A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset
|
|
|
- Horatio Reynolds
- 5 years ago
- Views:
Transcription
1 A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset Sisi Xiong*, Feiyi Wang + and Qing Cao* *University of Tennessee Knoxville, Knoxville, TN, USA + Oak Ridge National Laboratory, Oak Ridge, TN, USA 1
2 Data integrity check n Motivations Ø Silent data corruption Ø Data movement n Checksumming Ø Generate a signature for a dataset 0x23ac After 3 months 0x23ac Dataset 1 Dataset 1 0x23ac After movement 0x4abf Dataset 1 Dataset 2 2
3 Scalability n Traditional approaches Ø Serial and file based n File distribution on Spider 2* Ø 50 million directories, half a billion files *Feiyi Wang, Veronica G. Vergara Larrea, Dustin Leverman, Sarp Oral. FCP: A Fast and Scalable Data Copy Tool for High Performance Parallel File Systems 3
4 Design goals n Develop a parallel checksumming tool Ø Use multiple processes/hosts to achieve horizontal scaling n Generate signatures for large-scale datasets Ø A two-step task: l Generate a signature for each file l Aggregate all the file-level signatures to a dataset-level signature n The resulting design: fsum 4
5 File-level signature vs chunk-level signature n Increase parallelism: break files into chunks File A Chunk0(fileA, 0) Chunk1(fileA, 4MiB) Chunking Chunk2(fileA, 8MiB) Chunk3(fileA, 12MiB) Chunk4(fileA, 16MiB) Chunk5(fileA, 20MiB) Chunk size: 4MiB 5
6 Workload distribution n Work stealing pattern Ø An idle process sends out work request Ø A busy process distributes its work queue equally P0: P1: P2: P3: Work queue split P0: P1: P2: P3: P0: P1: P2: P3: Work queue split P0: P1: P2: P3: work processing 6
7 Work stealing pattern n Random work distribution Ø Same/different number of processes 7
8 Aggregation of chunk-level signatures n Two possible solutions: Ø Hash list Ø Merkle tree: hash tree n Sorting is necessary! Hash list 1 s0 s1 s2 s3 s4 s5 s6 s7 Hash list 2 s4 s1 s3 s7 s2 s5 s6 s0 a6 b6 a4 a5 b4 b5 a0 a1 a2 a3 b0 b1 b2 b3 s0 s1 s2 s3 s4 s5 s6 s7 s4 s1 s3 s7 s2 s5 s6 s0 Hash tree1 Hash tree2 8
9 Bloom filter based signature aggregation approach n Bloom filter Ø An array of bits, initialized to all 0s Ø Check membership Ø Two operations: insert and query n Configuration parameters Ø Size: m Ø Number of hash functions: k m=10, k= Insert{a,b} Query{a,c} a In the set! b c Not In the in set the! set! False positive error 9
10 Bloom filter based signature aggregation approach n Probabilistic nature: errors Ø False negative error never happens Ø False positive error - with a probability p: l m: bloom filter size, n: number of elements l Given n, larger m results in a smaller p. l Give p, m increases linearly with respect to n p = e %& ' ()* +)- ln p m = n (ln 2) + 10
11 Bloom filter based signature aggregation approach n Features Ø Independent of insertion orders {A, B, C, D, E} insert {E, D, C, B, A} insert Ø Use OR result to represent the union of multiple sets {A, B, C} {D, E} insert insert OR {A, B, C, D, E} 11
12 Bloom filter based signature aggregation approach n P0: {(file1chunk1, s), (file2chunk2, s), (file2chunk3, s), (file3chunk2, s)} n P1: {(file1chunk2, s), (file1chunk3, s), (file2chunk1, s), (file3chunk4, s)} n P2: {(file1chunk4, s), (file1chunk6, s), (file2chunk6, s), (file3chunk3, s)} n P3: {(file1chunk5, s), (file2chunk4, s), (file2chunk5, s), (file3chunk1, s)} n OR result 12
13 Bloom filter based signature aggregation approach n Parameter setting and error probability Ø Error case: two different datasets have the same signature Ø Suppose there are r different signatures l C 5 = {x 5, x +,, x :, c :, c :<5,, c ' } l C + = {y 5, y +,, y :, c :, c :<5,, c ' } l Given r, the error probability is p +:, p is false positive probability of bloom filter Ø Worst case: r = 1 l Number of errors follows a binomial distribution e~b(n, p + ) l P e = 0 = (1 p + ) ' l p = e %D E ()* +)- l The relationship between P(e=0) and m/n 13
14 Evaluation n Two datasets Ø Scientific datasets generated on Spider 2 Dataset 1 Dataset 2 Total size 5.39TiB 14.74TiB Number of files 28,114,281 15,590 Average file size KiB 1.19GiB Chunk size 16MiB 64MiB Number of chunks 28,343, ,629 14
15 Evaluation n Scalability test Ø Higher process rate when using more processes, until bounded by I/O bandwidth Ø Handling large files is more efficient than handling small files, potentially bounded by metadata retrieval in Lustre file system Processing time Processing rate 15
16 Evaluation n Function verification Ø Corrupt the dataset l 100 times, corrupt a single byte in a single file each time Ø Compare two signatures of the original and the corrupted dataset Ø Results: all the signatures are different 16
17 Evaluation n Compare with related approaches 5.8x 2.6x 7.1x 4.4x Memory usage compared with sorting (P(e=0) = 99.99%) Runtime compared with sha1 (a 500GiB file, 4 processes) 17
18 Conclusions n Present the design and implementation of scalable parallel checksumming tool, fsum, for large scale datasets n Design a bloom filter based signature aggregation approach and analyze the relationship between error probability and parameter selection n Test on representative and real production datasets and demonstrate that fsum exhibits near-linear scalability and is able to detect data corruption n fsum is both memory and time efficient than other approaches Code available at github.com/olcf/pcircle 18
19 Thanks! 19
File Systems: Fundamentals
 File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
Last Time. Bit banged SPI I2C LIN Ethernet. u Embedded networks. Ø Characteristics Ø Requirements Ø Simple embedded LANs
 Last Time u Embedded networks Ø Characteristics Ø Requirements Ø Simple embedded LANs Bit banged SPI I2C LIN Ethernet Today u CAN Bus Ø Intro Ø Low-level stuff Ø Frame types Ø Arbitration Ø Filtering Ø
Last Time u Embedded networks Ø Characteristics Ø Requirements Ø Simple embedded LANs Bit banged SPI I2C LIN Ethernet Today u CAN Bus Ø Intro Ø Low-level stuff Ø Frame types Ø Arbitration Ø Filtering Ø
Comparison Sorts. EECS 2011 Prof. J. Elder - 1 -
 Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
CS 5523: Operating Systems
 Lecture1: OS Overview CS 5523: Operating Systems Instructor: Dr Tongping Liu Midterm Exam: Oct 2, 2017, Monday 7:20pm 8:45pm Operating System: what is it?! Evolution of Computer Systems and OS Concepts
Lecture1: OS Overview CS 5523: Operating Systems Instructor: Dr Tongping Liu Midterm Exam: Oct 2, 2017, Monday 7:20pm 8:45pm Operating System: what is it?! Evolution of Computer Systems and OS Concepts
Random Forests. Gradient Boosting. and. Bagging and Boosting
 Random Forests and Gradient Boosting Bagging and Boosting The Bootstrap Sample and Bagging Simple ideas to improve any model via ensemble Bootstrap Samples Ø Random samples of your data with replacement
Random Forests and Gradient Boosting Bagging and Boosting The Bootstrap Sample and Bagging Simple ideas to improve any model via ensemble Bootstrap Samples Ø Random samples of your data with replacement
Swiss E-Voting Workshop 2010
 Swiss E-Voting Workshop 2010 Verifiability in Remote Voting Systems September 2010 Jordi Puiggali VP Research & Development Jordi.Puiggali@scytl.com Index Auditability in e-voting Types of verifiability
Swiss E-Voting Workshop 2010 Verifiability in Remote Voting Systems September 2010 Jordi Puiggali VP Research & Development Jordi.Puiggali@scytl.com Index Auditability in e-voting Types of verifiability
Maps and Hash Tables. EECS 2011 Prof. J. Elder - 1 -
 Maps and Hash Tables - 1 - Outline Ø Maps Ø Hashing Ø Multimaps Ø Ordered Maps - 2 - Learning Outcomes Ø By understanding this lecture, you should be able to: Ø Outline the ADT for a map and a multimap
Maps and Hash Tables - 1 - Outline Ø Maps Ø Hashing Ø Multimaps Ø Ordered Maps - 2 - Learning Outcomes Ø By understanding this lecture, you should be able to: Ø Outline the ADT for a map and a multimap
A Micro-Benchmark Evaluation of Catamount and Cray Linux Environment (CLE) Performance
 A Micro-Benchmark Evaluation of Catamount and Cray Linux Environment (CLE) Performance Jeff Larkin Cray Inc. Jeff Kuehn ORNL Does CLE waddle like a penguin, or run like
A Micro-Benchmark Evaluation of Catamount and Cray Linux Environment (CLE) Performance Jeff Larkin Cray Inc. Jeff Kuehn ORNL Does CLE waddle like a penguin, or run like
Maps, Hash Tables and Dictionaries
 Maps, Hash Tables and Dictionaries Chapter 9-1 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 2 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 3 -
Maps, Hash Tables and Dictionaries Chapter 9-1 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 2 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 3 -
Midterm Review. EECS 2011 Prof. J. Elder - 1 -
 Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
The Social Web: Social networks, tagging and what you can learn from them. Kristina Lerman USC Information Sciences Institute
 The Social Web: Social networks, tagging and what you can learn from them Kristina Lerman USC Information Sciences Institute The Social Web The Social Web is a collection of technologies, practices and
The Social Web: Social networks, tagging and what you can learn from them Kristina Lerman USC Information Sciences Institute The Social Web The Social Web is a collection of technologies, practices and
CS 5523 Operating Systems: Intro to Distributed Systems
 CS 5523 Operating Systems: Intro to Distributed Systems Instructor: Dr. Tongping Liu Thank Dr. Dakai Zhu, Dr. Palden Lama for providing their slides. Outline Different Distributed Systems Ø Distributed
CS 5523 Operating Systems: Intro to Distributed Systems Instructor: Dr. Tongping Liu Thank Dr. Dakai Zhu, Dr. Palden Lama for providing their slides. Outline Different Distributed Systems Ø Distributed
Lecture 6 Cryptographic Hash Functions
 Lecture 6 Cryptographic Hash Functions 1 Purpose Ø CHF one of the most important tools in modern cryptography and security Ø In crypto, CHF instantiates a Random Oracle paradigm Ø In security, used in
Lecture 6 Cryptographic Hash Functions 1 Purpose Ø CHF one of the most important tools in modern cryptography and security Ø In crypto, CHF instantiates a Random Oracle paradigm Ø In security, used in
Sector Discrimination: Sector Identification with Similarity Digest Fingerprints
 Sector Discrimination: Sector Identification with Similarity Digest Fingerprints Vassil Roussev vassil@cs.uno.edu 1 Problem: given a set of fragments, iden4fy the original ar4fact. Source objects (files)
Sector Discrimination: Sector Identification with Similarity Digest Fingerprints Vassil Roussev vassil@cs.uno.edu 1 Problem: given a set of fragments, iden4fy the original ar4fact. Source objects (files)
Analysis of the Reputation System and User Contributions on a Question Answering Website: StackOverflow
 Analysis of the Reputation System and User Contributions on a Question Answering Website: StackOverflow Dana Movshovitz-Attias Yair Movshovitz-Attias Peter Steenkiste Christos Faloutsos August 27, 2013
Analysis of the Reputation System and User Contributions on a Question Answering Website: StackOverflow Dana Movshovitz-Attias Yair Movshovitz-Attias Peter Steenkiste Christos Faloutsos August 27, 2013
Optimization Strategies
 Global Memory Access Pattern and Control Flow Objectives Ø Ø Global Memory Access Pattern (Coalescing) Ø Control Flow (Divergent branch) Copyright 2013 by Yong Cao, Referencing UIUC ECE498AL Course Notes
Global Memory Access Pattern and Control Flow Objectives Ø Ø Global Memory Access Pattern (Coalescing) Ø Control Flow (Divergent branch) Copyright 2013 by Yong Cao, Referencing UIUC ECE498AL Course Notes
Combating Friend Spam Using Social Rejections
 Combating Friend Spam Using Social Rejections Qiang Cao Duke University Michael Sirivianos Xiaowei Yang Kamesh Munagala Cyprus Univ. of Technology Duke University Duke University Friend Spam in online
Combating Friend Spam Using Social Rejections Qiang Cao Duke University Michael Sirivianos Xiaowei Yang Kamesh Munagala Cyprus Univ. of Technology Duke University Duke University Friend Spam in online
Priority Queues & Heaps
 Priority Queues & Heaps Chapter 8-1 - The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List
Priority Queues & Heaps Chapter 8-1 - The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List
Concurrent Programing: Why you should care, deeply. Don Porter Portions courtesy Emmett Witchel
 Concurrent Programing: Why you should care, deeply Don Porter Portions courtesy Emmett Witchel 1 Uniprocessor Performance Not Scaling Performance (vs. VAX-11/780) 10000 1000 100 10 1 20% /year 52% /year
Concurrent Programing: Why you should care, deeply Don Porter Portions courtesy Emmett Witchel 1 Uniprocessor Performance Not Scaling Performance (vs. VAX-11/780) 10000 1000 100 10 1 20% /year 52% /year
Support Vector Machines
 Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Colorado Secretary of State Election Rules [8 CCR ]
![Colorado Secretary of State Election Rules [8 CCR ] Colorado Secretary of State Election Rules [8 CCR ]](/thumbs/78/78717657.jpg) Rule 25. Post-election audit 25.1 Definitions. As used in this rule, unless stated otherwise: 25.1.1 Audit Center means the page or pages of the Secretary of State s website devoted to risk-limiting audits.
Rule 25. Post-election audit 25.1 Definitions. As used in this rule, unless stated otherwise: 25.1.1 Audit Center means the page or pages of the Secretary of State s website devoted to risk-limiting audits.
Probabilistic Latent Semantic Analysis Hofmann (1999)
 Probabilistic Latent Semantic Analysis Hofmann (1999) Presenter: Mercè Vintró Ricart February 8, 2016 Outline Background Topic models: What are they? Why do we use them? Latent Semantic Analysis (LSA)
Probabilistic Latent Semantic Analysis Hofmann (1999) Presenter: Mercè Vintró Ricart February 8, 2016 Outline Background Topic models: What are they? Why do we use them? Latent Semantic Analysis (LSA)
UNITED STATES [DISTRICT/BANKRUPTCY] COURT FOR THE DISTRICT OF DIVISION., ) ) Plaintiff, ) ) vs. ) Case No. ), ) Judge ) Defendant.
![UNITED STATES [DISTRICT/BANKRUPTCY] COURT FOR THE DISTRICT OF DIVISION., ) ) Plaintiff, ) ) vs. ) Case No. ), ) Judge ) Defendant. UNITED STATES [DISTRICT/BANKRUPTCY] COURT FOR THE DISTRICT OF DIVISION., ) ) Plaintiff, ) ) vs. ) Case No. ), ) Judge ) Defendant.](/thumbs/72/66639571.jpg) UNITED STATES [DISTRICT/BANKRUPTCY] COURT FOR THE DISTRICT OF DIVISION, Plaintiff, vs. Case No., Judge Defendant. [PROPOSED] STANDING ORDER RELATING TO THE DISCOVERY OF ELECTRONICALLY STORED INFORMATION
UNITED STATES [DISTRICT/BANKRUPTCY] COURT FOR THE DISTRICT OF DIVISION, Plaintiff, vs. Case No., Judge Defendant. [PROPOSED] STANDING ORDER RELATING TO THE DISCOVERY OF ELECTRONICALLY STORED INFORMATION
Estonian National Electoral Committee. E-Voting System. General Overview
 Estonian National Electoral Committee E-Voting System General Overview Tallinn 2005-2010 Annotation This paper gives an overview of the technical and organisational aspects of the Estonian e-voting system.
Estonian National Electoral Committee E-Voting System General Overview Tallinn 2005-2010 Annotation This paper gives an overview of the technical and organisational aspects of the Estonian e-voting system.
Chapter. Sampling Distributions Pearson Prentice Hall. All rights reserved
 Chapter 8 Sampling Distributions 2010 Pearson Prentice Hall. All rights reserved Section 8.1 Distribution of the Sample Mean 2010 Pearson Prentice Hall. All rights reserved Objectives 1. Describe the distribution
Chapter 8 Sampling Distributions 2010 Pearson Prentice Hall. All rights reserved Section 8.1 Distribution of the Sample Mean 2010 Pearson Prentice Hall. All rights reserved Objectives 1. Describe the distribution
ECE250: Algorithms and Data Structures Trees
 ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
Contents. Bibliography 121. Index 123
 Contents 5 Advanced Data Types page 2 5.1 Sparse Arrays: Dictionary Arrays, Hashing Arrays, and Maps 2 5.2 The Implementation of the Data Type Map 14 5.3 Dictionaries and Sets 27 5.4 Priority Queues 28
Contents 5 Advanced Data Types page 2 5.1 Sparse Arrays: Dictionary Arrays, Hashing Arrays, and Maps 2 5.2 The Implementation of the Data Type Map 14 5.3 Dictionaries and Sets 27 5.4 Priority Queues 28
Digital humanities methods in comparative law
 Thomas Favre-Bulle thomas.favre-bulle@epfl.ch July 18, 2014 JurisDiversitas Annual Meeting 2015, Aix-en-Provence Digital humanities methods in comparative law Quantitative analysis on a plain text corpus
Thomas Favre-Bulle thomas.favre-bulle@epfl.ch July 18, 2014 JurisDiversitas Annual Meeting 2015, Aix-en-Provence Digital humanities methods in comparative law Quantitative analysis on a plain text corpus
Learning Systems. Research at the Intersection of Machine Learning & Data Systems. Joseph E. Gonzalez
 Learning Systems Research at the Intersection of Machine Learning & Data Systems Joseph E. Gonzalez Asst. Professor, UC Berkeley jegonzal@cs.berkeley.edu How can machine learning techniques be used to
Learning Systems Research at the Intersection of Machine Learning & Data Systems Joseph E. Gonzalez Asst. Professor, UC Berkeley jegonzal@cs.berkeley.edu How can machine learning techniques be used to
Running head: ROCK THE BLOCKCHAIN 1. Rock the Blockchain: Next Generation Voting. Nikolas Roby, Patrick Gill, Michael Williams
 Running head: ROCK THE BLOCKCHAIN 1 Rock the Blockchain: Next Generation Voting Nikolas Roby, Patrick Gill, Michael Williams University of Maryland University College (UMUC) Author Note Thanks to our UMUC
Running head: ROCK THE BLOCKCHAIN 1 Rock the Blockchain: Next Generation Voting Nikolas Roby, Patrick Gill, Michael Williams University of Maryland University College (UMUC) Author Note Thanks to our UMUC
United States District Court, D. Delaware. LUCENT TECHNOLOGIES, INC. Plaintiff. v. NEWBRIDGE NETWORKS CORP. and Newbridge Networks, Inc. Defendants.
 United States District Court, D. Delaware. LUCENT TECHNOLOGIES, INC. Plaintiff. v. NEWBRIDGE NETWORKS CORP. and Newbridge Networks, Inc. Defendants. No. 97-347-JJF Sept. 21, 2001. Action was brought alleging
United States District Court, D. Delaware. LUCENT TECHNOLOGIES, INC. Plaintiff. v. NEWBRIDGE NETWORKS CORP. and Newbridge Networks, Inc. Defendants. No. 97-347-JJF Sept. 21, 2001. Action was brought alleging
SECURE REMOTE VOTER REGISTRATION
 SECURE REMOTE VOTER REGISTRATION August 2008 Jordi Puiggali VP Research & Development Jordi.Puiggali@scytl.com Index Voter Registration Remote Voter Registration Current Systems Problems in the Current
SECURE REMOTE VOTER REGISTRATION August 2008 Jordi Puiggali VP Research & Development Jordi.Puiggali@scytl.com Index Voter Registration Remote Voter Registration Current Systems Problems in the Current
Protocol to Check Correctness of Colorado s Risk-Limiting Tabulation Audit
 1 Public RLA Oversight Protocol Stephanie Singer and Neal McBurnett, Free & Fair Copyright Stephanie Singer and Neal McBurnett 2018 Version 1.0 One purpose of a Risk-Limiting Tabulation Audit is to improve
1 Public RLA Oversight Protocol Stephanie Singer and Neal McBurnett, Free & Fair Copyright Stephanie Singer and Neal McBurnett 2018 Version 1.0 One purpose of a Risk-Limiting Tabulation Audit is to improve
THE ECONOMIC EFFECT OF CORRUPTION IN ITALY: A REGIONAL PANEL ANALYSIS (M. LISCIANDRA & E. MILLEMACI) APPENDIX A: CORRUPTION CRIMES AND GROWTH RATES
 THE ECONOMIC EFFECT OF CORRUPTION IN ITALY: A REGIONAL PANEL ANALYSIS (M. LISCIANDRA & E. MILLEMACI) APPENDIX A: CORRUPTION CRIMES AND GROWTH RATES Figure A1 shows an apparently negative correlation between
THE ECONOMIC EFFECT OF CORRUPTION IN ITALY: A REGIONAL PANEL ANALYSIS (M. LISCIANDRA & E. MILLEMACI) APPENDIX A: CORRUPTION CRIMES AND GROWTH RATES Figure A1 shows an apparently negative correlation between
Exploring QR Factorization on GPU for Quantum Monte Carlo Simulation
 Exploring QR Factorization on GPU for Quantum Monte Carlo Simulation Tyler McDaniel Ming Wong Mentors: Ed D Azevedo, Ying Wai Li, Kwai Wong Quantum Monte Carlo Simulation Slater Determinant for N-electrons
Exploring QR Factorization on GPU for Quantum Monte Carlo Simulation Tyler McDaniel Ming Wong Mentors: Ed D Azevedo, Ying Wai Li, Kwai Wong Quantum Monte Carlo Simulation Slater Determinant for N-electrons
Non-Binding Trusted Party Consortium Agreement. Accession Agreement. ASERL-GWLA Consortium Membership v
 Accession Agreement This Accession Agreement (the Accession Agreement ) is entered into by and between ORCID, Inc., a Delaware nonstock corporation located at 10411 Motor City Drive, Suite 750, Bethesda,
Accession Agreement This Accession Agreement (the Accession Agreement ) is entered into by and between ORCID, Inc., a Delaware nonstock corporation located at 10411 Motor City Drive, Suite 750, Bethesda,
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Cloud Tutorial: AWS IoT. TA for class CSE 521S, Fall, Jan/18/2018 Haoran Li
 Cloud Tutorial: AWS IoT TA for class CSE 521S, Fall, Jan/18/2018 Haoran Li Pointers Ø Amazon IoT q http://docs.aws.amazon.com/iot/latest/developerguide/what-isaws-iot.html Ø Amazon EC2 q http://docs.aws.amazon.com/awsec2/latest/userguide/
Cloud Tutorial: AWS IoT TA for class CSE 521S, Fall, Jan/18/2018 Haoran Li Pointers Ø Amazon IoT q http://docs.aws.amazon.com/iot/latest/developerguide/what-isaws-iot.html Ø Amazon EC2 q http://docs.aws.amazon.com/awsec2/latest/userguide/
GST 104: Cartographic Design Lab 6: Countries with Refugees and Internally Displaced Persons Over 1 Million Map Design
 GST 104: Cartographic Design Lab 6: Countries with Refugees and Internally Displaced Persons Over 1 Million Map Design Objective Utilize QGIS and Inkscape to Design a Chorolpleth Map Showing Refugees and
GST 104: Cartographic Design Lab 6: Countries with Refugees and Internally Displaced Persons Over 1 Million Map Design Objective Utilize QGIS and Inkscape to Design a Chorolpleth Map Showing Refugees and
Testing the Waters: Working With CSS Data in Congressional Collections
 Electronic Records Case Studies Series Congressional Papers Roundtable Society of American Archivists Testing the Waters: Working With CSS Data in Congressional Collections Natalie Bond University of Montana
Electronic Records Case Studies Series Congressional Papers Roundtable Society of American Archivists Testing the Waters: Working With CSS Data in Congressional Collections Natalie Bond University of Montana
Classifier Evaluation and Selection. Review and Overview of Methods
 Classifier Evaluation and Selection Review and Overview of Methods Things to consider Ø Interpretation vs. Prediction Ø Model Parsimony vs. Model Error Ø Type of prediction task: Ø Decisions Interested
Classifier Evaluation and Selection Review and Overview of Methods Things to consider Ø Interpretation vs. Prediction Ø Model Parsimony vs. Model Error Ø Type of prediction task: Ø Decisions Interested
7th CIRCUIT ELECTRONIC DISCOVERY COMMITTEE PRINCIPLES RELATING TO THE DISCOVERY OF ELECTRONICALLY STORED INFORMATION. Second Edition, January, 2018
 General Principles Principle 1.01 (Purpose) 7th CIRCUIT ELECTRONIC DISCOVERY COMMITTEE PRINCIPLES RELATING TO THE DISCOVERY OF ELECTRONICALLY STORED INFORMATION Second Edition, January, 2018 The purpose
General Principles Principle 1.01 (Purpose) 7th CIRCUIT ELECTRONIC DISCOVERY COMMITTEE PRINCIPLES RELATING TO THE DISCOVERY OF ELECTRONICALLY STORED INFORMATION Second Edition, January, 2018 The purpose
Midterm Review. EECS 2011 Prof. J. Elder - 1 -
 Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Understanding factors that influence L1-visa outcomes in US
 Understanding factors that influence L1-visa outcomes in US By Nihar Dalmia, Meghana Murthy and Nianthrini Vivekanandan Link to online course gallery : https://www.ischool.berkeley.edu/projects/2017/understanding-factors-influence-l1-work
Understanding factors that influence L1-visa outcomes in US By Nihar Dalmia, Meghana Murthy and Nianthrini Vivekanandan Link to online course gallery : https://www.ischool.berkeley.edu/projects/2017/understanding-factors-influence-l1-work
Paper: Entered: January 16, 2018 UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE PATENT TRIAL AND APPEAL BOARD
 Trials@uspto.gov Paper: 11 571-272-7822 Entered: January 16, 2018 UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE PATENT TRIAL AND APPEAL BOARD LIVE NATION ENTERTAINMENT, INC., Petitioner, v. COMPLETE
Trials@uspto.gov Paper: 11 571-272-7822 Entered: January 16, 2018 UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE PATENT TRIAL AND APPEAL BOARD LIVE NATION ENTERTAINMENT, INC., Petitioner, v. COMPLETE
General Framework of Electronic Voting and Implementation thereof at National Elections in Estonia
 State Electoral Office of Estonia General Framework of Electronic Voting and Implementation thereof at National Elections in Estonia Document: IVXV-ÜK-1.0 Date: 20 June 2017 Tallinn 2017 Annotation This
State Electoral Office of Estonia General Framework of Electronic Voting and Implementation thereof at National Elections in Estonia Document: IVXV-ÜK-1.0 Date: 20 June 2017 Tallinn 2017 Annotation This
Real-Time Scheduling Single Processor. Chenyang Lu
 Real-Time Scheduling Single Processor Chenyang Lu Critiques Ø 1/2 page critiques of research papers. q Back-of-envelop comments - NOT whole essays. q Guidelines: http://www.cs.wustl.edu/%7elu/cse521s/critique.html
Real-Time Scheduling Single Processor Chenyang Lu Critiques Ø 1/2 page critiques of research papers. q Back-of-envelop comments - NOT whole essays. q Guidelines: http://www.cs.wustl.edu/%7elu/cse521s/critique.html
Samiah Ibrahim. Canada Border Services Agency
 Forensic document examination for evidence of identity Samiah Ibrahim Manager, Forensic Document Examination Canada Border Services Agency What do we do? Forensic Document Examination is the: Objective
Forensic document examination for evidence of identity Samiah Ibrahim Manager, Forensic Document Examination Canada Border Services Agency What do we do? Forensic Document Examination is the: Objective
IBM Cognos Open Mic Cognos Analytics 11 Part nd June, IBM Corporation
 IBM Cognos Open Mic Cognos Analytics 11 Part 2 22 nd June, 2016 IBM Cognos Open MIC Team Deepak Giri Presenter Subhash Kothari Technical Panel Member Chakravarthi Mannava Technical Panel Member 2 Agenda
IBM Cognos Open Mic Cognos Analytics 11 Part 2 22 nd June, 2016 IBM Cognos Open MIC Team Deepak Giri Presenter Subhash Kothari Technical Panel Member Chakravarthi Mannava Technical Panel Member 2 Agenda
Follow this and additional works at:
 University of Tennessee, Knoxville Trace: Tennessee Research and Creative Exchange Tennessee Department of State, Opinions from the Administrative Procedures Division Law 10-13-2009 TENNESSEE DEPARTMENT
University of Tennessee, Knoxville Trace: Tennessee Research and Creative Exchange Tennessee Department of State, Opinions from the Administrative Procedures Division Law 10-13-2009 TENNESSEE DEPARTMENT
IceCube Project Monthly Report November 2007
 Accomplishments IceCube Project Monthly Report November 2007 Completed the commissioning of the IceCube Seasonal Equipment Site in preparations for drilling. Started deep ice drilling on December 5 following
Accomplishments IceCube Project Monthly Report November 2007 Completed the commissioning of the IceCube Seasonal Equipment Site in preparations for drilling. Started deep ice drilling on December 5 following
Measures for Consular Legalization
 Decree of the Ministry of Foreign Affairs of the People's Republic of China No. 2 Measures for Consular Legalization, approved by the State Council on November 6,2015,is hereby promulgated and shall come
Decree of the Ministry of Foreign Affairs of the People's Republic of China No. 2 Measures for Consular Legalization, approved by the State Council on November 6,2015,is hereby promulgated and shall come
Analysis of Social Voting Patterns on Digg
 Analysis of Social Voting Patterns on Digg Kristina Lerman Aram Galstyan USC Information Sciences Institute {lerman,galstyan}@isi.edu Content, content everywhere and not a drop to read Explosion of user-generated
Analysis of Social Voting Patterns on Digg Kristina Lerman Aram Galstyan USC Information Sciences Institute {lerman,galstyan}@isi.edu Content, content everywhere and not a drop to read Explosion of user-generated
Introduction-cont Pattern classification
 How are people identified? Introduction-cont Pattern classification Biometrics CSE 190-a Lecture 2 People are identified by three basic means: Something they have (identity document or token) Something
How are people identified? Introduction-cont Pattern classification Biometrics CSE 190-a Lecture 2 People are identified by three basic means: Something they have (identity document or token) Something
Draft rules issued for comment on July 20, Ballot cast should be when voter relinquishes control of a marked, sealed ballot.
 Draft rules issued for comment on July 20, 2016. Public Comment: Proposed Commenter Comment Department action Rule 1.1.8 Kolwicz Ballot cast should be when voter relinquishes control of a marked, sealed
Draft rules issued for comment on July 20, 2016. Public Comment: Proposed Commenter Comment Department action Rule 1.1.8 Kolwicz Ballot cast should be when voter relinquishes control of a marked, sealed
The bill now must pass the Senate. We hope that will be the case later this year.
 On July 21, 2014, Fanny and I journeyed to, to explore the future Manhattan Project National Historical Park potential sites there. I had explored the Los Alamos, NM, potential sites and the Los Alamos
On July 21, 2014, Fanny and I journeyed to, to explore the future Manhattan Project National Historical Park potential sites there. I had explored the Los Alamos, NM, potential sites and the Los Alamos
Follow this and additional works at:
 University of Tennessee, Knoxville Trace: Tennessee Research and Creative Exchange Tennessee Department of State, Opinions from the Administrative Procedures Division Law 9-24-2008 TENNESSEE DEPARTMENT
University of Tennessee, Knoxville Trace: Tennessee Research and Creative Exchange Tennessee Department of State, Opinions from the Administrative Procedures Division Law 9-24-2008 TENNESSEE DEPARTMENT
CASE STUDY 2 Portuguese Immigration & Border Service
 CASE STUDY 2 Portuguese Immigration & Border Service Page 1 Table of Contents EXECUTIVE SUMMARY... 3 1 CUSTOMER NAME... 4 2 BUSINESS CASE BUSINESS DRIVERS... 4 3 CHALLENGE... 4 4 SOLUTION DESCRIPTION...
CASE STUDY 2 Portuguese Immigration & Border Service Page 1 Table of Contents EXECUTIVE SUMMARY... 3 1 CUSTOMER NAME... 4 2 BUSINESS CASE BUSINESS DRIVERS... 4 3 CHALLENGE... 4 4 SOLUTION DESCRIPTION...
The HeLIx + inversion code Genetic algorithms. A. Lagg - Abisko Winter School 1
 The HeLIx + inversion code Genetic algorithms A. Lagg - Abisko Winter School 1 Inversion of the RTE Once solution of RTE is known: Ø comparison between Stokes spectra of synthetic and observed spectrum
The HeLIx + inversion code Genetic algorithms A. Lagg - Abisko Winter School 1 Inversion of the RTE Once solution of RTE is known: Ø comparison between Stokes spectra of synthetic and observed spectrum
Florida Supreme Court Standards for Electronic Access to the Courts
 Florida Supreme Court Standards for Electronic Access to the Courts Adopted June 2009 Adopted modifications August 2017 Version 18.0 TABLE OF CONTENTS 1.0. PORTAL TECHNOLOGY STANDARDS... 4 2.0 PORTAL FUNCTIONALITY...
Florida Supreme Court Standards for Electronic Access to the Courts Adopted June 2009 Adopted modifications August 2017 Version 18.0 TABLE OF CONTENTS 1.0. PORTAL TECHNOLOGY STANDARDS... 4 2.0 PORTAL FUNCTIONALITY...
what Flaws IN the PPWT? --THE WAY FORWARD FOR ARMS CONTROL IN OUTER SPACE
 ESPI-Space Security: Some Perspective what Flaws IN the PPWT? --THE WAY FORWARD FOR ARMS CONTROL IN OUTER SPACE Dr. Guoyu WANG Institute of Space Law Beijing Institute of Technology (BIT) China Vienna,
ESPI-Space Security: Some Perspective what Flaws IN the PPWT? --THE WAY FORWARD FOR ARMS CONTROL IN OUTER SPACE Dr. Guoyu WANG Institute of Space Law Beijing Institute of Technology (BIT) China Vienna,
Highlights of Fourth Annual Tulane University Report
 Highlights of Fourth Annual Tulane University Report On September 30, 2010, the Payson Center for International Development at Tulane University released its fourth annual report on Oversight of Public
Highlights of Fourth Annual Tulane University Report On September 30, 2010, the Payson Center for International Development at Tulane University released its fourth annual report on Oversight of Public
Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times
 Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
COMP : DATA STRUCTURES 2/27/14. Are binary trees satisfying two additional properties:
 BINARY HEAPS Two Additional Properties 9 Binary Heaps Are binary trees satisfying two additional properties: Ø Structure property: Levels are filled in order, left to right Also known as complete binary
BINARY HEAPS Two Additional Properties 9 Binary Heaps Are binary trees satisfying two additional properties: Ø Structure property: Levels are filled in order, left to right Also known as complete binary
Comparison of the Psychometric Properties of Several Computer-Based Test Designs for. Credentialing Exams
 CBT DESIGNS FOR CREDENTIALING 1 Running head: CBT DESIGNS FOR CREDENTIALING Comparison of the Psychometric Properties of Several Computer-Based Test Designs for Credentialing Exams Michael Jodoin, April
CBT DESIGNS FOR CREDENTIALING 1 Running head: CBT DESIGNS FOR CREDENTIALING Comparison of the Psychometric Properties of Several Computer-Based Test Designs for Credentialing Exams Michael Jodoin, April
MINUTES OF THE SENATE COMMITTEE ON JUDICIARY. Seventy-Eighth Session February 10, 2015
 MINUTES OF THE SENATE COMMITTEE ON JUDICIARY Seventy-Eighth Session The Senate Committee on Judiciary was called to order by Chair Greg Brower at 1:02 p.m. on Tuesday,, in Room 2134 of the Legislative
MINUTES OF THE SENATE COMMITTEE ON JUDICIARY Seventy-Eighth Session The Senate Committee on Judiciary was called to order by Chair Greg Brower at 1:02 p.m. on Tuesday,, in Room 2134 of the Legislative
Georg Lutz, Nicolas Pekari, Marina Shkapina. CSES Module 5 pre-test report, Switzerland
 Georg Lutz, Nicolas Pekari, Marina Shkapina CSES Module 5 pre-test report, Switzerland Lausanne, 8.31.2016 1 Table of Contents 1 Introduction 3 1.1 Methodology 3 2 Distribution of key variables 7 2.1 Attitudes
Georg Lutz, Nicolas Pekari, Marina Shkapina CSES Module 5 pre-test report, Switzerland Lausanne, 8.31.2016 1 Table of Contents 1 Introduction 3 1.1 Methodology 3 2 Distribution of key variables 7 2.1 Attitudes
Performance & Energy
 1 Performance & Energy Optimization @ Md Abdullah Shahneous Bari Abid M. Malik Millad Ghane Ahmad Qawasmeh Barbara M. Chapman 11/28/15 2 Layout of the talk Ø Overview Ø Motivation Ø Factors that affect
1 Performance & Energy Optimization @ Md Abdullah Shahneous Bari Abid M. Malik Millad Ghane Ahmad Qawasmeh Barbara M. Chapman 11/28/15 2 Layout of the talk Ø Overview Ø Motivation Ø Factors that affect
IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF PENNSYLVANIA
 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF PENNSYLVANIA Mahari Bailey, et al., : Plaintiffs : C.A. No. 10-5952 : v. : : City of Philadelphia, et al., : Defendants : PLAINTIFFS EIGHTH
IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF PENNSYLVANIA Mahari Bailey, et al., : Plaintiffs : C.A. No. 10-5952 : v. : : City of Philadelphia, et al., : Defendants : PLAINTIFFS EIGHTH
VITA. February Robert A. Nakosteen EDUCATION
 1 EDUCATION VITA February 2016 B.A. (Economics) University of Colorado M.A. (Economics) University of Michigan Ph.D. (Economics) University of Tennessee PROFESSIONAL EXPERIENCE: Professor, Isenberg School
1 EDUCATION VITA February 2016 B.A. (Economics) University of Colorado M.A. (Economics) University of Michigan Ph.D. (Economics) University of Tennessee PROFESSIONAL EXPERIENCE: Professor, Isenberg School
IDENTIFYING FAULT-PRONE MODULES IN SOFTWARE FOR DIAGNOSIS AND TREATMENT USING EEPORTERS CLASSIFICATION TREE
 IDENTIFYING FAULT-PRONE MODULES IN SOFTWARE FOR DIAGNOSIS AND TREATMENT USING EEPORTERS CLASSIFICATION TREE Bassey. A. Ekanem 1, Nseabasi Essien 2 1 Department of Computer Science, Delta State Polytechnic,
IDENTIFYING FAULT-PRONE MODULES IN SOFTWARE FOR DIAGNOSIS AND TREATMENT USING EEPORTERS CLASSIFICATION TREE Bassey. A. Ekanem 1, Nseabasi Essien 2 1 Department of Computer Science, Delta State Polytechnic,
Data Assimilation in Geosciences
 Data Assimilation in Geosciences Alberto Carrassi The Nordic Centre of Excellence for ensemble-based data assimilation Laurent Bertino (Lead), Alberto Carrassi (Co-Lead), Colin Grudzien (PD), Patrick Raanes
Data Assimilation in Geosciences Alberto Carrassi The Nordic Centre of Excellence for ensemble-based data assimilation Laurent Bertino (Lead), Alberto Carrassi (Co-Lead), Colin Grudzien (PD), Patrick Raanes
CHINA IN THE WORLD PODCAST. Host: Paul Haenle Guest: Claire Reade
 CHINA IN THE WORLD PODCAST Host: Paul Haenle Guest: Claire Reade Episode 73: U.S.-China Trade Relations in the Trump Era November 24, 2016 Haenle: Today, I m delighted to welcome Claire Reade, a nonresident
CHINA IN THE WORLD PODCAST Host: Paul Haenle Guest: Claire Reade Episode 73: U.S.-China Trade Relations in the Trump Era November 24, 2016 Haenle: Today, I m delighted to welcome Claire Reade, a nonresident
INSTRUCTIONS FOR USE
 GATEKEEPER INDIVIDUAL SUBSCRIBER AGREEMENT INSTRUCTIONS FOR USE Before a Certificate will be issued to you you need to follow these steps: 1. Fill in your name and the grade of Certificate you wish to
GATEKEEPER INDIVIDUAL SUBSCRIBER AGREEMENT INSTRUCTIONS FOR USE Before a Certificate will be issued to you you need to follow these steps: 1. Fill in your name and the grade of Certificate you wish to
Resolution Establishing a Surplus Property Policy
 Published on MTAS (http://www.mtas.tennessee.edu) September 30, 2018 Dear Reader: The following document was created from the MTAS electronic library known as MORe (www.mtas.tennessee.edu/more). This online
Published on MTAS (http://www.mtas.tennessee.edu) September 30, 2018 Dear Reader: The following document was created from the MTAS electronic library known as MORe (www.mtas.tennessee.edu/more). This online
(14 November 1997 to date) HAZARDOUS SUBSTANCES ACT 15 OF (Gazette No. 3834, No. 550 dated 4 April See Act for commencement dates.
 (14 November 1997 to date) HAZARDOUS SUBSTANCES ACT 15 OF 1973 (Gazette No. 3834, No. 550 dated 4 April 1973. See Act for commencement dates.) REGULATIONS UNDER THE HAZARDOUS SUBSTANCES ACT 15 OF 1973
(14 November 1997 to date) HAZARDOUS SUBSTANCES ACT 15 OF 1973 (Gazette No. 3834, No. 550 dated 4 April 1973. See Act for commencement dates.) REGULATIONS UNDER THE HAZARDOUS SUBSTANCES ACT 15 OF 1973
Probabilistic earthquake early warning in complex earth models using prior sampling
 Probabilistic earthquake early warning in complex earth models using prior sampling Andrew Valentine, Paul Käufl & Jeannot Trampert EGU 2016 21 st April www.geo.uu.nl/~andrew a.p.valentine@uu.nl A case
Probabilistic earthquake early warning in complex earth models using prior sampling Andrew Valentine, Paul Käufl & Jeannot Trampert EGU 2016 21 st April www.geo.uu.nl/~andrew a.p.valentine@uu.nl A case
An Audit of the November 2, 2010 Election in Richland County Duncan A. Buell, Eleanor Hare, Frank Heindel, Chip Moore 14 February 2011.
 THE LEAGUE OF WOMEN VOTERS OF SOUTH CAROLINA PO Box 8453, Columbia, SC, 29202, (803) 251-2726, www.lwvsc.org An Audit of the November 2, 2010 Election in Richland County Duncan A. Buell, Eleanor Hare,
THE LEAGUE OF WOMEN VOTERS OF SOUTH CAROLINA PO Box 8453, Columbia, SC, 29202, (803) 251-2726, www.lwvsc.org An Audit of the November 2, 2010 Election in Richland County Duncan A. Buell, Eleanor Hare,
And for such other and further relief as to this Court may deem just and proper.
 SUPERIOR COURT OF THE STATE OF NEW YORK COUNTY OF NIAGARA: CRIMINAL TERM THE PEOPLE OF THE STATE OF NEW YORK Indictment 2015-041 VS. DAVID SMITH NOTICE OF MOTION Defendant SIRS/MADAMES: PLEASE TAKE NOTICE,
SUPERIOR COURT OF THE STATE OF NEW YORK COUNTY OF NIAGARA: CRIMINAL TERM THE PEOPLE OF THE STATE OF NEW YORK Indictment 2015-041 VS. DAVID SMITH NOTICE OF MOTION Defendant SIRS/MADAMES: PLEASE TAKE NOTICE,
Cyber-Physical Systems Scheduling
 Cyber-Physical Systems Scheduling ICEN 553/453 Fall 2018 Prof. Dola Saha 1 Quick Recap 1. What characterizes the memory architecture of a system? 2. What are the issues with heaps in embedded/real-time
Cyber-Physical Systems Scheduling ICEN 553/453 Fall 2018 Prof. Dola Saha 1 Quick Recap 1. What characterizes the memory architecture of a system? 2. What are the issues with heaps in embedded/real-time
The documents listed below were utilized in the development of this Test Report:
 1 Introduction The purpose of this Test Report is to document the procedures that Pro V&V, Inc. followed to perform certification testing of the of the Dominion Voting System D-Suite 5.5-NC to the requirements
1 Introduction The purpose of this Test Report is to document the procedures that Pro V&V, Inc. followed to perform certification testing of the of the Dominion Voting System D-Suite 5.5-NC to the requirements
DBH 4 Social Science Contemporary history Unit 1: Political Revolutions: French Revolution. Name & last name:
 DBH 4 Social Science Contemporary history Unit 1: Political Revolutions: French Revolution Name & last name: Date:.. Class: DBH 4 A B C D Activity 1: multiple choice activity; choose the only right answer
DBH 4 Social Science Contemporary history Unit 1: Political Revolutions: French Revolution Name & last name: Date:.. Class: DBH 4 A B C D Activity 1: multiple choice activity; choose the only right answer
XMM-Newton Instrument Operations & Data Generation. J.R. Muñoz and the IOT members, SRE-OOX UGM#15, ESAC Apr 2014
 XMM-Newton Instrument Operations & Data Generation J.R. Muñoz and the IOT members, SRE-OOX UGM#15, ESAC 10-11 Apr 2014 Overview Ø Instrument Operations Instruments Status and Anomalies Instrument Operations
XMM-Newton Instrument Operations & Data Generation J.R. Muñoz and the IOT members, SRE-OOX UGM#15, ESAC 10-11 Apr 2014 Overview Ø Instrument Operations Instruments Status and Anomalies Instrument Operations
Virtual Memory and Address Translation
 Virtual Memry and Address Translatin Review! Prgram addresses are virtual addresses. Ø Relative ffset f prgram regins can nt change during prgram executin. E.g., heap can nt mve further frm cde. Ø Virtual
Virtual Memry and Address Translatin Review! Prgram addresses are virtual addresses. Ø Relative ffset f prgram regins can nt change during prgram executin. E.g., heap can nt mve further frm cde. Ø Virtual
BILL HORN SUPERVISOR, FIFTH DISTRICT SAN DIEGO COUNTY BOARD OF SUPERVISORS
 DATE: September 28, 2004 BILL HORN SUPERVISOR, FIFTH DISTRICT SAN DIEGO COUNTY BOARD OF SUPERVISORS AGENDA ITEM TO: Board of Supervisors SUBJECT: (District: 5) SUMMARY: Overview This year, more than ten
DATE: September 28, 2004 BILL HORN SUPERVISOR, FIFTH DISTRICT SAN DIEGO COUNTY BOARD OF SUPERVISORS AGENDA ITEM TO: Board of Supervisors SUBJECT: (District: 5) SUMMARY: Overview This year, more than ten
Commission Agreement for On-Line Course Materials
 DOCUMENT INFORMATION AND INSTRUCTIONS Commission Agreement for On-Line Course Materials Description: This contract form is to be used by the University of Minnesota Crookston to commission non-employees
DOCUMENT INFORMATION AND INSTRUCTIONS Commission Agreement for On-Line Course Materials Description: This contract form is to be used by the University of Minnesota Crookston to commission non-employees
Processes. Criteria for Comparing Scheduling Algorithms
 1 Processes Scheduling Processes Scheduling Processes Don Porter Portions courtesy Emmett Witchel Each process has state, that includes its text and data, procedure call stack, etc. This state resides
1 Processes Scheduling Processes Scheduling Processes Don Porter Portions courtesy Emmett Witchel Each process has state, that includes its text and data, procedure call stack, etc. This state resides
Interrogatories Are Written Questions For Which Written Answers Are Prepared And Signed Under Oath
 Interrogatories Are Written Questions For Which Written Answers Are Prepared And Signed Under Oath Opposing parties use various methods, such as interrogatories and for which written answers are prepared
Interrogatories Are Written Questions For Which Written Answers Are Prepared And Signed Under Oath Opposing parties use various methods, such as interrogatories and for which written answers are prepared
The Gender Gap's Back
 ABC NEWS POLLING UNIT BACKGROUNDER: THE GENDER GAP - 4/00 The Gender Gap's Back The gender gap, in hibernation earlier in the presidential campaign, is back and as big as ever. And its reappearance raises
ABC NEWS POLLING UNIT BACKGROUNDER: THE GENDER GAP - 4/00 The Gender Gap's Back The gender gap, in hibernation earlier in the presidential campaign, is back and as big as ever. And its reappearance raises
Production Sharing Agreements as a Form of International Cooperation N. Chebaeva, post-graduate student Supervisor Professor Dr. Igor B.
 Production Sharing Agreements as a Form of International Cooperation N. Chebaeva, post-graduate student Supervisor Professor Dr. Igor B. Sergeev Production Sharing Agreements PSA a contract, under which
Production Sharing Agreements as a Form of International Cooperation N. Chebaeva, post-graduate student Supervisor Professor Dr. Igor B. Sergeev Production Sharing Agreements PSA a contract, under which
Real-Time CORBA. Chenyang Lu CSE 520S
 Real-Time CORBA Chenyang Lu CSE 520S CORBA Common Object Request Broker Architecture Ø CORBA specifications q OMG is the standards body q Over 800 companies q CORBA defines interfaces, not implementations
Real-Time CORBA Chenyang Lu CSE 520S CORBA Common Object Request Broker Architecture Ø CORBA specifications q OMG is the standards body q Over 800 companies q CORBA defines interfaces, not implementations
PRE BEEISI8PJAL/ FeR 8FFlEI:\L else 8PJLY. Biometric Pathway. Transforming Air Travel. December 1, 2016 Version 3.0
 PRE BEEISI8PJAL/ FeR 8FFlEI:\L else 8PJLY Biometric Pathway Transforming Air Travel December 1, 2016 Version 3.0 RE I5Eel!HEJfJAt/ FeR efflelat erjt, epic.org EPIC-17-10-17-CBP-FOIA-20180319-Production
PRE BEEISI8PJAL/ FeR 8FFlEI:\L else 8PJLY Biometric Pathway Transforming Air Travel December 1, 2016 Version 3.0 RE I5Eel!HEJfJAt/ FeR efflelat erjt, epic.org EPIC-17-10-17-CBP-FOIA-20180319-Production
Why Biometrics? Why Biometrics? Biometric Technologies: Security and Privacy 2/25/2014. Dr. Rigoberto Chinchilla School of Technology
 Biometric Technologies: Security and Privacy Dr. Rigoberto Chinchilla School of Technology Why Biometrics? Reliable authorization and authentication are becoming necessary for many everyday actions (or
Biometric Technologies: Security and Privacy Dr. Rigoberto Chinchilla School of Technology Why Biometrics? Reliable authorization and authentication are becoming necessary for many everyday actions (or
2. Information concerning the host company s contact person the inviting party PLEASE COMPLETE IN CAPITAL LETTERS
 Invitation - business Invitation form for business visa applications VU1_en_200117 1. Information concerning the inviting company Company name Homepage Company address in Denmark Field of business CVR-.
Invitation - business Invitation form for business visa applications VU1_en_200117 1. Information concerning the inviting company Company name Homepage Company address in Denmark Field of business CVR-.
Search Trees. Chapter 10. CSE 2011 Prof. J. Elder Last Updated: :51 PM
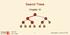 Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Requested by BE NCP EMN on 26 th October Compilation produced on 19 th December 2011
 Ad-Hoc Query on the rights of EU-citizens and their family members to move and reside freely within the territory of the Member State according to Council Directive 2004/38/EC Requested by BE NCP EMN on
Ad-Hoc Query on the rights of EU-citizens and their family members to move and reside freely within the territory of the Member State according to Council Directive 2004/38/EC Requested by BE NCP EMN on
Downloaded from: justpaste.it/vlxf
 Downloaded from: justpaste.it/vlxf Jun 24, 2016 20:19:27.468 [2944] INFO - Plex Media Server v1.0.0.2261-a17e99e - Microsoft PC - build: windows-i386 english Jun 24, 2016 20:19:27.469 [2944] INFO - Windows
Downloaded from: justpaste.it/vlxf Jun 24, 2016 20:19:27.468 [2944] INFO - Plex Media Server v1.0.0.2261-a17e99e - Microsoft PC - build: windows-i386 english Jun 24, 2016 20:19:27.469 [2944] INFO - Windows
An Algorithmic and Computational Approach to Optimizing Gerrymandering
 An Algorithmic and Computational Approach to Mentor: James Unwin, University of Illinois May 20, 2017 Introduction What and Why: Voting Districts in Democracy Determine elected representatives Equal population
An Algorithmic and Computational Approach to Mentor: James Unwin, University of Illinois May 20, 2017 Introduction What and Why: Voting Districts in Democracy Determine elected representatives Equal population
Complex systems theory & anarchism
 Complex systems theory & anarchism Gavin Mendel-Gleeson 2010-12-30 Contents * Complex systems theory & anarchism 3 Complex systems theory and society............................ 5 Structure and behaviour...................................
Complex systems theory & anarchism Gavin Mendel-Gleeson 2010-12-30 Contents * Complex systems theory & anarchism 3 Complex systems theory and society............................ 5 Structure and behaviour...................................
