Midterm Review. EECS 2011 Prof. J. Elder - 1 -
|
|
|
- Hubert Matthews
- 5 years ago
- Views:
Transcription
1 Midterm Review - 1 -
2 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps - 2 -
3 Data Structures So Far Ø Array List q (Extendable) Array Ø Node List q Singly or Doubly Linked List Ø Stack q Array q Singly Linked List Ø Queue q Array q Singly or Doubly Linked List Ø Priority Queue q Unsorted doubly-linked list q Sorted doubly-linked list q Heap (array-based) Ø Adaptable Priority Queue Ø Tree q Sorted doubly-linked list with locationaware entries q Heap with location-aware entries q Linked Structure Ø Binary Tree q Linked Structure q Array - 3 -
4 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps - 4 -
5 Data Structures & Object-Oriented Design Ø Definitions Ø Principles of Object-Oriented Design Ø Hierarchical Design in Java Ø Abstract Data Types & Interfaces Ø Casting Ø Generics Ø Pseudo-Code - 5 -
6 Ø Software must be: q Readable and understandable Software Engineering ² Allows correctness to be verified, and software to be easily updated. q Correct and complete ² Works correctly for all expected inputs q Robust ² Capable of handling unexpected inputs. q Adaptible ² All programs evolve over time. Programs should be designed so that re-use, generalization and modification is easy. q Portable ² Easily ported to new hardware or operating system platforms. q Efficient ² Makes reasonable use of time and memory resources
7 Seven Important Functions Ø Seven functions that often appear in algorithm analysis: q Constant 1 q Logarithmic log n q Linear n q N-Log-N n log n q Quadratic n 2 q Cubic n 3 q Exponential 2 n Ø In a log-log chart, the slope of the line corresponds to the growth rate of the function
8 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps - 8 -
9 Some Math to Review " Summations Ø properties of logarithms: " Logarithms and Exponents log b (xy) = log b x + log b y " Existential and universal operators " Proof techniques log b (x/y) = log b x - log b y " Basic probability log b x a = alog b x log b a = log x a/log x b existential and universal operators g b Loves(b, g) g b Loves(b, g) Ø properties of exponentials: a (b+c) = a b a c a bc = (a b ) c a b /a c = a (b-c) b = a log a b b c = a c*log a b - 9 -
10 Definition of Big Oh cg( n) fn ( ) fn ( ) Ogn ( ( )) gn ( ) > cn, 0 0: n n0, f( n) cgn ( ) n
11 Arithmetic Progression Ø The running time of prefixaverages1 is O( n) Ø The sum of the first n integers is n(n + 1) / 2 q There is a simple visual proof of this fact Ø Thus, algorithm prefixaverages1 runs in O(n 2 ) time
12 Relatives of Big-Oh " big-omega n f(n) is Ω(g(n)) if there is a constant c > 0 and an integer constant n 0 1 such that f(n) c g(n) for n n 0 " big-theta n f(n) is Θ(g(n)) if there are constants c 1 > 0 and c 2 > 0 and an integer constant n 0 1 such that c 1 g(n) f(n) c 2 g(n) for n n
13 Time Complexity of an Algorithm The time complexity of an algorithm is the largest time required on any input of size n. (Worst case analysis.) Ø O(n 2 ): For any input size n n 0, the algorithm takes no more than cn 2 time on every input. Ø Ω(n 2 ): For any input size n n 0, the algorithm takes at least cn 2 time on at least one input. Ø θ (n 2 ): Do both
14 Time Complexity of a Problem The time complexity of a problem is the time complexity of the fastest algorithm that solves the problem. Ø O(n 2 ): Provide an algorithm that solves the problem in no more than this time. q Remember: for every input, i.e. worst case analysis! Ø Ω(n 2 ): Prove that no algorithm can solve it faster. q Remember: only need one input that takes at least this long! Ø θ (n 2 ): Do both
15 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps
16 Arrays
17 Arrays Ø Array: a sequence of indexed components with the following properties: q array size is fixed at the time of array s construction ² int[] numbers = new int [10]; q array elements are placed contiguously in memory ² address of any element can be calculated directly as its offset from the beginning of the array q consequently, array components can be efficiently inspected or updated in O(1) time, using their indices ² randomnumber = numbers[5]; ² numbers[2] = 100;
18 Arrays in Java Ø Since an array is an object, the name of the array is actually a reference (pointer) to the place in memory where the array is stored. q reference to an object holds the address of the actual object Ø Example [ arrays as objects] int[] A={12, 24, 37, 53, 67}; int[] B=A; B[3]=5; Ø Example [ cloning an array] int[] A={12, 24, 37, 53, 67}; int[] B=A.clone(); B[3]=5; A B A B A B A B
19 Example Example [ 2D array in Java = array of arrays] int[][] nums = new int[5][4]; int[][] nums; nums = new int[5][]; for (int i=0; i<5; i++) { nums[i] = new int[4]; }
20 Array Lists
21 The Array List ADT ( 6.1) Ø The Array List ADT extends the notion of array by storing a sequence of arbitrary objects Ø An element can be accessed, inserted or removed by specifying its rank (number of elements preceding it) Ø An exception is thrown if an incorrect rank is specified (e.g., a negative rank)
22 The Array List ADT public interface IndexList<E> { /** Returns the number of elements in this list */ public int size(); /** Returns whether the list is empty. */ public boolean isempty(); /** Inserts an element e to be at index I, shifting all elements after this. */ public void add(int I, E e) throws IndexOutOfBoundsException; /** Returns the element at index I, without removing it. */ public E get(int i) throws IndexOutOfBoundsException; /** Removes and returns the element at index I, shifting the elements after this. */ public E remove(int i) throws IndexOutOfBoundsException; /** Replaces the element at index I with e, returning the previous element at i. */ public E set(int I, E e) throws IndexOutOfBoundsException; }
23 Performance Ø In the array based implementation q The space used by the data structure is O(n) q size, isempty, get and set run in O(1) time q add and remove run in O(n) time Ø In an add operation, when the array is full, instead of throwing an exception, we could replace the array with a larger one. Ø In fact java.util.arraylist implements this ADT using extendable arrays that do just this
24 Doubling Strategy Analysis Ø We replace the array k = log 2 n times Ø The total time T(n) of a series of n add(o) operations is proportional to n k = n + 2 k = 2n -1 Ø Thus T(n) is O(n) Ø The amortized time of an add operation is O(1)! geometric series Recall: n r i = i =0 n+1 1 r 1 r
25 Stacks Chapter
26 The Stack ADT Ø The Stack ADT stores arbitrary objects Ø Insertions and deletions follow the last-in first-out scheme Ø Think of a spring-loaded plate dispenser Ø Main stack operations: q push(object): inserts an element q object pop(): removes and returns the last inserted element Ø Auxiliary stack operations: q object top(): returns the last inserted element without removing it q integer size(): returns the number of elements stored q boolean isempty(): indicates whether no elements are stored
27 Array-based Stack Ø A simple way of implementing the Stack ADT uses an array Ø We add elements from left to right Ø A variable keeps track of the index of the top element Algorithm size() return t + 1 Algorithm pop() if isempty() then throw EmptyStackException else t ç t - 1 return S[t + 1] S t
28 Queues Chapters
29 Array-Based Queue Ø Use an array of size N in a circular fashion Ø Two variables keep track of the front and rear f index of the front element r index immediately past the rear element Ø Array location r is kept empty Q normal configuration f r Q wrapped-around configuration r f
30 Queue Operations Ø We use the modulo operator (remainder of division) Algorithm size() return (N - f + r) mod N Algorithm isempty() return (f = r) Note: N f + r = (r + N) f Q f r Q r f
31 Linked Lists Chapters
32 Singly Linked List ( 3.2) Ø A singly linked list is a concrete data structure consisting of a sequence of nodes Ø Each node stores q element q link to the next node elem next node A B C D
33 Running Time Ø Adding at the head is O(1) Ø Removing at the head is O(1) Ø How about tail operations?
34 Doubly Linked List Ø Doubly-linked lists allow more flexible list management (constant time operations at both ends). Ø Nodes store: q element q link to the previous node prev next q link to the next node Ø Special trailer and header (sentinel) nodes elem node header nodes/positions trailer elements
35 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps
36 Iterators Ø An Iterator is an object that enables you to traverse through a collection and to remove elements from the collection selectively, if desired. Ø You get an Iterator for a collection by calling its iterator method. Ø Suppose collection is an instance of a Collection. Then to print out each element on a separate line: Iterator<E> it = collection.iterator(); while (it.hasnext()) System.out.println(it.next());
37 The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List Priority Queue Abstract Sequential List Array List Vector Stack Linked List
38 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps
39 Linear Recursion Design Pattern Ø Test for base cases q Begin by testing for a set of base cases (there should be at least one). q Every possible chain of recursive calls must eventually reach a base case, and the handling of each base case should not use recursion. Ø Recurse once q Perform a single recursive call. (This recursive step may involve a test that decides which of several possible recursive calls to make, but it should ultimately choose to make just one of these calls each time we perform this step.) q Define each possible recursive call so that it makes progress towards a base case
40 Binary Recursion Ø Binary recursion occurs whenever there are two recursive calls for each non-base case. Ø Example 1: The Fibonacci Sequence
41 Formal Definition of Rooted Tree Ø A rooted tree may be empty. Ø Otherwise, it consists of q A root node r q A set of subtrees whose roots are the children of r r B C D E F G H I J K subtree
42 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps
43 Tree Terminology Ø Root: node without parent (A) Ø Internal node: node with at least one child (A, B, C, F) Ø External node (a.k.a. leaf ): node without children (E, I, J, K, G, H, D) Ø Ancestors of a node: parent, grandparent, grand-grandparent, etc. A Ø Descendant of a node: child, grandchild, grand-grandchild, etc. Ø Siblings: two nodes having the same parent B C D Ø Depth of a node: number of ancestors (excluding self) E F G H Ø Height of a tree: maximum depth of any node (3) Ø Subtree: tree consisting of a node and its descendants I J K subtree
44 Position ADT Ø The Position ADT models the notion of place within a data structure where a single object is stored Ø It gives a unified view of diverse ways of storing data, such as q a cell of an array q a node of a linked list q a node of a tree Ø Just one method: q object element(): returns the element stored at the position
45 Tree ADT Ø We use positions to abstract nodes Ø Generic methods: q integer size() q boolean isempty() q Iterator iterator() q Iterable positions() Ø Accessor methods: q position root() q position parent(p) q positioniterator children(p) Ø Query methods: q boolean isinternal(p) q boolean isexternal(p) q boolean isroot(p) Ø Update method: q object replace(p, o) q Additional update methods may be defined by data structures implementing the Tree ADT
46 Preorder Traversal Ø A traversal visits the nodes of a tree in a systematic manner Ø In a preorder traversal, a node is visited before its descendants Algorithm preorder(v) visit(v) for each child w of v preorder (w) 1 Make Money Fast! 2 1. Motivations 2. Methods References Greed 1.2 Avidity Stock Fraud 2.2 Ponzi Scheme 2.3 Bank Robbery
47 Postorder Traversal Ø In a postorder traversal, a node is visited after its descendants Algorithm postorder(v) for each child w of v postorder (w) visit(v) 9 cs16/ 3 homeworks/ 7 programs/ 8 todo.txt 1K h1c.doc 3K h1nc.doc 2K DDR.java 10K Stocks.java 25K Robot.java 20K
48 Properties of Proper Binary Trees Ø Notation n number of nodes e number of external nodes i number of internal nodes h height Ø Properties: q e = i + 1 q n = 2e - 1 q h i q h (n - 1)/2 q e 2 h q h log 2 e q h log 2 (n + 1)
49 BinaryTree ADT Ø The BinaryTree ADT extends the Tree ADT, i.e., it inherits all the methods of the Tree ADT Ø Additional methods: q position left(p) q position right(p) q boolean hasleft(p) q boolean hasright(p) Ø Update methods may be defined by data structures implementing the BinaryTree ADT
50 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps
51 Priority Queue ADT Ø A priority queue stores a collection of entries Ø Each entry is a pair (key, value) Ø Main methods of the Priority Queue ADT q insert(k, x) inserts an entry with key k and value x q removemin() removes and returns the entry with smallest key Ø Additional methods q min() returns, but does not remove, an entry with smallest key q size(), isempty() Ø Applications: q Process scheduling q Standby flyers
52 Entry ADT Ø An entry in a priority queue is simply a keyvalue pair Ø Methods: q key(): returns the key for this entry q value(): returns the value for this entry Ø As a Java interface: /** * Interface for a key-value * pair entry **/ public interface Entry { public Object key(); public Object value(); }
53 Comparator ADT Ø A comparator encapsulates the action of comparing two objects according to a given total order relation Ø A generic priority queue uses an auxiliary comparator Ø The comparator is external to the keys being compared Ø When the priority queue needs to compare two keys, it uses its comparator Ø The primary method of the Comparator ADT: q compare(a, b): ² Returns an integer i such that v i < 0 if a < b v i = 0 if a = b v i > 0 if a > b v an error occurs if a and b cannot be compared
54 Sequence-based Priority Queue Ø Implementation with an unsorted list Ø Implementation with a sorted list Ø Performance: q insert takes O(1) time since we can insert the item at the beginning or end of the sequence q removemin and min take O(n) time since we have to traverse the entire sequence to find the smallest key Ø Performance: q insert takes O(n) time since we have to find the right place to insert the item q removemin and min take O(1) time, since the smallest key is at the beginning Is this tradeoff inevitable?
55 Heaps Ø Goal: q O(log n) insertion q O(log n) removal Ø Remember that O(log n) is almost as good as O(1)! q e.g., n = 1,000,000,000 à log n 30 Ø There are min heaps and max heaps. We will assume min heaps
56 Min Heaps Ø A min heap is a binary tree storing keys at its nodes and satisfying the following properties: q Heap-order: for every internal node v other than the root ² key(v) key(parent(v)) q (Almost) complete binary tree: let h be the height of the heap ² for i = 0,, h - 1, there are 2 i nodes of depth i ² at depth h 1 v the internal nodes are to the left of the external nodes v Only the rightmost internal node may have a single child q The last node of a heap is the rightmost node of depth h
57 Upheap Ø After the insertion of a new key k, the heap-order property may be violated Ø Algorithm upheap restores the heap-order property by swapping k along an upward path from the insertion node Ø Upheap terminates when the key k reaches the root or a node whose parent has a key smaller than or equal to k Ø Since a heap has height O(log n), upheap runs in O(log n) time
58 Downheap Ø After replacing the root key with the key k of the last node, the heap-order property may be violated Ø Algorithm downheap restores the heap-order property by swapping key k along a downward path from the root Ø Note that there are, in general, many possible downward paths which one do we choose??? 7 5 w
59 Downheap Ø We select the downward path through the minimum-key nodes. Ø Downheap terminates when key k reaches a leaf or a node whose children have keys greater than or equal to k Ø Since a heap has height O(log n), downheap runs in O(log n) time w 6 7 w
60 Array-based Heap Implementation Ø We can represent a heap with n keys by means of an array of length n + 1 Ø Links between nodes are not explicitly stored 2 Ø The cell at rank 0 is not used Ø The root is stored at rank 1. Ø For the node at rank i q the left child is at rank 2i q the right child is at rank 2i q the parent is at rank floor(i/2) q if 2i + 1 > n, the node has no right child q if 2i > n, the node is a leaf
61 Bottom-up Heap Construction Ø We can construct a heap storing n keys using a bottom-up construction with log n phases 2 i -1 2 i -1 Ø In phase i, pairs of heaps with 2 i -1 keys are merged into heaps with 2 i+1-1 keys Ø Run time for construction is O(n). 2 i
62 Adaptable Priority 3 a Queues 5 g 4 e
63 Additional Methods of the Adaptable Priority Queue ADT Ø remove(e): Remove from P and return entry e. Ø replacekey(e,k): Replace with k and return the old key; an error condition occurs if k is invalid (that is, k cannot be compared with other keys). Ø replacevalue(e,x): Replace with x and return the old value
64 Location-Aware Entries Ø A locator-aware entry identifies and tracks the location of its (key, value) object within a data structure
65 List Implementation Ø A location-aware list entry is an object storing q key q value q position (or rank) of the item in the list Ø In turn, the position (or array cell) stores the entry Ø Back pointers (or ranks) are updated during swaps header nodes/positions trailer 2 c 4 a 5 d 8 b entries
66 Heap Implementation Ø A location-aware heap entry is an object storing q key 2 d q value q position of the entry in the underlying heap Ø In turn, each heap position stores an entry Ø Back pointers are updated during entry swaps 4 a 6 b 8 g 5 e 9 c
67 Performance Ø Times better than those achievable without location-aware entries are highlighted in red: Method Unsorted List Sorted List Heap size, isempty O(1) O(1) O(1) insert O(1) O(n) O(log n) min O(n) O(1) O(1) removemin O(n) O(1) O(log n) remove O(1) O(1) O(log n) replacekey O(1) O(n) O(log n) replacevalue O(1) O(1) O(1)
68 Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues & Heaps
Midterm Review. EECS 2011 Prof. J. Elder - 1 -
 Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Priority Queues & Heaps
 Priority Queues & Heaps Chapter 8-1 - The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List
Priority Queues & Heaps Chapter 8-1 - The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Search Trees. Chapter 10. CSE 2011 Prof. J. Elder Last Updated: :51 PM
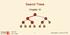 Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
ECE250: Algorithms and Data Structures Trees
 ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
Maps and Hash Tables. EECS 2011 Prof. J. Elder - 1 -
 Maps and Hash Tables - 1 - Outline Ø Maps Ø Hashing Ø Multimaps Ø Ordered Maps - 2 - Learning Outcomes Ø By understanding this lecture, you should be able to: Ø Outline the ADT for a map and a multimap
Maps and Hash Tables - 1 - Outline Ø Maps Ø Hashing Ø Multimaps Ø Ordered Maps - 2 - Learning Outcomes Ø By understanding this lecture, you should be able to: Ø Outline the ADT for a map and a multimap
Maps, Hash Tables and Dictionaries
 Maps, Hash Tables and Dictionaries Chapter 9-1 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 2 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 3 -
Maps, Hash Tables and Dictionaries Chapter 9-1 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 2 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 3 -
Comparison Sorts. EECS 2011 Prof. J. Elder - 1 -
 Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
File Systems: Fundamentals
 File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
COMP : DATA STRUCTURES 2/27/14. Are binary trees satisfying two additional properties:
 BINARY HEAPS Two Additional Properties 9 Binary Heaps Are binary trees satisfying two additional properties: Ø Structure property: Levels are filled in order, left to right Also known as complete binary
BINARY HEAPS Two Additional Properties 9 Binary Heaps Are binary trees satisfying two additional properties: Ø Structure property: Levels are filled in order, left to right Also known as complete binary
TAFTW (Take Aways for the Week) APT Quiz and Markov Overview. Comparing objects and tradeoffs. From Comparable to TreeMap/Sort
 TAFTW (Take Aways for the Week) Graded work this week: Ø APT Quiz, details and overview Ø Markov assignment, details and overview Concepts: Empirical and Analytical Analysis Ø Algorithms and Data Structures
TAFTW (Take Aways for the Week) Graded work this week: Ø APT Quiz, details and overview Ø Markov assignment, details and overview Concepts: Empirical and Analytical Analysis Ø Algorithms and Data Structures
Chapter 8: Recursion
 Chapter 8: Recursion Presentation slides for Java Software Solutions for AP* Computer Science 3rd Edition by John Lewis, William Loftus, and Cara Cocking Java Software Solutions is published by Addison-Wesley
Chapter 8: Recursion Presentation slides for Java Software Solutions for AP* Computer Science 3rd Edition by John Lewis, William Loftus, and Cara Cocking Java Software Solutions is published by Addison-Wesley
Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times
 Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Estimating the Margin of Victory for Instant-Runoff Voting
 Estimating the Margin of Victory for Instant-Runoff Voting David Cary Abstract A general definition is proposed for the margin of victory of an election contest. That definition is applied to Instant Runoff
Estimating the Margin of Victory for Instant-Runoff Voting David Cary Abstract A general definition is proposed for the margin of victory of an election contest. That definition is applied to Instant Runoff
CS 5523: Operating Systems
 Lecture1: OS Overview CS 5523: Operating Systems Instructor: Dr Tongping Liu Midterm Exam: Oct 2, 2017, Monday 7:20pm 8:45pm Operating System: what is it?! Evolution of Computer Systems and OS Concepts
Lecture1: OS Overview CS 5523: Operating Systems Instructor: Dr Tongping Liu Midterm Exam: Oct 2, 2017, Monday 7:20pm 8:45pm Operating System: what is it?! Evolution of Computer Systems and OS Concepts
Optimization Strategies
 Global Memory Access Pattern and Control Flow Objectives Ø Ø Global Memory Access Pattern (Coalescing) Ø Control Flow (Divergent branch) Copyright 2013 by Yong Cao, Referencing UIUC ECE498AL Course Notes
Global Memory Access Pattern and Control Flow Objectives Ø Ø Global Memory Access Pattern (Coalescing) Ø Control Flow (Divergent branch) Copyright 2013 by Yong Cao, Referencing UIUC ECE498AL Course Notes
Uninformed search. Lirong Xia
 Uninformed search Lirong Xia Spring, 2017 Today s schedule ØRational agents ØSearch problems State space graph: modeling the problem Search trees: scratch paper for solution ØUninformed search Depth first
Uninformed search Lirong Xia Spring, 2017 Today s schedule ØRational agents ØSearch problems State space graph: modeling the problem Search trees: scratch paper for solution ØUninformed search Depth first
Constraint satisfaction problems. Lirong Xia
 Constraint satisfaction problems Lirong Xia Spring, 2017 Project 1 Ø You can use Windows Ø Read the instruction carefully, make sure you understand the goal search for YOUR CODE HERE Ø Ask and answer questions
Constraint satisfaction problems Lirong Xia Spring, 2017 Project 1 Ø You can use Windows Ø Read the instruction carefully, make sure you understand the goal search for YOUR CODE HERE Ø Ask and answer questions
Hoboken Public Schools. Algebra II Honors Curriculum
 Hoboken Public Schools Algebra II Honors Curriculum Algebra Two Honors HOBOKEN PUBLIC SCHOOLS Course Description Algebra II Honors continues to build students understanding of the concepts that provide
Hoboken Public Schools Algebra II Honors Curriculum Algebra Two Honors HOBOKEN PUBLIC SCHOOLS Course Description Algebra II Honors continues to build students understanding of the concepts that provide
Contents. Bibliography 121. Index 123
 Contents 5 Advanced Data Types page 2 5.1 Sparse Arrays: Dictionary Arrays, Hashing Arrays, and Maps 2 5.2 The Implementation of the Data Type Map 14 5.3 Dictionaries and Sets 27 5.4 Priority Queues 28
Contents 5 Advanced Data Types page 2 5.1 Sparse Arrays: Dictionary Arrays, Hashing Arrays, and Maps 2 5.2 The Implementation of the Data Type Map 14 5.3 Dictionaries and Sets 27 5.4 Priority Queues 28
NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York
 NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York DEPARTMENT: Mathematics COURSE: MAT 2440/ MA 440 TITLE: DESCRIPTION: TEXTS: Discrete Structures and Algorithms I This course introduces
NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York DEPARTMENT: Mathematics COURSE: MAT 2440/ MA 440 TITLE: DESCRIPTION: TEXTS: Discrete Structures and Algorithms I This course introduces
Data 100. Lecture 9: Scraping Web Technologies. Slides by: Joseph E. Gonzalez, Deb Nolan
 Data 100 Lecture 9: Scraping Web Technologies Slides by: Joseph E. Gonzalez, Deb Nolan deborah_nolan@berkeley.edu hellerstein@berkeley.edu? Last Week Visualization Ø Tools and Technologies Ø Maplotlib
Data 100 Lecture 9: Scraping Web Technologies Slides by: Joseph E. Gonzalez, Deb Nolan deborah_nolan@berkeley.edu hellerstein@berkeley.edu? Last Week Visualization Ø Tools and Technologies Ø Maplotlib
Hoboken Public Schools. College Algebra Curriculum
 Hoboken Public Schools College Algebra Curriculum College Algebra HOBOKEN PUBLIC SCHOOLS Course Description College Algebra reflects the New Jersey learning standards at the high school level and is designed
Hoboken Public Schools College Algebra Curriculum College Algebra HOBOKEN PUBLIC SCHOOLS Course Description College Algebra reflects the New Jersey learning standards at the high school level and is designed
Chapter 11. Weighted Voting Systems. For All Practical Purposes: Effective Teaching
 Chapter Weighted Voting Systems For All Practical Purposes: Effective Teaching In observing other faculty or TA s, if you discover a teaching technique that you feel was particularly effective, don t hesitate
Chapter Weighted Voting Systems For All Practical Purposes: Effective Teaching In observing other faculty or TA s, if you discover a teaching technique that you feel was particularly effective, don t hesitate
Notes for Session 7 Basic Voting Theory and Arrow s Theorem
 Notes for Session 7 Basic Voting Theory and Arrow s Theorem We follow up the Impossibility (Session 6) of pooling expert probabilities, while preserving unanimities in both unconditional and conditional
Notes for Session 7 Basic Voting Theory and Arrow s Theorem We follow up the Impossibility (Session 6) of pooling expert probabilities, while preserving unanimities in both unconditional and conditional
Event Based Sequential Program Development: Application to Constructing a Pointer Program
 Event Based Sequential Program Development: Application to Constructing a Pointer Program Jean-Raymond Abrial Consultant, Marseille, France jr@abrial.org Abstract. In this article, I present an event approach
Event Based Sequential Program Development: Application to Constructing a Pointer Program Jean-Raymond Abrial Consultant, Marseille, France jr@abrial.org Abstract. In this article, I present an event approach
A Calculus for End-to-end Statistical Service Guarantees
 A Calculus for End-to-end Statistical Service Guarantees Technical Report: University of Virginia, CS-2001-19 (2nd revised version) Almut Burchard Ý Jörg Liebeherr Stephen Patek Ý Department of Mathematics
A Calculus for End-to-end Statistical Service Guarantees Technical Report: University of Virginia, CS-2001-19 (2nd revised version) Almut Burchard Ý Jörg Liebeherr Stephen Patek Ý Department of Mathematics
Complexity of Manipulating Elections with Few Candidates
 Complexity of Manipulating Elections with Few Candidates Vincent Conitzer and Tuomas Sandholm Computer Science Department Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 {conitzer, sandholm}@cs.cmu.edu
Complexity of Manipulating Elections with Few Candidates Vincent Conitzer and Tuomas Sandholm Computer Science Department Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 {conitzer, sandholm}@cs.cmu.edu
Text UI. Data Store Ø Example of a backend to a real Could add a different user interface. Good judgment comes from experience
 Reviewing Lab 10 Text UI Created two classes Ø Used one class within another class Ø Tested them Graphical UI Backend Data Store Ø Example of a backend to a real applica@on Could add a different user interface
Reviewing Lab 10 Text UI Created two classes Ø Used one class within another class Ø Tested them Graphical UI Backend Data Store Ø Example of a backend to a real applica@on Could add a different user interface
Approval Voting Theory with Multiple Levels of Approval
 Claremont Colleges Scholarship @ Claremont HMC Senior Theses HMC Student Scholarship 2012 Approval Voting Theory with Multiple Levels of Approval Craig Burkhart Harvey Mudd College Recommended Citation
Claremont Colleges Scholarship @ Claremont HMC Senior Theses HMC Student Scholarship 2012 Approval Voting Theory with Multiple Levels of Approval Craig Burkhart Harvey Mudd College Recommended Citation
The Effectiveness of Receipt-Based Attacks on ThreeBallot
 The Effectiveness of Receipt-Based Attacks on ThreeBallot Kevin Henry, Douglas R. Stinson, Jiayuan Sui David R. Cheriton School of Computer Science University of Waterloo Waterloo, N, N2L 3G1, Canada {k2henry,
The Effectiveness of Receipt-Based Attacks on ThreeBallot Kevin Henry, Douglas R. Stinson, Jiayuan Sui David R. Cheriton School of Computer Science University of Waterloo Waterloo, N, N2L 3G1, Canada {k2henry,
Mathematics and Social Choice Theory. Topic 4 Voting methods with more than 2 alternatives. 4.1 Social choice procedures
 Mathematics and Social Choice Theory Topic 4 Voting methods with more than 2 alternatives 4.1 Social choice procedures 4.2 Analysis of voting methods 4.3 Arrow s Impossibility Theorem 4.4 Cumulative voting
Mathematics and Social Choice Theory Topic 4 Voting methods with more than 2 alternatives 4.1 Social choice procedures 4.2 Analysis of voting methods 4.3 Arrow s Impossibility Theorem 4.4 Cumulative voting
One View Watchlists Implementation Guide Release 9.2
 [1]JD Edwards EnterpriseOne Applications One View Watchlists Implementation Guide Release 9.2 E63996-03 April 2017 Describes One View Watchlists and discusses how to add and modify One View Watchlists.
[1]JD Edwards EnterpriseOne Applications One View Watchlists Implementation Guide Release 9.2 E63996-03 April 2017 Describes One View Watchlists and discusses how to add and modify One View Watchlists.
Estimating the Margin of Victory for an IRV Election Part 1 by David Cary November 6, 2010
 Summary Estimating the Margin of Victory for an IRV Election Part 1 by David Cary November 6, 2010 New procedures are being developed for post-election audits involving manual recounts of random samples
Summary Estimating the Margin of Victory for an IRV Election Part 1 by David Cary November 6, 2010 New procedures are being developed for post-election audits involving manual recounts of random samples
General Framework of Electronic Voting and Implementation thereof at National Elections in Estonia
 State Electoral Office of Estonia General Framework of Electronic Voting and Implementation thereof at National Elections in Estonia Document: IVXV-ÜK-1.0 Date: 20 June 2017 Tallinn 2017 Annotation This
State Electoral Office of Estonia General Framework of Electronic Voting and Implementation thereof at National Elections in Estonia Document: IVXV-ÜK-1.0 Date: 20 June 2017 Tallinn 2017 Annotation This
Primecoin: Cryptocurrency with Prime Number Proof-of-Work
 Primecoin: Cryptocurrency with Prime Number Proof-of-Work Sunny King (sunnyking9999@gmail.com) July 7 th, 2013 Abstract A new type of proof-of-work based on searching for prime numbers is introduced in
Primecoin: Cryptocurrency with Prime Number Proof-of-Work Sunny King (sunnyking9999@gmail.com) July 7 th, 2013 Abstract A new type of proof-of-work based on searching for prime numbers is introduced in
Year 1 Mental mathematics and fluency in rapid recall of number facts are one of the main aims of the new Mathematics Curriculum.
 Year 1 by the end of Year 1. Ø Recite numbers to 100 forwards and backwards from any number Ø Read and write numbers to 100 in numerals Ø Read and write numbers to 20 in words Ø Order numbers to 100 Ø
Year 1 by the end of Year 1. Ø Recite numbers to 100 forwards and backwards from any number Ø Read and write numbers to 100 in numerals Ø Read and write numbers to 20 in words Ø Order numbers to 100 Ø
Estonian National Electoral Committee. E-Voting System. General Overview
 Estonian National Electoral Committee E-Voting System General Overview Tallinn 2005-2010 Annotation This paper gives an overview of the technical and organisational aspects of the Estonian e-voting system.
Estonian National Electoral Committee E-Voting System General Overview Tallinn 2005-2010 Annotation This paper gives an overview of the technical and organisational aspects of the Estonian e-voting system.
Cluster Analysis. (see also: Segmentation)
 Cluster Analysis (see also: Segmentation) Cluster Analysis Ø Unsupervised: no target variable for training Ø Partition the data into groups (clusters) so that: Ø Observations within a cluster are similar
Cluster Analysis (see also: Segmentation) Cluster Analysis Ø Unsupervised: no target variable for training Ø Partition the data into groups (clusters) so that: Ø Observations within a cluster are similar
This situation where each voter is not equal in the number of votes they control is called:
 Finite Math A Chapter 2, Weighted Voting Systems 1 Discrete Mathematics Notes Chapter 2: Weighted Voting Systems The Power Game Academic Standards: PS.ED.2: Use election theory techniques to analyze election
Finite Math A Chapter 2, Weighted Voting Systems 1 Discrete Mathematics Notes Chapter 2: Weighted Voting Systems The Power Game Academic Standards: PS.ED.2: Use election theory techniques to analyze election
Swiss E-Voting Workshop 2010
 Swiss E-Voting Workshop 2010 Verifiability in Remote Voting Systems September 2010 Jordi Puiggali VP Research & Development Jordi.Puiggali@scytl.com Index Auditability in e-voting Types of verifiability
Swiss E-Voting Workshop 2010 Verifiability in Remote Voting Systems September 2010 Jordi Puiggali VP Research & Development Jordi.Puiggali@scytl.com Index Auditability in e-voting Types of verifiability
Introduction to Game Theory. Lirong Xia
 Introduction to Game Theory Lirong Xia Fall, 2016 Homework 1 2 Announcements ØWe will use LMS for submission and grading ØPlease just submit one copy ØPlease acknowledge your team mates 3 Ø Show the math
Introduction to Game Theory Lirong Xia Fall, 2016 Homework 1 2 Announcements ØWe will use LMS for submission and grading ØPlease just submit one copy ØPlease acknowledge your team mates 3 Ø Show the math
Please reach out to for a complete list of our GET::search method conditions. 3
 Appendix 2 Technical and Methodological Details Abstract The bulk of the work described below can be neatly divided into two sequential phases: scraping and matching. The scraping phase includes all of
Appendix 2 Technical and Methodological Details Abstract The bulk of the work described below can be neatly divided into two sequential phases: scraping and matching. The scraping phase includes all of
IBM Cognos Open Mic Cognos Analytics 11 Part nd June, IBM Corporation
 IBM Cognos Open Mic Cognos Analytics 11 Part 2 22 nd June, 2016 IBM Cognos Open MIC Team Deepak Giri Presenter Subhash Kothari Technical Panel Member Chakravarthi Mannava Technical Panel Member 2 Agenda
IBM Cognos Open Mic Cognos Analytics 11 Part 2 22 nd June, 2016 IBM Cognos Open MIC Team Deepak Giri Presenter Subhash Kothari Technical Panel Member Chakravarthi Mannava Technical Panel Member 2 Agenda
Batch binary Edwards. D. J. Bernstein University of Illinois at Chicago NSF ITR
 Batch binary Edwards D. J. Bernstein University of Illinois at Chicago NSF ITR 0716498 Nonnegative elements of Z: etc. 0 meaning 0 1 meaning 2 0 10 meaning 2 1 11 meaning 2 0 + 2 1 100 meaning 2 2 101
Batch binary Edwards D. J. Bernstein University of Illinois at Chicago NSF ITR 0716498 Nonnegative elements of Z: etc. 0 meaning 0 1 meaning 2 0 10 meaning 2 1 11 meaning 2 0 + 2 1 100 meaning 2 2 101
Exploring QR Factorization on GPU for Quantum Monte Carlo Simulation
 Exploring QR Factorization on GPU for Quantum Monte Carlo Simulation Tyler McDaniel Ming Wong Mentors: Ed D Azevedo, Ying Wai Li, Kwai Wong Quantum Monte Carlo Simulation Slater Determinant for N-electrons
Exploring QR Factorization on GPU for Quantum Monte Carlo Simulation Tyler McDaniel Ming Wong Mentors: Ed D Azevedo, Ying Wai Li, Kwai Wong Quantum Monte Carlo Simulation Slater Determinant for N-electrons
Fall 2016 COP 3223H Program #5: Election Season Nears an End Due date: Please consult WebCourses for your section
 Fall 2016 COP 3223H Program #5: Election Season Nears an End Due date: Please consult WebCourses for your section Objective(s) 1. To learn how to use 1D arrays to solve a problem in C. Problem A: Expected
Fall 2016 COP 3223H Program #5: Election Season Nears an End Due date: Please consult WebCourses for your section Objective(s) 1. To learn how to use 1D arrays to solve a problem in C. Problem A: Expected
Lecture 6 Cryptographic Hash Functions
 Lecture 6 Cryptographic Hash Functions 1 Purpose Ø CHF one of the most important tools in modern cryptography and security Ø In crypto, CHF instantiates a Random Oracle paradigm Ø In security, used in
Lecture 6 Cryptographic Hash Functions 1 Purpose Ø CHF one of the most important tools in modern cryptography and security Ø In crypto, CHF instantiates a Random Oracle paradigm Ø In security, used in
Hoboken Public Schools. Algebra I Curriculum
 Hoboken Public Schools Algebra I Curriculum Algebra One HOBOKEN PUBLIC SCHOOLS Course Description Algebra I reflects the New Jersey learning standards at the high school level and is designed to give students
Hoboken Public Schools Algebra I Curriculum Algebra One HOBOKEN PUBLIC SCHOOLS Course Description Algebra I reflects the New Jersey learning standards at the high school level and is designed to give students
Processes. Criteria for Comparing Scheduling Algorithms
 1 Processes Scheduling Processes Scheduling Processes Don Porter Portions courtesy Emmett Witchel Each process has state, that includes its text and data, procedure call stack, etc. This state resides
1 Processes Scheduling Processes Scheduling Processes Don Porter Portions courtesy Emmett Witchel Each process has state, that includes its text and data, procedure call stack, etc. This state resides
Hoboken Public Schools. Project Lead The Way Curriculum Grade 8
 Hoboken Public Schools Project Lead The Way Curriculum Grade 8 Project Lead The Way HOBOKEN PUBLIC SCHOOLS Course Description PLTW Gateway s 9 units empower students to lead their own discovery. The hands-on
Hoboken Public Schools Project Lead The Way Curriculum Grade 8 Project Lead The Way HOBOKEN PUBLIC SCHOOLS Course Description PLTW Gateway s 9 units empower students to lead their own discovery. The hands-on
Support Vector Machines
 Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
Bribery in voting with CP-nets
 Ann Math Artif Intell (2013) 68:135 160 DOI 10.1007/s10472-013-9330-5 Bribery in voting with CP-nets Nicholas Mattei Maria Silvia Pini Francesca Rossi K. Brent Venable Published online: 7 February 2013
Ann Math Artif Intell (2013) 68:135 160 DOI 10.1007/s10472-013-9330-5 Bribery in voting with CP-nets Nicholas Mattei Maria Silvia Pini Francesca Rossi K. Brent Venable Published online: 7 February 2013
Classifier Evaluation and Selection. Review and Overview of Methods
 Classifier Evaluation and Selection Review and Overview of Methods Things to consider Ø Interpretation vs. Prediction Ø Model Parsimony vs. Model Error Ø Type of prediction task: Ø Decisions Interested
Classifier Evaluation and Selection Review and Overview of Methods Things to consider Ø Interpretation vs. Prediction Ø Model Parsimony vs. Model Error Ø Type of prediction task: Ø Decisions Interested
Electrical Engineering and Computer Science Department
 Electrical Engineering and Computer Science Department Technical Report NWU-EECS-08-5 July, 008 Internet Politics: Resist, Die, or Exploit? Leiwen Deng and Aleksandar Kuzmanovic Abstract In this paper,
Electrical Engineering and Computer Science Department Technical Report NWU-EECS-08-5 July, 008 Internet Politics: Resist, Die, or Exploit? Leiwen Deng and Aleksandar Kuzmanovic Abstract In this paper,
New Hampshire Secretary of State Electronic Ballot Counting Devices
 New Hampshire Secretary of State Electronic Ballot Counting Devices October, 2011 Statutory Requirements This article is to remind city/town Clerks and moderators about the statutory requirements for securing
New Hampshire Secretary of State Electronic Ballot Counting Devices October, 2011 Statutory Requirements This article is to remind city/town Clerks and moderators about the statutory requirements for securing
Louis M. Edwards Mathematics Super Bowl Valencia Community College -- April 30, 2004
 Practice Round 1. The overall average in an algebra class is described in the syllabus as a weighted average of homework, tests, and the final exam. The homework counts 10%, the three tests each count
Practice Round 1. The overall average in an algebra class is described in the syllabus as a weighted average of homework, tests, and the final exam. The homework counts 10%, the three tests each count
Subreddit Recommendations within Reddit Communities
 Subreddit Recommendations within Reddit Communities Vishnu Sundaresan, Irving Hsu, Daryl Chang Stanford University, Department of Computer Science ABSTRACT: We describe the creation of a recommendation
Subreddit Recommendations within Reddit Communities Vishnu Sundaresan, Irving Hsu, Daryl Chang Stanford University, Department of Computer Science ABSTRACT: We describe the creation of a recommendation
VOTING DYNAMICS IN INNOVATION SYSTEMS
 VOTING DYNAMICS IN INNOVATION SYSTEMS Voting in social and collaborative systems is a key way to elicit crowd reaction and preference. It enables the diverse perspectives of the crowd to be expressed and
VOTING DYNAMICS IN INNOVATION SYSTEMS Voting in social and collaborative systems is a key way to elicit crowd reaction and preference. It enables the diverse perspectives of the crowd to be expressed and
A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset
 A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset Sisi Xiong*, Feiyi Wang + and Qing Cao* *University of Tennessee Knoxville, Knoxville, TN, USA + Oak Ridge National Laboratory,
A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset Sisi Xiong*, Feiyi Wang + and Qing Cao* *University of Tennessee Knoxville, Knoxville, TN, USA + Oak Ridge National Laboratory,
Title: Adverserial Search AIMA: Chapter 5 (Sections 5.1, 5.2 and 5.3)
 B.Y. Choueiry 1 Instructor s notes #9 Title: dverserial Search IM: Chapter 5 (Sections 5.1, 5.2 and 5.3) Introduction to rtificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/ choueiry/f17-476-876
B.Y. Choueiry 1 Instructor s notes #9 Title: dverserial Search IM: Chapter 5 (Sections 5.1, 5.2 and 5.3) Introduction to rtificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/ choueiry/f17-476-876
PCGENESIS PAYROLL SYSTEM OPERATIONS GUIDE
 PCGENESIS PAYROLL SYSTEM OPERATIONS GUIDE 1/22/2009 Section I: Special Functions [Topic 1: Pay Schedule Processing, V2.1] Revision History Date Version Description Author 1/22/2009 2.1 08.04.00 Corrected
PCGENESIS PAYROLL SYSTEM OPERATIONS GUIDE 1/22/2009 Section I: Special Functions [Topic 1: Pay Schedule Processing, V2.1] Revision History Date Version Description Author 1/22/2009 2.1 08.04.00 Corrected
OPEN SOURCE CRYPTOCURRENCY
 23 April, 2018 OPEN SOURCE CRYPTOCURRENCY Document Filetype: PDF 325.26 KB 0 OPEN SOURCE CRYPTOCURRENCY Detailed information for OpenSourcecoin, including the OpenSourcecoin price and value, OpenSourcecoin
23 April, 2018 OPEN SOURCE CRYPTOCURRENCY Document Filetype: PDF 325.26 KB 0 OPEN SOURCE CRYPTOCURRENCY Detailed information for OpenSourcecoin, including the OpenSourcecoin price and value, OpenSourcecoin
JD Edwards EnterpriseOne Applications
 JD Edwards EnterpriseOne Applications One View Watchlists Implementation Guide Release 9.1 E39041-02 December 2013 JD Edwards EnterpriseOne Applications One View Watchlists Implementation Guide, Release
JD Edwards EnterpriseOne Applications One View Watchlists Implementation Guide Release 9.1 E39041-02 December 2013 JD Edwards EnterpriseOne Applications One View Watchlists Implementation Guide, Release
MATH4999 Capstone Projects in Mathematics and Economics Topic 3 Voting methods and social choice theory
 MATH4999 Capstone Projects in Mathematics and Economics Topic 3 Voting methods and social choice theory 3.1 Social choice procedures Plurality voting Borda count Elimination procedures Sequential pairwise
MATH4999 Capstone Projects in Mathematics and Economics Topic 3 Voting methods and social choice theory 3.1 Social choice procedures Plurality voting Borda count Elimination procedures Sequential pairwise
Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3)
 B.Y. Choueiry 1 Instructor s notes #5 Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3) Introduction to Artificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/~choueiry/f17-476-876
B.Y. Choueiry 1 Instructor s notes #5 Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3) Introduction to Artificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/~choueiry/f17-476-876
Random Forests. Gradient Boosting. and. Bagging and Boosting
 Random Forests and Gradient Boosting Bagging and Boosting The Bootstrap Sample and Bagging Simple ideas to improve any model via ensemble Bootstrap Samples Ø Random samples of your data with replacement
Random Forests and Gradient Boosting Bagging and Boosting The Bootstrap Sample and Bagging Simple ideas to improve any model via ensemble Bootstrap Samples Ø Random samples of your data with replacement
Case Study. MegaMatcher Accelerator
 MegaMatcher Accelerator Case Study Venezuela s New Biometric Voter Registration System Based on MegaMatcher biometric technology, the new system enrolls registered voters and verifies identity during local,
MegaMatcher Accelerator Case Study Venezuela s New Biometric Voter Registration System Based on MegaMatcher biometric technology, the new system enrolls registered voters and verifies identity during local,
GST 104: Cartographic Design Lab 6: Countries with Refugees and Internally Displaced Persons Over 1 Million Map Design
 GST 104: Cartographic Design Lab 6: Countries with Refugees and Internally Displaced Persons Over 1 Million Map Design Objective Utilize QGIS and Inkscape to Design a Chorolpleth Map Showing Refugees and
GST 104: Cartographic Design Lab 6: Countries with Refugees and Internally Displaced Persons Over 1 Million Map Design Objective Utilize QGIS and Inkscape to Design a Chorolpleth Map Showing Refugees and
Many Social Choice Rules
 Many Social Choice Rules 1 Introduction So far, I have mentioned several of the most commonly used social choice rules : pairwise majority rule, plurality, plurality with a single run off, the Borda count.
Many Social Choice Rules 1 Introduction So far, I have mentioned several of the most commonly used social choice rules : pairwise majority rule, plurality, plurality with a single run off, the Borda count.
Polydisciplinary Faculty of Larache Abdelmalek Essaadi University, MOROCCO 3 Department of Mathematics and Informatics
 International Journal of Pure and Applied Mathematics Volume 115 No. 4 2017, 801-812 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu doi: 10.12732/ijpam.v115i4.13
International Journal of Pure and Applied Mathematics Volume 115 No. 4 2017, 801-812 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu doi: 10.12732/ijpam.v115i4.13
M-Series, Actuator Overview. Machine Screw Cutaway. UNI-LIFT Machine Screw Actuators offer precise. 12
 M-, Actuator Overview UNI-LIFT Machine Screw Actuators offer precise positioning, uniform lifting speeds and capacity up to 250 tons. Standard model configurations include upright or inverted units with
M-, Actuator Overview UNI-LIFT Machine Screw Actuators offer precise positioning, uniform lifting speeds and capacity up to 250 tons. Standard model configurations include upright or inverted units with
Protocol to Check Correctness of Colorado s Risk-Limiting Tabulation Audit
 1 Public RLA Oversight Protocol Stephanie Singer and Neal McBurnett, Free & Fair Copyright Stephanie Singer and Neal McBurnett 2018 Version 1.0 One purpose of a Risk-Limiting Tabulation Audit is to improve
1 Public RLA Oversight Protocol Stephanie Singer and Neal McBurnett, Free & Fair Copyright Stephanie Singer and Neal McBurnett 2018 Version 1.0 One purpose of a Risk-Limiting Tabulation Audit is to improve
Homework 4 solutions
 Homework 4 solutions ASSIGNMENT: exercises 2, 3, 4, 8, and 17 in Chapter 2, (pp. 65 68). Solution to Exercise 2. A coalition that has exactly 12 votes is winning because it meets the quota. This coalition
Homework 4 solutions ASSIGNMENT: exercises 2, 3, 4, 8, and 17 in Chapter 2, (pp. 65 68). Solution to Exercise 2. A coalition that has exactly 12 votes is winning because it meets the quota. This coalition
ANALYSES OF JUVENILE CHINOOK SALMON AND STEELHEAD TRANSPORT FROM LOWER GRANITE AND LITTLE GOOSE DAMS, NOAA Fisheries
 ANALYSES OF JUVENILE CHINOOK SALMON AND STEELHEAD TRANSPORT FROM LOWER GRANITE AND LITTLE GOOSE DAMS, 1998-2008 NOAA Fisheries Northwest Fisheries Science Center Fish Ecology Division January 2010 Executive
ANALYSES OF JUVENILE CHINOOK SALMON AND STEELHEAD TRANSPORT FROM LOWER GRANITE AND LITTLE GOOSE DAMS, 1998-2008 NOAA Fisheries Northwest Fisheries Science Center Fish Ecology Division January 2010 Executive
CSCI211: Intro Objectives
 CSCI211: Intro Objectives Introduction to Algorithms, Analysis Course summary Reviewing proof techniques Jan 7, 2019 Sprenkle CSCI211 1 My Bio From Dallastown, PA B.S., Gettysburg College M.S., Duke University
CSCI211: Intro Objectives Introduction to Algorithms, Analysis Course summary Reviewing proof techniques Jan 7, 2019 Sprenkle CSCI211 1 My Bio From Dallastown, PA B.S., Gettysburg College M.S., Duke University
CS 5523 Operating Systems: Synchronization in Distributed Systems
 CS 5523 Operating Systems: Synchronization in Distributed Systems Instructor: Dr. Tongping Liu Thank Dr. Dakai Zhu and Dr. Palden Lama for providing their slides. Outline Physical clock/time in distributed
CS 5523 Operating Systems: Synchronization in Distributed Systems Instructor: Dr. Tongping Liu Thank Dr. Dakai Zhu and Dr. Palden Lama for providing their slides. Outline Physical clock/time in distributed
arxiv: v2 [math.ho] 12 Oct 2018
![arxiv: v2 [math.ho] 12 Oct 2018 arxiv: v2 [math.ho] 12 Oct 2018](/thumbs/92/109875862.jpg) PHRAGMÉN S AND THIELE S ELECTION METHODS arxiv:1611.08826v2 [math.ho] 12 Oct 2018 SVANTE JANSON Abstract. The election methods introduced in 1894 1895 by Phragmén and Thiele, and their somewhat later versions
PHRAGMÉN S AND THIELE S ELECTION METHODS arxiv:1611.08826v2 [math.ho] 12 Oct 2018 SVANTE JANSON Abstract. The election methods introduced in 1894 1895 by Phragmén and Thiele, and their somewhat later versions
B-Series Section Overview. Ball Screw Cutaway. UNI-LIFT Ball Screw Actuators provide high. 34
 B- Section Overview UNI-LIFT Actuators provide high efficiency and high speed in a linear positioning package up to 100 tons. The low friction ball screw and nut design provides longer life at load and
B- Section Overview UNI-LIFT Actuators provide high efficiency and high speed in a linear positioning package up to 100 tons. The low friction ball screw and nut design provides longer life at load and
Social welfare functions
 Social welfare functions We have defined a social choice function as a procedure that determines for each possible profile (set of preference ballots) of the voters the winner or set of winners for the
Social welfare functions We have defined a social choice function as a procedure that determines for each possible profile (set of preference ballots) of the voters the winner or set of winners for the
Overview. Ø Neural Networks are considered black-box models Ø They are complex and do not provide much insight into variable relationships
 Neural Networks Overview Ø s are considered black-box models Ø They are complex and do not provide much insight into variable relationships Ø They have the potential to model very complicated patterns
Neural Networks Overview Ø s are considered black-box models Ø They are complex and do not provide much insight into variable relationships Ø They have the potential to model very complicated patterns
Andreas Fring. Basic Operations
 Basic Operations Creating a workbook: The first action should always be to give your workbook a name and save it on your computer. Go for this to the menu bar and select by left mouse click (LC): Ø File
Basic Operations Creating a workbook: The first action should always be to give your workbook a name and save it on your computer. Go for this to the menu bar and select by left mouse click (LC): Ø File
HASHGRAPH CONSENSUS: DETAILED EXAMPLES
 HASHGRAPH CONSENSUS: DETAILED EXAMPLES LEEMON BAIRD BAIRD@SWIRLDS.COM DECEMBER 11, 2016 SWIRLDS TECH REPORT SWIRLDS-TR-2016-02 ABSTRACT: The Swirlds hashgraph consensus algorithm is explained through a
HASHGRAPH CONSENSUS: DETAILED EXAMPLES LEEMON BAIRD BAIRD@SWIRLDS.COM DECEMBER 11, 2016 SWIRLDS TECH REPORT SWIRLDS-TR-2016-02 ABSTRACT: The Swirlds hashgraph consensus algorithm is explained through a
IC Chapter 15. Ballot Card and Electronic Voting Systems; Additional Standards and Procedures for Approving System Changes
 IC 3-11-15 Chapter 15. Ballot Card and Electronic Voting Systems; Additional Standards and Procedures for Approving System Changes IC 3-11-15-1 Applicability of chapter Sec. 1. Except as otherwise provided,
IC 3-11-15 Chapter 15. Ballot Card and Electronic Voting Systems; Additional Standards and Procedures for Approving System Changes IC 3-11-15-1 Applicability of chapter Sec. 1. Except as otherwise provided,
Genetic Algorithms with Elitism-Based Immigrants for Changing Optimization Problems
 Genetic Algorithms with Elitism-Based Immigrants for Changing Optimization Problems Shengxiang Yang Department of Computer Science, University of Leicester University Road, Leicester LE1 7RH, United Kingdom
Genetic Algorithms with Elitism-Based Immigrants for Changing Optimization Problems Shengxiang Yang Department of Computer Science, University of Leicester University Road, Leicester LE1 7RH, United Kingdom
Introduction to Path Analysis: Multivariate Regression
 Introduction to Path Analysis: Multivariate Regression EPSY 905: Multivariate Analysis Spring 2016 Lecture #7 March 9, 2016 EPSY 905: Multivariate Regression via Path Analysis Today s Lecture Multivariate
Introduction to Path Analysis: Multivariate Regression EPSY 905: Multivariate Analysis Spring 2016 Lecture #7 March 9, 2016 EPSY 905: Multivariate Regression via Path Analysis Today s Lecture Multivariate
Chief Electoral Officer Directives for the Counting of Ballots (Elections Act, R.S.N.B. 1973, c.e-3, ss.5.2(1), s.87.63, 87.64, 91.1, and 91.
 Chief Electoral Officer Directives for the Counting of Ballots (Elections Act, R.S.N.B. 1973, c.e-3, ss.5.2(1), s.87.63, 87.64, 91.1, and 91.2) P 01 403 (2016-09-01) BALLOT COUNT USING TABULATION MACHINES
Chief Electoral Officer Directives for the Counting of Ballots (Elections Act, R.S.N.B. 1973, c.e-3, ss.5.2(1), s.87.63, 87.64, 91.1, and 91.2) P 01 403 (2016-09-01) BALLOT COUNT USING TABULATION MACHINES
WORLD INTELLECTUAL PROPERTY ORGANIZATION GENEVA SPECIAL UNION FOR THE INTERNATIONAL PATENT CLASSIFICATION (IPC UNION) AD HOC IPC REFORM WORKING GROUP
 WIPO IPC/REF/7/3 ORIGINAL: English DATE: May 17, 2002 WORLD INTELLECTUAL PROPERTY ORGANIZATION GENEVA E SPECIAL UNION FOR THE INTERNATIONAL PATENT CLASSIFICATION (IPC UNION) AD HOC IPC REFORM WORKING GROUP
WIPO IPC/REF/7/3 ORIGINAL: English DATE: May 17, 2002 WORLD INTELLECTUAL PROPERTY ORGANIZATION GENEVA E SPECIAL UNION FOR THE INTERNATIONAL PATENT CLASSIFICATION (IPC UNION) AD HOC IPC REFORM WORKING GROUP
COULD SIMULATION OPTIMIZATION HAVE PREVENTED 2012 CENTRAL FLORIDA ELECTION LINES?
 Proceedings of the 2013 Winter Simulation Conference R. Pasupathy, S.-H. Kim, A. Tolk, R. Hill, and M. E. Kuhl, eds. COULD SIMULATION OPTIMIZATION HAVE PREVENTED 2012 CENTRAL FLORIDA ELECTION LINES? Jingsheng
Proceedings of the 2013 Winter Simulation Conference R. Pasupathy, S.-H. Kim, A. Tolk, R. Hill, and M. E. Kuhl, eds. COULD SIMULATION OPTIMIZATION HAVE PREVENTED 2012 CENTRAL FLORIDA ELECTION LINES? Jingsheng
Iowa Voting Series, Paper 6: An Examination of Iowa Absentee Voting Since 2000
 Department of Political Science Publications 5-1-2014 Iowa Voting Series, Paper 6: An Examination of Iowa Absentee Voting Since 2000 Timothy M. Hagle University of Iowa 2014 Timothy M. Hagle Comments This
Department of Political Science Publications 5-1-2014 Iowa Voting Series, Paper 6: An Examination of Iowa Absentee Voting Since 2000 Timothy M. Hagle University of Iowa 2014 Timothy M. Hagle Comments This
Case 4:16-cv Document 11 Filed in TXSD on 08/15/16 Page 1 of 32 IN UNITED STATES DISTRICT COURT FOR THE SOUTHERN DISTRICT OF TEXAS
 Case 4:16-cv-00936 Document 11 Filed in TXSD on 08/15/16 Page 1 of 32 IN UNITED STATES DISTRICT COURT FOR THE SOUTHERN DISTRICT OF TEXAS IKAN INTERNATIONAL, ) CIVIL ACTION NO. LLC ) ) 4:16 - CV - 00936
Case 4:16-cv-00936 Document 11 Filed in TXSD on 08/15/16 Page 1 of 32 IN UNITED STATES DISTRICT COURT FOR THE SOUTHERN DISTRICT OF TEXAS IKAN INTERNATIONAL, ) CIVIL ACTION NO. LLC ) ) 4:16 - CV - 00936
Photon Identification in the Future. Andrew Askew Florida State University
 Photon Identification in the Future Andrew Askew Florida State University WHAT IS IN STORE? Ø Predictions are difficult to make, especially about the future. Yogi Berra Ø Everything I ve showed you here
Photon Identification in the Future Andrew Askew Florida State University WHAT IS IN STORE? Ø Predictions are difficult to make, especially about the future. Yogi Berra Ø Everything I ve showed you here
ForeScout Extended Module for McAfee epolicy Orchestrator
 ForeScout Extended Module for McAfee epolicy Orchestrator Version 3.1 Table of Contents About McAfee epolicy Orchestrator (epo) Integration... 4 Use Cases... 4 Additional McAfee epo Documentation... 4
ForeScout Extended Module for McAfee epolicy Orchestrator Version 3.1 Table of Contents About McAfee epolicy Orchestrator (epo) Integration... 4 Use Cases... 4 Additional McAfee epo Documentation... 4
The mathematics of voting, power, and sharing Part 1
 The mathematics of voting, power, and sharing Part 1 Voting systems A voting system or a voting scheme is a way for a group of people to select one from among several possibilities. If there are only two
The mathematics of voting, power, and sharing Part 1 Voting systems A voting system or a voting scheme is a way for a group of people to select one from among several possibilities. If there are only two
MOS Exams Objective Mapping
 Core 1 Create and Manage Worksheets and Workbooks Core 1.1 Create Worksheets and Workbooks Core 1.1.1 create a workbook Level 1 Chapter 2 Topic A Core 1.1.2 import data from a delimited text file Level
Core 1 Create and Manage Worksheets and Workbooks Core 1.1 Create Worksheets and Workbooks Core 1.1.1 create a workbook Level 1 Chapter 2 Topic A Core 1.1.2 import data from a delimited text file Level
NELIS NEVADA ELECTRONIC LEGISLATIVE INFORMATION SYSTEM 79TH (2017) SESSION
 NELIS NEVADA ELECTRONIC LEGISLATIVE INFORMATION SYSTEM 79TH (2017) SESSION LEGISLATIVE COUNSEL BUREAU: INFORMATION TECHNOLOGY SERVICES 1/10/2017 Table of Contents Introduction... 1 NELIS Home... 1 Register
NELIS NEVADA ELECTRONIC LEGISLATIVE INFORMATION SYSTEM 79TH (2017) SESSION LEGISLATIVE COUNSEL BUREAU: INFORMATION TECHNOLOGY SERVICES 1/10/2017 Table of Contents Introduction... 1 NELIS Home... 1 Register
Please see my attached comments. Thank you.
 From: Sent: To: Subject: Attachments: MJ Schillaci Friday, July 12, 2013 12:38 PM Public UVS Panel public comment on Voting System s UVSs-Public.doc Please see my attached
From: Sent: To: Subject: Attachments: MJ Schillaci Friday, July 12, 2013 12:38 PM Public UVS Panel public comment on Voting System s UVSs-Public.doc Please see my attached
Tengyu Ma Facebook AI Research. Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford)
 Tengyu Ma Facebook AI Research Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford) Ø Over-parameterization: # parameters # examples Ø a set of parameters that can Ø fit to training
Tengyu Ma Facebook AI Research Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford) Ø Over-parameterization: # parameters # examples Ø a set of parameters that can Ø fit to training
Super-Simple Simultaneous Single-Ballot Risk-Limiting Audits
 Super-Simple Simultaneous Single-Ballot Risk-Limiting Audits Philip B. Stark Department of Statistics University of California, Berkeley Abstract Simultaneous risk-limiting audits of a collection of contests
Super-Simple Simultaneous Single-Ballot Risk-Limiting Audits Philip B. Stark Department of Statistics University of California, Berkeley Abstract Simultaneous risk-limiting audits of a collection of contests
