UI. Data Store Ø Example of a backend to a real Could add a different user interface. Good judgment comes from experience
 Reviewing Lab 10 Text UI Created two classes Ø Used one class within another class Ø Tested them Graphical UI Backend Data Store Ø Example of a backend to a real applica@on Could add a different user interface
Reviewing Lab 10 Text UI Created two classes Ø Used one class within another class Ø Tested them Graphical UI Backend Data Store Ø Example of a backend to a real applica@on Could add a different user interface
CSCI211: Intro Objectives
 CSCI211: Intro Objectives Introduction to Algorithms, Analysis Course summary Reviewing proof techniques Jan 7, 2019 Sprenkle CSCI211 1 My Bio From Dallastown, PA B.S., Gettysburg College M.S., Duke University
CSCI211: Intro Objectives Introduction to Algorithms, Analysis Course summary Reviewing proof techniques Jan 7, 2019 Sprenkle CSCI211 1 My Bio From Dallastown, PA B.S., Gettysburg College M.S., Duke University
Objec&ves. Usability Project Discussion. May 9, 2016 Sprenkle - CSCI335 1
 Objec&ves Usability Project Discussion May 9, 2016 Sprenkle - CSCI335 1 JavaScript review True or False: JavaScript is just like Java How do you declare a variable? (2 ways) How do you write text to the
Objec&ves Usability Project Discussion May 9, 2016 Sprenkle - CSCI335 1 JavaScript review True or False: JavaScript is just like Java How do you declare a variable? (2 ways) How do you write text to the
Political Districting for Elections to the German Bundestag: An Optimization-Based Multi-Stage Heuristic Respecting Administrative Boundaries
 Political Districting for Elections to the German Bundestag: An Optimization-Based Multi-Stage Heuristic Respecting Administrative Boundaries Sebastian Goderbauer 1 Electoral Districts in Elections to
Political Districting for Elections to the German Bundestag: An Optimization-Based Multi-Stage Heuristic Respecting Administrative Boundaries Sebastian Goderbauer 1 Electoral Districts in Elections to
Coalitional Game Theory
 Coalitional Game Theory Game Theory Algorithmic Game Theory 1 TOC Coalitional Games Fair Division and Shapley Value Stable Division and the Core Concept ε-core, Least core & Nucleolus Reading: Chapter
Coalitional Game Theory Game Theory Algorithmic Game Theory 1 TOC Coalitional Games Fair Division and Shapley Value Stable Division and the Core Concept ε-core, Least core & Nucleolus Reading: Chapter
The Australian Society for Operations Research
 The Australian Society for Operations Research www.asor.org.au ASOR Bulletin Volume 34, Issue, (06) Pages -4 A minimum spanning tree with node index Elias Munapo School of Economics and Decision Sciences,
The Australian Society for Operations Research www.asor.org.au ASOR Bulletin Volume 34, Issue, (06) Pages -4 A minimum spanning tree with node index Elias Munapo School of Economics and Decision Sciences,
Analyzing proofs Introduction to problem solving. Wiki: Everyone log in okay? Decide on either using a blog or wiki-style journal?
 Objectives Analyzing proofs Introduction to problem solving Ø Our process, through an example Wiki: Everyone log in okay? Decide on either using a blog or wiki-style journal? 1 Review What are our goals
Objectives Analyzing proofs Introduction to problem solving Ø Our process, through an example Wiki: Everyone log in okay? Decide on either using a blog or wiki-style journal? 1 Review What are our goals
Kruskal's MST Algorithm with step-by-step execution
 Kruskal's MST Algorithm with step-by-step execution Daniel Michel Tavera Student at National Autonomous University of Mexico (UNAM) Mexico e-mail: daniel_michel@ciencias.unam.mx Social service project
Kruskal's MST Algorithm with step-by-step execution Daniel Michel Tavera Student at National Autonomous University of Mexico (UNAM) Mexico e-mail: daniel_michel@ciencias.unam.mx Social service project
Prim's MST Algorithm with step-by-step execution
 Prim's MST Algorithm with step-by-step execution Daniel Michel Tavera Student at National Autonomous University of Mexico (UNAM) Mexico e-mail: daniel_michel@ciencias.unam.mx Social service project director:
Prim's MST Algorithm with step-by-step execution Daniel Michel Tavera Student at National Autonomous University of Mexico (UNAM) Mexico e-mail: daniel_michel@ciencias.unam.mx Social service project director:
Designing a Social Network Prep for Lab 10. March 26, 2018 Sprenkle - CSCI Why classes and objects? How do we create new data types?
 Objec(ves Designing a Social Network Prep for Lab 10 March 26, 2018 Sprenkle - CSCI111 1 Review What trends did we see in the names of students at W&L? Ø What was as you expected? Ø What surprised you?
Objec(ves Designing a Social Network Prep for Lab 10 March 26, 2018 Sprenkle - CSCI111 1 Review What trends did we see in the names of students at W&L? Ø What was as you expected? Ø What surprised you?
Uninformed search. Lirong Xia
 Uninformed search Lirong Xia Spring, 2017 Today s schedule ØRational agents ØSearch problems State space graph: modeling the problem Search trees: scratch paper for solution ØUninformed search Depth first
Uninformed search Lirong Xia Spring, 2017 Today s schedule ØRational agents ØSearch problems State space graph: modeling the problem Search trees: scratch paper for solution ØUninformed search Depth first
CSCI 325: Distributed Systems. Objec?ves. Professor Sprenkle. Course overview Overview of distributed systems Introduc?on to reading research papers
 CSCI 325: Distributed Systems Professor Sprenkle Objec?ves Course overview Overview of distributed systems Introduc?on to reading research papers Sept 8, 2017 Sprenkle - CSCI 325 2 1 Distributed Systems?
CSCI 325: Distributed Systems Professor Sprenkle Objec?ves Course overview Overview of distributed systems Introduc?on to reading research papers Sept 8, 2017 Sprenkle - CSCI 325 2 1 Distributed Systems?
ECE250: Algorithms and Data Structures Trees
 ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
Coverage tools Eclipse Debugger Object-oriented Design Principles. Oct 26, 2016 Sprenkle - CSCI209 1
 Objec&ves Coverage tools Eclipse Debugger Object-oriented Design Principles Ø Design in the Small Ø DRY Ø Single responsibility principle Ø Shy Ø Open-closed principle Oct 26, 2016 Sprenkle - CSCI209 1
Objec&ves Coverage tools Eclipse Debugger Object-oriented Design Principles Ø Design in the Small Ø DRY Ø Single responsibility principle Ø Shy Ø Open-closed principle Oct 26, 2016 Sprenkle - CSCI209 1
Search Trees. Chapter 10. CSE 2011 Prof. J. Elder Last Updated: :51 PM
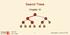 Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Constraint satisfaction problems. Lirong Xia
 Constraint satisfaction problems Lirong Xia Spring, 2017 Project 1 Ø You can use Windows Ø Read the instruction carefully, make sure you understand the goal search for YOUR CODE HERE Ø Ask and answer questions
Constraint satisfaction problems Lirong Xia Spring, 2017 Project 1 Ø You can use Windows Ø Read the instruction carefully, make sure you understand the goal search for YOUR CODE HERE Ø Ask and answer questions
STUDY GUIDE FOR TEST 2
 STUDY GUIDE FOR TEST 2 MATH 303. SPRING 2006. INSTRUCTOR: PROFESSOR AITKEN The test will cover Chapters 4, 5, and 6. Chapter 4: The Mathematics of Voting Sample Exercises: 1, 3, 5, 7, 8, 10, 14, 15, 17,
STUDY GUIDE FOR TEST 2 MATH 303. SPRING 2006. INSTRUCTOR: PROFESSOR AITKEN The test will cover Chapters 4, 5, and 6. Chapter 4: The Mathematics of Voting Sample Exercises: 1, 3, 5, 7, 8, 10, 14, 15, 17,
HASHGRAPH CONSENSUS: DETAILED EXAMPLES
 HASHGRAPH CONSENSUS: DETAILED EXAMPLES LEEMON BAIRD BAIRD@SWIRLDS.COM DECEMBER 11, 2016 SWIRLDS TECH REPORT SWIRLDS-TR-2016-02 ABSTRACT: The Swirlds hashgraph consensus algorithm is explained through a
HASHGRAPH CONSENSUS: DETAILED EXAMPLES LEEMON BAIRD BAIRD@SWIRLDS.COM DECEMBER 11, 2016 SWIRLDS TECH REPORT SWIRLDS-TR-2016-02 ABSTRACT: The Swirlds hashgraph consensus algorithm is explained through a
Designing police patrol districts on street network
 Designing police patrol districts on street network Huanfa Chen* 1 and Tao Cheng 1 1 SpaceTimeLab for Big Data Analytics, Department of Civil, Environmental, and Geomatic Engineering, University College
Designing police patrol districts on street network Huanfa Chen* 1 and Tao Cheng 1 1 SpaceTimeLab for Big Data Analytics, Department of Civil, Environmental, and Geomatic Engineering, University College
Estimating the Margin of Victory for Instant-Runoff Voting
 Estimating the Margin of Victory for Instant-Runoff Voting David Cary Abstract A general definition is proposed for the margin of victory of an election contest. That definition is applied to Instant Runoff
Estimating the Margin of Victory for Instant-Runoff Voting David Cary Abstract A general definition is proposed for the margin of victory of an election contest. That definition is applied to Instant Runoff
Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3)
 B.Y. Choueiry 1 Instructor s notes #5 Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3) Introduction to Artificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/~choueiry/f17-476-876
B.Y. Choueiry 1 Instructor s notes #5 Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3) Introduction to Artificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/~choueiry/f17-476-876
A MINIMUM DISTANCE AND THE GENERALISED EKS APPROACHES TO MULTILATERAL COMPARISONS OF PRICES AND REAL INCOMES
 A MINIMUM DISTANCE AND THE GENERALISED EKS APPROACHES TO MULTILATERAL COMPARISONS OF PRICES AND REAL INCOMES D.S. Prasada Rao Sriram Shankar School of Economics The University of Queensland Australia Golamreza
A MINIMUM DISTANCE AND THE GENERALISED EKS APPROACHES TO MULTILATERAL COMPARISONS OF PRICES AND REAL INCOMES D.S. Prasada Rao Sriram Shankar School of Economics The University of Queensland Australia Golamreza
Review: SoBware Development
 Objec&ves Tes&ng Oct 12, 2016 Sprenkle - CSCI209 1 Review: SoBware Development From Monday Oct 12, 2016 Sprenkle - CSCI209 2 1 CLASSPATH Oct 12, 2016 Sprenkle - CSCI209 3 Classpath Tells the compiler or
Objec&ves Tes&ng Oct 12, 2016 Sprenkle - CSCI209 1 Review: SoBware Development From Monday Oct 12, 2016 Sprenkle - CSCI209 2 1 CLASSPATH Oct 12, 2016 Sprenkle - CSCI209 3 Classpath Tells the compiler or
Aggregating Dependency Graphs into Voting Agendas in Multi-Issue Elections
 Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Aggregating Dependency Graphs into Voting Agendas in Multi-Issue Elections Stéphane Airiau, Ulle Endriss, Umberto
Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Aggregating Dependency Graphs into Voting Agendas in Multi-Issue Elections Stéphane Airiau, Ulle Endriss, Umberto
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Satisfaction Approval Voting
 Satisfaction Approval Voting Steven J. Brams Department of Politics New York University New York, NY 10012 USA D. Marc Kilgour Department of Mathematics Wilfrid Laurier University Waterloo, Ontario N2L
Satisfaction Approval Voting Steven J. Brams Department of Politics New York University New York, NY 10012 USA D. Marc Kilgour Department of Mathematics Wilfrid Laurier University Waterloo, Ontario N2L
Computational Social Choice: Spring 2017
 Computational Social Choice: Spring 2017 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today So far we saw three voting rules: plurality, plurality
Computational Social Choice: Spring 2017 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today So far we saw three voting rules: plurality, plurality
arxiv: v1 [cs.gt] 11 Jul 2018
![arxiv: v1 [cs.gt] 11 Jul 2018 arxiv: v1 [cs.gt] 11 Jul 2018](/thumbs/89/99238134.jpg) Sequential Voting with Confirmation Network Yakov Babichenko yakovbab@tx.technion.ac.il Oren Dean orendean@campus.technion.ac.il Moshe Tennenholtz moshet@ie.technion.ac.il arxiv:1807.03978v1 [cs.gt] 11
Sequential Voting with Confirmation Network Yakov Babichenko yakovbab@tx.technion.ac.il Oren Dean orendean@campus.technion.ac.il Moshe Tennenholtz moshet@ie.technion.ac.il arxiv:1807.03978v1 [cs.gt] 11
Hat problem on a graph
 Hat problem on a graph Submitted by Marcin Piotr Krzywkowski to the University of Exeter as a thesis for the degree of Doctor of Philosophy by Publication in Mathematics In April 2012 This thesis is available
Hat problem on a graph Submitted by Marcin Piotr Krzywkowski to the University of Exeter as a thesis for the degree of Doctor of Philosophy by Publication in Mathematics In April 2012 This thesis is available
Quantum theory of scattering by a potential. Lecture notes 8 (based on CT, Sec4on 8)
 Quantum theory of scattering by a potential Lecture notes 8 (based on CT, Sec4on 8) ì Introduction Ø In physics, the fundamental interac4ons between par4cles are o?en studied by le@ng these par4cles collide
Quantum theory of scattering by a potential Lecture notes 8 (based on CT, Sec4on 8) ì Introduction Ø In physics, the fundamental interac4ons between par4cles are o?en studied by le@ng these par4cles collide
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
How hard is it to control sequential elections via the agenda?
 How hard is it to control sequential elections via the agenda? Vincent Conitzer Department of Computer Science Duke University Durham, NC 27708, USA conitzer@cs.duke.edu Jérôme Lang LAMSADE Université
How hard is it to control sequential elections via the agenda? Vincent Conitzer Department of Computer Science Duke University Durham, NC 27708, USA conitzer@cs.duke.edu Jérôme Lang LAMSADE Université
Combating Friend Spam Using Social Rejections
 Combating Friend Spam Using Social Rejections Qiang Cao Duke University Michael Sirivianos Xiaowei Yang Kamesh Munagala Cyprus Univ. of Technology Duke University Duke University Friend Spam in online
Combating Friend Spam Using Social Rejections Qiang Cao Duke University Michael Sirivianos Xiaowei Yang Kamesh Munagala Cyprus Univ. of Technology Duke University Duke University Friend Spam in online
Midterm Review. EECS 2011 Prof. J. Elder - 1 -
 Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Influence in Social Networks
 CSCI 3210: Computational Game Theory Influence Games Ref: Irfan & Ortiz, AI (2014) Reading: Sections 1 3(up to pg. 86), Sections 4.5, 5 (no proof), 6 bowdoin.edu/~mirfan/papers/irfan_ortiz_influence_games_ai2014.pdf
CSCI 3210: Computational Game Theory Influence Games Ref: Irfan & Ortiz, AI (2014) Reading: Sections 1 3(up to pg. 86), Sections 4.5, 5 (no proof), 6 bowdoin.edu/~mirfan/papers/irfan_ortiz_influence_games_ai2014.pdf
Comparison Sorts. EECS 2011 Prof. J. Elder - 1 -
 Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Adapting the Social Network to Affect Elections
 Adapting the Social Network to Affect Elections Sigal Sina Dept of Computer Science Bar Ilan University, Israel sinasi@macs.biu.ac.il Noam Hazon Dept of Computer Science and Mathematics Ariel University,
Adapting the Social Network to Affect Elections Sigal Sina Dept of Computer Science Bar Ilan University, Israel sinasi@macs.biu.ac.il Noam Hazon Dept of Computer Science and Mathematics Ariel University,
Cloning in Elections
 Proceedings of the Twenty-Fourth AAAI Conference on Artificial Intelligence (AAAI-10) Cloning in Elections Edith Elkind School of Physical and Mathematical Sciences Nanyang Technological University Singapore
Proceedings of the Twenty-Fourth AAAI Conference on Artificial Intelligence (AAAI-10) Cloning in Elections Edith Elkind School of Physical and Mathematical Sciences Nanyang Technological University Singapore
Cluster Analysis. (see also: Segmentation)
 Cluster Analysis (see also: Segmentation) Cluster Analysis Ø Unsupervised: no target variable for training Ø Partition the data into groups (clusters) so that: Ø Observations within a cluster are similar
Cluster Analysis (see also: Segmentation) Cluster Analysis Ø Unsupervised: no target variable for training Ø Partition the data into groups (clusters) so that: Ø Observations within a cluster are similar
NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York
 NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York DEPARTMENT: Mathematics COURSE: MAT 2440/ MA 440 TITLE: DESCRIPTION: TEXTS: Discrete Structures and Algorithms I This course introduces
NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York DEPARTMENT: Mathematics COURSE: MAT 2440/ MA 440 TITLE: DESCRIPTION: TEXTS: Discrete Structures and Algorithms I This course introduces
Overview. Ø Neural Networks are considered black-box models Ø They are complex and do not provide much insight into variable relationships
 Neural Networks Overview Ø s are considered black-box models Ø They are complex and do not provide much insight into variable relationships Ø They have the potential to model very complicated patterns
Neural Networks Overview Ø s are considered black-box models Ø They are complex and do not provide much insight into variable relationships Ø They have the potential to model very complicated patterns
Computational challenges in analyzing and moderating online social discussions
 Computational challenges in analyzing and moderating online social discussions Aristides Gionis Department of Computer Science Aalto University Machine learning coffee seminar Oct 23, 2017 social media
Computational challenges in analyzing and moderating online social discussions Aristides Gionis Department of Computer Science Aalto University Machine learning coffee seminar Oct 23, 2017 social media
Lab 11: Pair Programming. Review: Pair Programming Roles
 Lab 11: Pair Programming Apr 2, 2019 Sprenkle - CSCI111 1 Review: Pair Programming Roles Driver (Like the role I play when we write programs in class) Uses keyboard and mouse to execute all actions on
Lab 11: Pair Programming Apr 2, 2019 Sprenkle - CSCI111 1 Review: Pair Programming Roles Driver (Like the role I play when we write programs in class) Uses keyboard and mouse to execute all actions on
Support Vector Machines
 Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
File Systems: Fundamentals
 File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
Coalitional Game Theory for Communication Networks: A Tutorial
 Coalitional Game Theory for Communication Networks: A Tutorial Walid Saad 1, Zhu Han 2, Mérouane Debbah 3, Are Hjørungnes 1 and Tamer Başar 4 1 UNIK - University Graduate Center, University of Oslo, Kjeller,
Coalitional Game Theory for Communication Networks: A Tutorial Walid Saad 1, Zhu Han 2, Mérouane Debbah 3, Are Hjørungnes 1 and Tamer Başar 4 1 UNIK - University Graduate Center, University of Oslo, Kjeller,
c M. J. Wooldridge, used by permission/updated by Simon Parsons, Spring
 Today LECTURE 8: MAKING GROUP DECISIONS CIS 716.5, Spring 2010 We continue thinking in the same framework as last lecture: multiagent encounters game-like interactions participants act strategically We
Today LECTURE 8: MAKING GROUP DECISIONS CIS 716.5, Spring 2010 We continue thinking in the same framework as last lecture: multiagent encounters game-like interactions participants act strategically We
Dimension Reduction. Why and How
 Dimension Reduction Why and How The Curse of Dimensionality As the dimensionality (i.e. number of variables) of a space grows, data points become so spread out that the ideas of distance and density become
Dimension Reduction Why and How The Curse of Dimensionality As the dimensionality (i.e. number of variables) of a space grows, data points become so spread out that the ideas of distance and density become
Bribery in voting with CP-nets
 Ann Math Artif Intell (2013) 68:135 160 DOI 10.1007/s10472-013-9330-5 Bribery in voting with CP-nets Nicholas Mattei Maria Silvia Pini Francesca Rossi K. Brent Venable Published online: 7 February 2013
Ann Math Artif Intell (2013) 68:135 160 DOI 10.1007/s10472-013-9330-5 Bribery in voting with CP-nets Nicholas Mattei Maria Silvia Pini Francesca Rossi K. Brent Venable Published online: 7 February 2013
Priority Queues & Heaps
 Priority Queues & Heaps Chapter 8-1 - The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List
Priority Queues & Heaps Chapter 8-1 - The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List
Tengyu Ma Facebook AI Research. Based on joint work with Rong Ge (Duke) and Jason D. Lee (USC)
 Tengyu Ma Facebook AI Research Based on joint work with Rong Ge (Duke) and Jason D. Lee (USC) Users Optimization Researchers function f Solution gradient descent local search Convex relaxation + Rounding
Tengyu Ma Facebook AI Research Based on joint work with Rong Ge (Duke) and Jason D. Lee (USC) Users Optimization Researchers function f Solution gradient descent local search Convex relaxation + Rounding
Patterns in Congressional Earmarks
 Patterns in Congressional Earmarks Chris Musialek University of Maryland, College Park 8 November, 2012 Introduction This dataset from Taxpayers for Common Sense captures Congressional appropriations earmarks
Patterns in Congressional Earmarks Chris Musialek University of Maryland, College Park 8 November, 2012 Introduction This dataset from Taxpayers for Common Sense captures Congressional appropriations earmarks
Online Appendix: Trafficking Networks and the Mexican Drug War
 Online Appendix: Trafficking Networks and the Mexican Drug War Melissa Dell February 6, 2015 Contents A-1 Estimation appendix A 3 A-1.1 The shortest paths problem........................ A 3 A-1.2 Solving
Online Appendix: Trafficking Networks and the Mexican Drug War Melissa Dell February 6, 2015 Contents A-1 Estimation appendix A 3 A-1.1 The shortest paths problem........................ A 3 A-1.2 Solving
A Framework for the Quantitative Evaluation of Voting Rules
 A Framework for the Quantitative Evaluation of Voting Rules Michael Munie Computer Science Department Stanford University, CA munie@stanford.edu Yoav Shoham Computer Science Department Stanford University,
A Framework for the Quantitative Evaluation of Voting Rules Michael Munie Computer Science Department Stanford University, CA munie@stanford.edu Yoav Shoham Computer Science Department Stanford University,
Improved Boosting Algorithms Using Confidence-rated Predictions
 Improved Boosting Algorithms Using Confidence-rated Predictions ÊÇÊÌ º ËÀÈÁÊ schapire@research.att.com AT&T Labs, Shannon Laboratory, 18 Park Avenue, Room A279, Florham Park, NJ 7932-971 ÇÊÅ ËÁÆÊ singer@research.att.com
Improved Boosting Algorithms Using Confidence-rated Predictions ÊÇÊÌ º ËÀÈÁÊ schapire@research.att.com AT&T Labs, Shannon Laboratory, 18 Park Avenue, Room A279, Florham Park, NJ 7932-971 ÇÊÅ ËÁÆÊ singer@research.att.com
Real-Time Wireless Control Networks for Cyber-Physical Systems
 Real-Time Wireless Control Networks for Cyber-Physical Systems Chenyang Lu Cyber-Physical Systems Laboratory Department of Computer Science and Engineering Wireless Control Networks Ø Real-time Sensor
Real-Time Wireless Control Networks for Cyber-Physical Systems Chenyang Lu Cyber-Physical Systems Laboratory Department of Computer Science and Engineering Wireless Control Networks Ø Real-time Sensor
11/15/13. Objectives. Review. Our Screen Saver Dependencies. Our Screen Saver Dependencies. Project Deliverables Timeline TEAM FINAL PROJECT
 Objectives Team Final Project Review What design pattern is used in the screen savers code? What is the design principle we discussed on Wednesday? What was likely to change? Open up Eclipse Nov 15, 2013
Objectives Team Final Project Review What design pattern is used in the screen savers code? What is the design principle we discussed on Wednesday? What was likely to change? Open up Eclipse Nov 15, 2013
Evaluation of election outcomes under uncertainty
 Evaluation of election outcomes under uncertainty Noam Hazon, Yonatan umann, Sarit Kraus, Michael Wooldridge Department of omputer Science Department of omputer Science ar-ilan University University of
Evaluation of election outcomes under uncertainty Noam Hazon, Yonatan umann, Sarit Kraus, Michael Wooldridge Department of omputer Science Department of omputer Science ar-ilan University University of
Objec&ves. Tes&ng 11/8/16. by Frederick P. Brooks, Jr., 1986
 Objec&ves Tes&ng Oct 12, 2016 Sprenkle - CSCI209 1 No Silver Bullet: Essence and Accidents of SoHware Engineering Of all the monsters that fill the nightmares of our folklore, none terrify more than werewolves,
Objec&ves Tes&ng Oct 12, 2016 Sprenkle - CSCI209 1 No Silver Bullet: Essence and Accidents of SoHware Engineering Of all the monsters that fill the nightmares of our folklore, none terrify more than werewolves,
Multi-Winner Elections: Complexity of Manipulation, Control, and Winner-Determination
 Multi-Winner Elections: Complexity of Manipulation, Control, and Winner-Determination Ariel D. Procaccia and Jeffrey S. Rosenschein and Aviv Zohar School of Engineering and Computer Science The Hebrew
Multi-Winner Elections: Complexity of Manipulation, Control, and Winner-Determination Ariel D. Procaccia and Jeffrey S. Rosenschein and Aviv Zohar School of Engineering and Computer Science The Hebrew
MAC 2311 CALCULUS 1 FALL SEMESTER 2015
 MAC 2311 CALCULUS 1 FALL SEMESTER 2015 COURSE DESCRIPTION 95129 MAC 2311-006. Class meets at 12:00 13:50 TR in BU 307. URL: http://math.fau.edu/ford/syllabi/s15/mac2311/ Instructor: Dr. Timothy Ford, Professor
MAC 2311 CALCULUS 1 FALL SEMESTER 2015 COURSE DESCRIPTION 95129 MAC 2311-006. Class meets at 12:00 13:50 TR in BU 307. URL: http://math.fau.edu/ford/syllabi/s15/mac2311/ Instructor: Dr. Timothy Ford, Professor
Tengyu Ma Facebook AI Research. Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford)
 Tengyu Ma Facebook AI Research Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford) Ø Over-parameterization: # parameters # examples Ø a set of parameters that can Ø fit to training
Tengyu Ma Facebook AI Research Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford) Ø Over-parameterization: # parameters # examples Ø a set of parameters that can Ø fit to training
Decentralised solutions for renewable energies and water in developing countries
 Decentralised solutions for renewable energies and water in developing countries Energy and Water Solu0ons in sub- Saharan Africa 16. - 17. October 2014 Radolfzell at Lake Constance, Germany Dr. Julia
Decentralised solutions for renewable energies and water in developing countries Energy and Water Solu0ons in sub- Saharan Africa 16. - 17. October 2014 Radolfzell at Lake Constance, Germany Dr. Julia
A constraint based dependancy parser for Sanskrit
 A constraint based dependancy parser for Sanskrit Amba Kulkarni apksh@uohyd.ernet.in Department of Sanskrit Studies University of Hyderabad Hyderabad 19 Feb 2010 Calicut University Page 1 Æ Ó - Ý Ý Ñ ÚÝ
A constraint based dependancy parser for Sanskrit Amba Kulkarni apksh@uohyd.ernet.in Department of Sanskrit Studies University of Hyderabad Hyderabad 19 Feb 2010 Calicut University Page 1 Æ Ó - Ý Ý Ñ ÚÝ
Contact 3-Manifolds, Holomorphic Curves and Intersection Theory
 Contact 3-Manifolds, Holomorphic Curves and Intersection Theory (Durham University, August 2013) Chris Wendl University College London These slides plus detailed lecture notes (in progress) available at:
Contact 3-Manifolds, Holomorphic Curves and Intersection Theory (Durham University, August 2013) Chris Wendl University College London These slides plus detailed lecture notes (in progress) available at:
Event Based Sequential Program Development: Application to Constructing a Pointer Program
 Event Based Sequential Program Development: Application to Constructing a Pointer Program Jean-Raymond Abrial Consultant, Marseille, France jr@abrial.org Abstract. In this article, I present an event approach
Event Based Sequential Program Development: Application to Constructing a Pointer Program Jean-Raymond Abrial Consultant, Marseille, France jr@abrial.org Abstract. In this article, I present an event approach
Complexity of Manipulating Elections with Few Candidates
 Complexity of Manipulating Elections with Few Candidates Vincent Conitzer and Tuomas Sandholm Computer Science Department Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 {conitzer, sandholm}@cs.cmu.edu
Complexity of Manipulating Elections with Few Candidates Vincent Conitzer and Tuomas Sandholm Computer Science Department Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 {conitzer, sandholm}@cs.cmu.edu
Real- Time Wireless Control Networks for Cyber- Physical Systems
 Real- Time Wireless Control Networks for Cyber- Physical Systems Chenyang Lu Cyber- Physical Systems Laboratory Department of Computer Science and Engineering Wireless Control Networks Ø Real-time Ø Reliability
Real- Time Wireless Control Networks for Cyber- Physical Systems Chenyang Lu Cyber- Physical Systems Laboratory Department of Computer Science and Engineering Wireless Control Networks Ø Real-time Ø Reliability
Cloning in Elections 1
 Cloning in Elections 1 Edith Elkind, Piotr Faliszewski, and Arkadii Slinko Abstract We consider the problem of manipulating elections via cloning candidates. In our model, a manipulator can replace each
Cloning in Elections 1 Edith Elkind, Piotr Faliszewski, and Arkadii Slinko Abstract We consider the problem of manipulating elections via cloning candidates. In our model, a manipulator can replace each
LED545-series TECHNICAL DATA. Specifications. Absolute Maximum Ratings (T a =25 C) Electro-Optical Characteristics (T a =25 C)
 LED545-series TECHNICAL DATA Visible LED InGaN LED545-series are InGaN LEDs mounted on a lead frame and encapsulated in various types of epoxy lens, which offers different design settings. On forward bias,
LED545-series TECHNICAL DATA Visible LED InGaN LED545-series are InGaN LEDs mounted on a lead frame and encapsulated in various types of epoxy lens, which offers different design settings. On forward bias,
arxiv: v1 [cs.cc] 29 Sep 2015
![arxiv: v1 [cs.cc] 29 Sep 2015 arxiv: v1 [cs.cc] 29 Sep 2015](/thumbs/75/72239584.jpg) Often harder than in the Constructive Case: Destructive Bribery in CP-nets Britta Dorn 1, Dominikus Krüger 2, and Patrick Scharpfenecker 2 arxiv:1509.08628v1 [cs.cc] 29 Sep 2015 1 Faculty of Science, Dept.
Often harder than in the Constructive Case: Destructive Bribery in CP-nets Britta Dorn 1, Dominikus Krüger 2, and Patrick Scharpfenecker 2 arxiv:1509.08628v1 [cs.cc] 29 Sep 2015 1 Faculty of Science, Dept.
LED1200-series TECHNICAL DATA. Specifications. Absolute Maximum Ratings (T a =25 C) Electro-Optical Characteristics (T a =25 C)
 LED1200-series TECHNICAL DATA Infrared LED InGaAsP LED1200-series are InGaAsP LEDs mounted on a lead frame and encapsulated in various types of epoxy lens, which offers different design settings. On forward
LED1200-series TECHNICAL DATA Infrared LED InGaAsP LED1200-series are InGaAsP LEDs mounted on a lead frame and encapsulated in various types of epoxy lens, which offers different design settings. On forward
Need for a uniform European registra2on system for volunteer par2cipa2on? Annick Peremans Research Centre Aalst Belgium
 Need for a uniform European registra2on system for volunteer par2cipa2on? Research Centre Aalst Belgium Conflict of interest No grants received form any company men2oned in this presenta2on Presenta2on
Need for a uniform European registra2on system for volunteer par2cipa2on? Research Centre Aalst Belgium Conflict of interest No grants received form any company men2oned in this presenta2on Presenta2on
From Argument Games to Persuasion Dialogues
 From Argument Games to Persuasion Dialogues Nicolas Maudet (aka Nicholas of Paris) 08/02/10 (DGHRCM workshop) LAMSADE Université Paris-Dauphine 1 / 33 Introduction Main sources of inspiration for this
From Argument Games to Persuasion Dialogues Nicolas Maudet (aka Nicholas of Paris) 08/02/10 (DGHRCM workshop) LAMSADE Université Paris-Dauphine 1 / 33 Introduction Main sources of inspiration for this
Lab 3: Logistic regression models
 Lab 3: Logistic regression models In this lab, we will apply logistic regression models to United States (US) presidential election data sets. The main purpose is to predict the outcomes of presidential
Lab 3: Logistic regression models In this lab, we will apply logistic regression models to United States (US) presidential election data sets. The main purpose is to predict the outcomes of presidential
Analyzing and Representing Two-Mode Network Data Week 8: Reading Notes
 Analyzing and Representing Two-Mode Network Data Week 8: Reading Notes Wasserman and Faust Chapter 8: Affiliations and Overlapping Subgroups Affiliation Network (Hypernetwork/Membership Network): Two mode
Analyzing and Representing Two-Mode Network Data Week 8: Reading Notes Wasserman and Faust Chapter 8: Affiliations and Overlapping Subgroups Affiliation Network (Hypernetwork/Membership Network): Two mode
Agenda trees and sincere voting: a response to Schwartz
 Public Choice (2010) 145: 213 221 DOI 10.1007/s11127-009-9562-4 Agenda trees and sincere voting: a response to Schwartz Nicholas R. Miller Received: 27 July 2009 / Accepted: 30 October 2009 / Published
Public Choice (2010) 145: 213 221 DOI 10.1007/s11127-009-9562-4 Agenda trees and sincere voting: a response to Schwartz Nicholas R. Miller Received: 27 July 2009 / Accepted: 30 October 2009 / Published
NETWORK ANALYSIS OF INTERNATIONAL MIGRATION
 NETWORK ANALYSIS OF INTERNATIONAL MIGRATION Working Paper WP7/2016/06 Series WP7 Mathematical methods for decision making in economics, business and politics Моscow 2016 УДК 325:303 ББК 60.7 N46 Editors
NETWORK ANALYSIS OF INTERNATIONAL MIGRATION Working Paper WP7/2016/06 Series WP7 Mathematical methods for decision making in economics, business and politics Моscow 2016 УДК 325:303 ББК 60.7 N46 Editors
CS269I: Incentives in Computer Science Lecture #4: Voting, Machine Learning, and Participatory Democracy
 CS269I: Incentives in Computer Science Lecture #4: Voting, Machine Learning, and Participatory Democracy Tim Roughgarden October 5, 2016 1 Preamble Last lecture was all about strategyproof voting rules
CS269I: Incentives in Computer Science Lecture #4: Voting, Machine Learning, and Participatory Democracy Tim Roughgarden October 5, 2016 1 Preamble Last lecture was all about strategyproof voting rules
A Mathematical View on Voting and Power
 A Mathematical View on Voting and Power Werner Kirsch Abstract. In this article we describe some concepts, ideas and results from the mathematical theory of voting. We give a mathematical description of
A Mathematical View on Voting and Power Werner Kirsch Abstract. In this article we describe some concepts, ideas and results from the mathematical theory of voting. We give a mathematical description of
Evaluation of Election Outcomes under Uncertainty
 Evaluation of Election Outcomes under Uncertainty Noam Hazon, Yonatan umann, Sarit Kraus, Michael Wooldridge Department of omputer Science Department of omputer Science ar-ilan University University of
Evaluation of Election Outcomes under Uncertainty Noam Hazon, Yonatan umann, Sarit Kraus, Michael Wooldridge Department of omputer Science Department of omputer Science ar-ilan University University of
LED700-series TECHNICAL DATA. Specifications. Absolute Maximum Ratings (T a =25 C) Electro-Optical Characteristics (T a =25 C)
 LED700-series TECHNICAL DATA Infrared LED AlGaAs LED700-series are AlGaAs LEDs mounted on a lead frame and encapsulated in various types of epoxy lens, which offers different design settings. On forward
LED700-series TECHNICAL DATA Infrared LED AlGaAs LED700-series are AlGaAs LEDs mounted on a lead frame and encapsulated in various types of epoxy lens, which offers different design settings. On forward
Chapter. Sampling Distributions Pearson Prentice Hall. All rights reserved
 Chapter 8 Sampling Distributions 2010 Pearson Prentice Hall. All rights reserved Section 8.1 Distribution of the Sample Mean 2010 Pearson Prentice Hall. All rights reserved Objectives 1. Describe the distribution
Chapter 8 Sampling Distributions 2010 Pearson Prentice Hall. All rights reserved Section 8.1 Distribution of the Sample Mean 2010 Pearson Prentice Hall. All rights reserved Objectives 1. Describe the distribution
Chapter 11. Weighted Voting Systems. For All Practical Purposes: Effective Teaching
 Chapter Weighted Voting Systems For All Practical Purposes: Effective Teaching In observing other faculty or TA s, if you discover a teaching technique that you feel was particularly effective, don t hesitate
Chapter Weighted Voting Systems For All Practical Purposes: Effective Teaching In observing other faculty or TA s, if you discover a teaching technique that you feel was particularly effective, don t hesitate
Objec&ves. Review. So-ware Quality Metrics Sta&c Analysis Tools Refactoring for Extensibility
 Objec&ves So-ware Quality Metrics Sta&c Analysis Tools Refactoring for Extensibility Nov 2, 2016 Sprenkle - CSCI209 1 Review What principle did we focus on last class? What is the typical fix for designing
Objec&ves So-ware Quality Metrics Sta&c Analysis Tools Refactoring for Extensibility Nov 2, 2016 Sprenkle - CSCI209 1 Review What principle did we focus on last class? What is the typical fix for designing
Graph Structurings. 16. How to Structure Large Models - Obligatory Reading. Ø T. Fischer, Jörg Niere, L. Torunski, and Albert Zündorf, 'Story
 Fakultät Informatik, Institut für Software- und Multimediatechnik, Lehrstuhl für Softwaretechnologie 16. How to Structure Large Models - Graph Structurings Prof. Dr. U. Aßmann Technische Universität Dresden
Fakultät Informatik, Institut für Software- und Multimediatechnik, Lehrstuhl für Softwaretechnologie 16. How to Structure Large Models - Graph Structurings Prof. Dr. U. Aßmann Technische Universität Dresden
Do two parties represent the US? Clustering analysis of US public ideology survey
 Do two parties represent the US? Clustering analysis of US public ideology survey Louisa Lee 1 and Siyu Zhang 2, 3 Advised by: Vicky Chuqiao Yang 1 1 Department of Engineering Sciences and Applied Mathematics,
Do two parties represent the US? Clustering analysis of US public ideology survey Louisa Lee 1 and Siyu Zhang 2, 3 Advised by: Vicky Chuqiao Yang 1 1 Department of Engineering Sciences and Applied Mathematics,
Connecting Voting Theory and Graph Theory
 Connecting Voting Theory and Graph Theory Karl-Dieter Crisman Gordon College Willamette University Math Colloquium, October 13, 2016 Karl-Dieter Crisman (Gordon College) Graphs and Voting WU Colloquium
Connecting Voting Theory and Graph Theory Karl-Dieter Crisman Gordon College Willamette University Math Colloquium, October 13, 2016 Karl-Dieter Crisman (Gordon College) Graphs and Voting WU Colloquium
HANDS ACROSS BORDERS. An International Workshop on. Alterna(ve Mechanisms to Establish and Govern Transboundary Conserva(on Ini(a(ves
 HANDS ACROSS BORDERS An International Workshop on Transboundary Conservation Alterna(ve Mechanisms to Establish and Govern Transboundary Conserva(on Ini(a(ves Michael Schoon School of Sustainability Arizona
HANDS ACROSS BORDERS An International Workshop on Transboundary Conservation Alterna(ve Mechanisms to Establish and Govern Transboundary Conserva(on Ini(a(ves Michael Schoon School of Sustainability Arizona
Computational Social Choice: Spring 2007
 Computational Social Choice: Spring 2007 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today This lecture will be an introduction to voting
Computational Social Choice: Spring 2007 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today This lecture will be an introduction to voting
arxiv: v5 [cs.gt] 21 Jun 2014
![arxiv: v5 [cs.gt] 21 Jun 2014 arxiv: v5 [cs.gt] 21 Jun 2014](/thumbs/94/118062164.jpg) Schulze and Ranked-Pairs Voting Are Fixed-Parameter Tractable to Bribe, Manipulate, and Control arxiv:1210.6963v5 [cs.gt] 21 Jun 2014 Lane A. Hemaspaandra, Rahman Lavaee Department of Computer Science
Schulze and Ranked-Pairs Voting Are Fixed-Parameter Tractable to Bribe, Manipulate, and Control arxiv:1210.6963v5 [cs.gt] 21 Jun 2014 Lane A. Hemaspaandra, Rahman Lavaee Department of Computer Science
Sector Discrimination: Sector Identification with Similarity Digest Fingerprints
 Sector Discrimination: Sector Identification with Similarity Digest Fingerprints Vassil Roussev vassil@cs.uno.edu 1 Problem: given a set of fragments, iden4fy the original ar4fact. Source objects (files)
Sector Discrimination: Sector Identification with Similarity Digest Fingerprints Vassil Roussev vassil@cs.uno.edu 1 Problem: given a set of fragments, iden4fy the original ar4fact. Source objects (files)
Randomized Pursuit-Evasion in Graphs
 Randomized Pursuit-Evasion in Graphs Micah Adler, Harald Räcke ¾, Naveen Sivadasan, Christian Sohler ¾, and Berthold Vöcking ¾ Department of Computer Science University of Massachusetts, Amherst, micah@cs.umass.edu
Randomized Pursuit-Evasion in Graphs Micah Adler, Harald Räcke ¾, Naveen Sivadasan, Christian Sohler ¾, and Berthold Vöcking ¾ Department of Computer Science University of Massachusetts, Amherst, micah@cs.umass.edu
ÔÖ Î µ ÛÖ Î Ø Ø Ó ÚÖØ ÖÔ Ø Ø Ó º ØØ Û Ö ÚÒ Ø Ò Ú ¼ ½ Ú ½ ¾ Ú ¾ Ú Ú ½ ÒÒ ÙÒØÓÒ Eº ÏÐ Ò Ø ÖÔ ÕÙÒ Ú ÛÖ Ú ¼ Ú ¾ Î ½ ¾ Ò E µ Ú ½ Ú º Ì ÛÐ ÐÓ Ø Ö Ø Ò Ð Ø ÚÖ
 ÙÐÖÒ ÖÔ ÔÖ Î µ ÛÖ Î Ø Ø Ó ÚÖØ ÖÔ Ø Ø Ó º ØØ Û Ö ÚÒ Ø Ò Ú ¼ ½ Ú ½ ¾ Ú ¾ Ú Ú ½ ÒÒ ÙÒØÓÒ Eº ÏÐ Ò Ø ÖÔ ÕÙÒ Ú ÛÖ Ú ¼ Ú ¾ Î ½ ¾ Ò E µ Ú ½ Ú º Ì ÛÐ ÐÓ Ø Ö Ø Ò Ð Ø ÚÖØ ÓÒº ÈØ ÛÐ ÛÖ ÚÖÝ ÚÖØÜ ÓÙÖ Ø ÑÓ Ø ÓÒº ÝÐ ÐÓ
ÙÐÖÒ ÖÔ ÔÖ Î µ ÛÖ Î Ø Ø Ó ÚÖØ ÖÔ Ø Ø Ó º ØØ Û Ö ÚÒ Ø Ò Ú ¼ ½ Ú ½ ¾ Ú ¾ Ú Ú ½ ÒÒ ÙÒØÓÒ Eº ÏÐ Ò Ø ÖÔ ÕÙÒ Ú ÛÖ Ú ¼ Ú ¾ Î ½ ¾ Ò E µ Ú ½ Ú º Ì ÛÐ ÐÓ Ø Ö Ø Ò Ð Ø ÚÖØ ÓÒº ÈØ ÛÐ ÛÖ ÚÖÝ ÚÖØÜ ÓÙÖ Ø ÑÓ Ø ÓÒº ÝÐ ÐÓ
Are Friends Overrated? A Study for the Social News Aggregator Digg.com
 Are Friends Overrated? A Study for the Social News Aggregator Digg.com Chris>an Doerr, Norbert Blenn, Siyu Tang, Piet Van Mieghem TU DelG, Mekelweg 4, 2628CD DelG, The Netherlands {C.Doerr, N.Blenn, S.Tang,
Are Friends Overrated? A Study for the Social News Aggregator Digg.com Chris>an Doerr, Norbert Blenn, Siyu Tang, Piet Van Mieghem TU DelG, Mekelweg 4, 2628CD DelG, The Netherlands {C.Doerr, N.Blenn, S.Tang,
A Network Theory of Military Alliances
 A Network Theory of Military Alliances Yuke Li April 12, 214 Abstract This paper introduces network game theory into the study of international relations and specifically, military alliances. Using concepts
A Network Theory of Military Alliances Yuke Li April 12, 214 Abstract This paper introduces network game theory into the study of international relations and specifically, military alliances. Using concepts
A Calculus for End-to-end Statistical Service Guarantees
 A Calculus for End-to-end Statistical Service Guarantees Technical Report: University of Virginia, CS-2001-19 (2nd revised version) Almut Burchard Ý Jörg Liebeherr Stephen Patek Ý Department of Mathematics
A Calculus for End-to-end Statistical Service Guarantees Technical Report: University of Virginia, CS-2001-19 (2nd revised version) Almut Burchard Ý Jörg Liebeherr Stephen Patek Ý Department of Mathematics
