Priority Queues & Heaps
|
|
|
- Silas Strickland
- 6 years ago
- Views:
Transcription
1 Priority Queues & Heaps Chapter 8-1 -
2 The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List Priority Queue Abstract Sequential List Array List Vector Stack Linked List - 2 -
3 The Priority Queue Class Ø Based on priority heap Ø Elements are prioritized based either on q natural order q a comparator, passed to the constructor. Ø Provides an iterator - 3 -
4 Priority Queue ADT Ø A priority queue stores a collection of entries Ø Each entry is a pair (key, value) Ø Main methods of the Priority Queue ADT q insert(k, x) inserts an entry with key k and value x q removemin() removes and returns the entry with smallest key Ø Additional methods q min() returns, but does not remove, an entry with smallest key q size(), isempty() Ø Applications: q Process scheduling q Standby flyers - 4 -
5 Total Order Relations Ø Keys in a priority queue can be arbitrary objects on which an order is defined Ø Two distinct entries in a priority queue can have the same key Ø Mathematical concept of total order relation q Reflexive property: x x q Antisymmetric property: x y y x è x = y q Transitive property: x y y z è x z - -
6 Entry ADT Ø An entry in a priority queue is simply a keyvalue pair Ø Methods: q getkey(): returns the key for this entry q getvalue(): returns the value for this entry Ø As a Java interface: /** * Interface for a key-value * pair entry **/ public interface Entry { public Object getkey(); public Object getvalue(); } - -
7 Comparator ADT Ø A comparator encapsulates the action of comparing two objects according to a given total order relation Ø A generic priority queue uses an auxiliary comparator Ø The comparator is external to the keys being compared Ø When the priority queue needs to compare two keys, it uses its comparator Ø The primary method of the Comparator ADT: q compare(a, b): ² Returns an integer i such that v i < 0 if a < b v i = 0 if a = b v i > 0 if a > b v an error occurs if a and b cannot be compared
8 Example Comparator /** Comparator for 2D points under the standard lexicographic order. */ public class Lexicographic implements Comparator { } } int xa, ya, xb, yb; public int compare(object a, Object b) throws ClassCastException { xa = ((Point2D) a).getx(); ya = ((Point2D) a).gety(); xb = ((Point2D) b).getx(); yb = ((Point2D) b).gety(); if (xa!= xb) else return (xa - xb); return (ya - yb); /** Class representing a point in the plane with integer coordinates */ public class Point2D { } } protected int xc, yc; // coordinates public Point2D(int x, int y) { xc = x; yc = y; public int getx() { } return xc; public int gety() { } return yc; - 8 -
9 Sequence-based Priority Queue Ø Implementation with an unsorted list Ø Implementation with a sorted list Ø Performance: q insert takes O(1) time since we can insert the item at the beginning or end of the sequence q removemin and min take O(n) time since we have to traverse the entire sequence to find the smallest key Ø Performance: q insert takes O(n) time since we have to find the right place to insert the item q removemin and min take O (1) time, since the smallest key is at the beginning Is this tradeoff inevitable? - 9 -
10 Heaps Ø Goal: q O(log n) insertion q O(log n) removal Ø Remember that O(log n) is almost as good as O(1)! q e.g., n = 1,000,000,000 à log n 30 Ø There are min heaps and max heaps. We will assume min heaps
11 Min Heaps Ø A min heap is a binary tree storing keys at its nodes and satisfying the following properties: q Heap-order: for every internal node v other than the root ² key(v) key(parent(v)) q (Almost) complete binary tree: let h be the height of the heap ² for i = 0,, h 1, there are 2 i nodes of depth i ² at depth h 1 v the internal nodes are to the left of the external nodes v Only the rightmost internal node may have a single child q The last node of a heap is the rightmost node of depth h
12 Height of a Heap Ø Theorem: A heap storing n keys has height O(log n) Proof: (we apply the complete binary tree property) q Let h be the height of a heap storing n keys q Since there are 2 i keys at depth i = 0,, h 1 and at least one key at depth h, we have n h q Thus, n 2 h, i.e., h log n depth 0 1 h 1 h keys h
13 Heaps and Priority Queues Ø We can use a heap to implement a priority queue Ø We store a (key, element) item at each internal node Ø We keep track of the position of the last node Ø For simplicity, we will typically show only the keys in the pictures (2, Sue) (, Pat) (, Mark) (9, Jeff) (7, Anna)
14 Insertion into a Heap Ø Method insert of the priority queue ADT involves inserting a new entry with key k into the heap Ø The insertion algorithm consists of two steps q Store the new entry at the next available location q Restore the heap-order property 2 z 9 7 new node 2 z
15 Upheap Ø After the insertion of a new key k, the heap-order property may be violated Ø Algorithm upheap restores the heap-order property by swapping k along an upward path from the insertion node Ø Upheap terminates when the key k reaches the root or a node whose parent has a key smaller than or equal to k Ø Since a heap has height O(log n), upheap runs in O(log n) time
16 Removal from a Heap Ø Method removemin of the priority queue ADT corresponds to the removal of the root key from the heap Ø The removal algorithm consists of three steps q Replace the root key with the key of the last node w q Remove w q Restore the heap-order property 9 7 w w 7 2 last node 9 new last node - 1 -
17 Downheap Ø After replacing the root key with the key k of the last node, the heap-order property may be violated Ø Algorithm downheap restores the heap-order property by swapping key k along a downward path from the root Ø Note that there are, in general, many possible downward paths which one do we choose??? 7 w
18 Downheap Ø We select the downward path through the minimum-key nodes. Ø Downheap terminates when key k reaches a leaf or a node whose children have keys greater than or equal to k Ø Since a heap has height O(log n), downheap runs in O(log n) time 7 w 7 w
19 Array-based Heap Implementation Ø We can represent a heap with n keys by means of an array of length n + 1 Ø Links between nodes are not explicitly stored 2 Ø The cell at rank 0 is not used Ø The root is stored at rank 1. Ø For the node at rank i q the left child is at rank 2i q the right child is at rank 2i q the parent is at rank floor(i/2) q if 2i + 1 > n, the node has no right child q if 2i > n, the node is a leaf
20 Merging Two Heaps Ø We are given two heaps and a new key k Ø We create a new heap with the root node storing k and with the two heaps as subtrees Ø We perform downheap to restore the heaporder property
21 Bottom-up Heap Construction Ø We can construct a heap storing n keys using a bottom-up construction with log n phases 2 i 1 2 i 1 Ø In phase i, pairs of heaps with 2 i 1 keys are merged into heaps with 2 i+1 1 keys 2 i
22 Example
23 Example (contd.)
24 Example (contd.)
25 Example (end)
26 Analysis Ø We visualize the worst-case time of a downheap with a proxy path that goes first right and then repeatedly goes left until the bottom of the heap (this path may differ from the actual downheap path) Ø Since each node is traversed by at most two proxy paths, the total number of nodes of the proxy paths is O(n) Ø Thus, bottom-up heap construction runs in O(n) time Ø Bottom-up heap construction is faster than n successive insertions (running time?)
27 Bottom-Up Heap Construction Ø Uses downheap to reorganize the tree from bottom to top to make it a heap. Ø Can be written concisely in either recursive or iterative form
28 Iterative MakeHeap MakeHeap(A, n) <pre-cond>:a[1 n] is a balanced binary tree <post-cond>:a[1 n] is a heap for i! " n / 2$ # % downto 1 < LI >: All subtrees rooted at i + 1 n are heaps DownHeap(A, i, n)
29 Recursive MakeHeap Get help from friends
30 Recursive MakeHeap MakeHeap(A, i, n) Invoke as MakeHeap (A, 1, n) <pre-cond>:a[i n] is a balanced binary tree <post-cond>:the subtree rooted at i is a heap if i! " n / 4$ # % then MakeHeap(A, LEFT (i), n) MakeHeap(A, RIGHT (i), n) Downheap(A, i, n) Running time: T(n) = 2T(n/2) + log(n) i = (n) n/4 is grandparent of n n/2 is parent of n n
31 Iterative vs Recursive MakeHeap Ø Recursive and Iterative MakeHeap do essentially the same thing: Heapify from bottom to top. Ø Difference: q Recursive is depth-first q Iterative is breadth-first
32 Adaptable Priority 3 a Queues g 4 e
33 Recall the Entry and Priority Queue ADTs Ø An entry stores a (key, value) pair within a data structure Ø Methods of the entry ADT: q getkey(): returns the key associated with this entry q getvalue(): returns the value paired with the key associated with this entry Ø Priority Queue ADT: q insert(k, x) inserts an entry with key k and value x q removemin() removes and returns the entry with smallest key q min() returns, but does not remove, an entry with smallest key q size(), isempty()
34 Motivating Example Ø Suppose we have an online trading system where orders to purchase and sell a given stock are stored in two priority queues (one for sell orders and one for buy orders) as (p,s) entries: q The key, p, of an order is the price q The value, s, for an entry is the number of shares q A buy order (p,s) is executed when a sell order (p,s ) with price p <p is added (the execution is complete if s >s) q A sell order (p,s) is executed when a buy order (p,s ) with price p >p is added (the execution is complete if s >s) Ø What if someone wishes to cancel their order before it executes? Ø What if someone wishes to update the price or number of shares for their order?
35 Additional Methods of the Adaptable Priority Queue ADT Ø remove(e): Remove from P and return entry e. Ø replacekey(e,k): Replace with k and return the old key; an error condition occurs if k is invalid (that is, k cannot be compared with other keys). Ø replacevalue(e,x): Replace with x and return the old value
36 Example Operation Output P insert(,a) e 1 (,A) insert(3,b) e 2 (3,B),(,A) insert(7,c) e 3 (3,B),(,A),(7,C) min() e 2 (3,B),(,A),(7,C) key(e 2 ) 3 (3,B),(,A),(7,C) remove(e 1 ) e 1 (3,B),(7,C) replacekey(e 2,9) 3 (7,C),(9,B) replacevalue(e 3,D) C (7,D),(9,B) remove(e 2 ) e 2 (7,D) - 3 -
37 Locating Entries Ø In order to implement the operations remove(e), replacekey(e,k), and replacevalue(e,x), we need fast ways of locating an entry e in a priority queue. Ø We can always just search the entire data structure to find an entry e, but there are better ways for locating entries
38 Location-Aware Entries Ø A location-aware entry identifies and tracks the location of its (key, value) object within a data structure
39 List Implementation Ø A location-aware list entry is an object storing q key q value q position (or rank) of the item in the list Ø In turn, the position (or array cell) stores the entry Ø Back pointers (or ranks) are updated during swaps header nodes/positions trailer 2 c 4 a d 8 b entries
40 Heap Implementation Ø A location-aware heap entry is an object storing q key 2 d q value q position of the entry in the underlying heap Ø In turn, each heap position stores an entry Ø Back pointers are updated during entry swaps 4 a b 8 g e 9 c
41 Performance Ø Times better than those achievable without location-aware entries are highlighted in red: Method Unsorted List Sorted List Heap size, isempty O(1) O(1) O(1) insert O(1) O(n) O(log n) min O(n) O(1) O(1) removemin O(n) O(1) O(log n) remove O(1) O(1) O(log n) replacekey O(1) O(n) O(log n) replacevalue O(1) O(1) O(1)
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue class of the Java Collections Framework Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues
Priority Queues & Heaps
 Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Priority Queues & Heaps - 1 - Outline Ø The Priority Queue ADT Ø Total orderings, the Comparable Interface and the Comparator Class Ø Heaps Ø Adaptable Priority Queues - 2 - Outcomes Ø By understanding
Midterm Review. EECS 2011 Prof. J. Elder - 1 -
 Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review. EECS 2011 Prof. J. Elder - 1 -
 Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Midterm Review - 1 - Topics on the Midterm Ø Data Structures & Object-Oriented Design Ø Run-Time Analysis Ø Linear Data Structures Ø The Java Collections Framework Ø Recursion Ø Trees Ø Priority Queues
Comparison Sorts. EECS 2011 Prof. J. Elder - 1 -
 Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Comparison Sorts - 1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Search Trees. Chapter 10. CSE 2011 Prof. J. Elder Last Updated: :51 PM
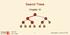 Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Search Trees Chapter 1 < 6 2 > 1 4 = 8 9-1 - Outline Ø Binary Search Trees Ø AVL Trees Ø Splay Trees - 2 - Binary Search Trees Ø A binary search tree is a binary tree storing key-value entries at its internal
Maps, Hash Tables and Dictionaries
 Maps, Hash Tables and Dictionaries Chapter 9-1 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 2 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 3 -
Maps, Hash Tables and Dictionaries Chapter 9-1 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 2 - Outline Ø Maps Ø Hashing Ø Dictionaries Ø Ordered Maps & Dictionaries - 3 -
ECE250: Algorithms and Data Structures Trees
 ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
ECE250: Algorithms and Data Structures Trees Ladan Tahvildari, PEng, SMIEEE Professor Software Technologies Applied Research (STAR) Group Dept. of Elect. & Comp. Eng. University of Waterloo Materials from
Maps and Hash Tables. EECS 2011 Prof. J. Elder - 1 -
 Maps and Hash Tables - 1 - Outline Ø Maps Ø Hashing Ø Multimaps Ø Ordered Maps - 2 - Learning Outcomes Ø By understanding this lecture, you should be able to: Ø Outline the ADT for a map and a multimap
Maps and Hash Tables - 1 - Outline Ø Maps Ø Hashing Ø Multimaps Ø Ordered Maps - 2 - Learning Outcomes Ø By understanding this lecture, you should be able to: Ø Outline the ADT for a map and a multimap
COMP : DATA STRUCTURES 2/27/14. Are binary trees satisfying two additional properties:
 BINARY HEAPS Two Additional Properties 9 Binary Heaps Are binary trees satisfying two additional properties: Ø Structure property: Levels are filled in order, left to right Also known as complete binary
BINARY HEAPS Two Additional Properties 9 Binary Heaps Are binary trees satisfying two additional properties: Ø Structure property: Levels are filled in order, left to right Also known as complete binary
Chapter 8: Recursion
 Chapter 8: Recursion Presentation slides for Java Software Solutions for AP* Computer Science 3rd Edition by John Lewis, William Loftus, and Cara Cocking Java Software Solutions is published by Addison-Wesley
Chapter 8: Recursion Presentation slides for Java Software Solutions for AP* Computer Science 3rd Edition by John Lewis, William Loftus, and Cara Cocking Java Software Solutions is published by Addison-Wesley
File Systems: Fundamentals
 File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
File Systems: Fundamentals 1 Files What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type, location, size, protection, creator,
Notes for Session 7 Basic Voting Theory and Arrow s Theorem
 Notes for Session 7 Basic Voting Theory and Arrow s Theorem We follow up the Impossibility (Session 6) of pooling expert probabilities, while preserving unanimities in both unconditional and conditional
Notes for Session 7 Basic Voting Theory and Arrow s Theorem We follow up the Impossibility (Session 6) of pooling expert probabilities, while preserving unanimities in both unconditional and conditional
CS 5523: Operating Systems
 Lecture1: OS Overview CS 5523: Operating Systems Instructor: Dr Tongping Liu Midterm Exam: Oct 2, 2017, Monday 7:20pm 8:45pm Operating System: what is it?! Evolution of Computer Systems and OS Concepts
Lecture1: OS Overview CS 5523: Operating Systems Instructor: Dr Tongping Liu Midterm Exam: Oct 2, 2017, Monday 7:20pm 8:45pm Operating System: what is it?! Evolution of Computer Systems and OS Concepts
Uninformed search. Lirong Xia
 Uninformed search Lirong Xia Spring, 2017 Today s schedule ØRational agents ØSearch problems State space graph: modeling the problem Search trees: scratch paper for solution ØUninformed search Depth first
Uninformed search Lirong Xia Spring, 2017 Today s schedule ØRational agents ØSearch problems State space graph: modeling the problem Search trees: scratch paper for solution ØUninformed search Depth first
Estimating the Margin of Victory for Instant-Runoff Voting
 Estimating the Margin of Victory for Instant-Runoff Voting David Cary Abstract A general definition is proposed for the margin of victory of an election contest. That definition is applied to Instant Runoff
Estimating the Margin of Victory for Instant-Runoff Voting David Cary Abstract A general definition is proposed for the margin of victory of an election contest. That definition is applied to Instant Runoff
Optimization Strategies
 Global Memory Access Pattern and Control Flow Objectives Ø Ø Global Memory Access Pattern (Coalescing) Ø Control Flow (Divergent branch) Copyright 2013 by Yong Cao, Referencing UIUC ECE498AL Course Notes
Global Memory Access Pattern and Control Flow Objectives Ø Ø Global Memory Access Pattern (Coalescing) Ø Control Flow (Divergent branch) Copyright 2013 by Yong Cao, Referencing UIUC ECE498AL Course Notes
TAFTW (Take Aways for the Week) APT Quiz and Markov Overview. Comparing objects and tradeoffs. From Comparable to TreeMap/Sort
 TAFTW (Take Aways for the Week) Graded work this week: Ø APT Quiz, details and overview Ø Markov assignment, details and overview Concepts: Empirical and Analytical Analysis Ø Algorithms and Data Structures
TAFTW (Take Aways for the Week) Graded work this week: Ø APT Quiz, details and overview Ø Markov assignment, details and overview Concepts: Empirical and Analytical Analysis Ø Algorithms and Data Structures
A Calculus for End-to-end Statistical Service Guarantees
 A Calculus for End-to-end Statistical Service Guarantees Technical Report: University of Virginia, CS-2001-19 (2nd revised version) Almut Burchard Ý Jörg Liebeherr Stephen Patek Ý Department of Mathematics
A Calculus for End-to-end Statistical Service Guarantees Technical Report: University of Virginia, CS-2001-19 (2nd revised version) Almut Burchard Ý Jörg Liebeherr Stephen Patek Ý Department of Mathematics
Event Based Sequential Program Development: Application to Constructing a Pointer Program
 Event Based Sequential Program Development: Application to Constructing a Pointer Program Jean-Raymond Abrial Consultant, Marseille, France jr@abrial.org Abstract. In this article, I present an event approach
Event Based Sequential Program Development: Application to Constructing a Pointer Program Jean-Raymond Abrial Consultant, Marseille, France jr@abrial.org Abstract. In this article, I present an event approach
Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3)
 B.Y. Choueiry 1 Instructor s notes #5 Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3) Introduction to Artificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/~choueiry/f17-476-876
B.Y. Choueiry 1 Instructor s notes #5 Title: Solving Problems by Searching AIMA: Chapter 3 (Sections 3.1, 3.2 and 3.3) Introduction to Artificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/~choueiry/f17-476-876
Constraint satisfaction problems. Lirong Xia
 Constraint satisfaction problems Lirong Xia Spring, 2017 Project 1 Ø You can use Windows Ø Read the instruction carefully, make sure you understand the goal search for YOUR CODE HERE Ø Ask and answer questions
Constraint satisfaction problems Lirong Xia Spring, 2017 Project 1 Ø You can use Windows Ø Read the instruction carefully, make sure you understand the goal search for YOUR CODE HERE Ø Ask and answer questions
Subreddit Recommendations within Reddit Communities
 Subreddit Recommendations within Reddit Communities Vishnu Sundaresan, Irving Hsu, Daryl Chang Stanford University, Department of Computer Science ABSTRACT: We describe the creation of a recommendation
Subreddit Recommendations within Reddit Communities Vishnu Sundaresan, Irving Hsu, Daryl Chang Stanford University, Department of Computer Science ABSTRACT: We describe the creation of a recommendation
Text UI. Data Store Ø Example of a backend to a real Could add a different user interface. Good judgment comes from experience
 Reviewing Lab 10 Text UI Created two classes Ø Used one class within another class Ø Tested them Graphical UI Backend Data Store Ø Example of a backend to a real applica@on Could add a different user interface
Reviewing Lab 10 Text UI Created two classes Ø Used one class within another class Ø Tested them Graphical UI Backend Data Store Ø Example of a backend to a real applica@on Could add a different user interface
Mathematics and Social Choice Theory. Topic 4 Voting methods with more than 2 alternatives. 4.1 Social choice procedures
 Mathematics and Social Choice Theory Topic 4 Voting methods with more than 2 alternatives 4.1 Social choice procedures 4.2 Analysis of voting methods 4.3 Arrow s Impossibility Theorem 4.4 Cumulative voting
Mathematics and Social Choice Theory Topic 4 Voting methods with more than 2 alternatives 4.1 Social choice procedures 4.2 Analysis of voting methods 4.3 Arrow s Impossibility Theorem 4.4 Cumulative voting
Contents. Bibliography 121. Index 123
 Contents 5 Advanced Data Types page 2 5.1 Sparse Arrays: Dictionary Arrays, Hashing Arrays, and Maps 2 5.2 The Implementation of the Data Type Map 14 5.3 Dictionaries and Sets 27 5.4 Priority Queues 28
Contents 5 Advanced Data Types page 2 5.1 Sparse Arrays: Dictionary Arrays, Hashing Arrays, and Maps 2 5.2 The Implementation of the Data Type Map 14 5.3 Dictionaries and Sets 27 5.4 Priority Queues 28
Lecture 6 Cryptographic Hash Functions
 Lecture 6 Cryptographic Hash Functions 1 Purpose Ø CHF one of the most important tools in modern cryptography and security Ø In crypto, CHF instantiates a Random Oracle paradigm Ø In security, used in
Lecture 6 Cryptographic Hash Functions 1 Purpose Ø CHF one of the most important tools in modern cryptography and security Ø In crypto, CHF instantiates a Random Oracle paradigm Ø In security, used in
Complexity of Manipulating Elections with Few Candidates
 Complexity of Manipulating Elections with Few Candidates Vincent Conitzer and Tuomas Sandholm Computer Science Department Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 {conitzer, sandholm}@cs.cmu.edu
Complexity of Manipulating Elections with Few Candidates Vincent Conitzer and Tuomas Sandholm Computer Science Department Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 {conitzer, sandholm}@cs.cmu.edu
Voting. Suppose that the outcome is determined by the mean of all voter s positions.
 Voting Suppose that the voters are voting on a single-dimensional issue. (Say 0 is extreme left and 100 is extreme right for example.) Each voter has a favorite point on the spectrum and the closer the
Voting Suppose that the voters are voting on a single-dimensional issue. (Say 0 is extreme left and 100 is extreme right for example.) Each voter has a favorite point on the spectrum and the closer the
Cluster Analysis. (see also: Segmentation)
 Cluster Analysis (see also: Segmentation) Cluster Analysis Ø Unsupervised: no target variable for training Ø Partition the data into groups (clusters) so that: Ø Observations within a cluster are similar
Cluster Analysis (see also: Segmentation) Cluster Analysis Ø Unsupervised: no target variable for training Ø Partition the data into groups (clusters) so that: Ø Observations within a cluster are similar
Manipulating Two Stage Voting Rules
 Manipulating Two Stage Voting Rules Nina Narodytska and Toby Walsh Abstract We study the computational complexity of computing a manipulation of a two stage voting rule. An example of a two stage voting
Manipulating Two Stage Voting Rules Nina Narodytska and Toby Walsh Abstract We study the computational complexity of computing a manipulation of a two stage voting rule. An example of a two stage voting
Title: Adverserial Search AIMA: Chapter 5 (Sections 5.1, 5.2 and 5.3)
 B.Y. Choueiry 1 Instructor s notes #9 Title: dverserial Search IM: Chapter 5 (Sections 5.1, 5.2 and 5.3) Introduction to rtificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/ choueiry/f17-476-876
B.Y. Choueiry 1 Instructor s notes #9 Title: dverserial Search IM: Chapter 5 (Sections 5.1, 5.2 and 5.3) Introduction to rtificial Intelligence CSCE 476-876, Fall 2017 URL: www.cse.unl.edu/ choueiry/f17-476-876
Dictatorships Are Not the Only Option: An Exploration of Voting Theory
 Dictatorships Are Not the Only Option: An Exploration of Voting Theory Geneva Bahrke May 17, 2014 Abstract The field of social choice theory, also known as voting theory, examines the methods by which
Dictatorships Are Not the Only Option: An Exploration of Voting Theory Geneva Bahrke May 17, 2014 Abstract The field of social choice theory, also known as voting theory, examines the methods by which
1 Aggregating Preferences
 ECON 301: General Equilibrium III (Welfare) 1 Intermediate Microeconomics II, ECON 301 General Equilibrium III: Welfare We are done with the vital concepts of general equilibrium Its power principally
ECON 301: General Equilibrium III (Welfare) 1 Intermediate Microeconomics II, ECON 301 General Equilibrium III: Welfare We are done with the vital concepts of general equilibrium Its power principally
Electrical Engineering and Computer Science Department
 Electrical Engineering and Computer Science Department Technical Report NWU-EECS-08-5 July, 008 Internet Politics: Resist, Die, or Exploit? Leiwen Deng and Aleksandar Kuzmanovic Abstract In this paper,
Electrical Engineering and Computer Science Department Technical Report NWU-EECS-08-5 July, 008 Internet Politics: Resist, Die, or Exploit? Leiwen Deng and Aleksandar Kuzmanovic Abstract In this paper,
Chapter 10. The Manipulability of Voting Systems. For All Practical Purposes: Effective Teaching. Chapter Briefing
 Chapter 10 The Manipulability of Voting Systems For All Practical Purposes: Effective Teaching As a teaching assistant, you most likely will administer and proctor many exams. Although it is tempting to
Chapter 10 The Manipulability of Voting Systems For All Practical Purposes: Effective Teaching As a teaching assistant, you most likely will administer and proctor many exams. Although it is tempting to
CS 4407 Algorithms Greedy Algorithms and Minimum Spanning Trees
 CS 4407 Algorithms Greedy Algorithms and Minimum Spanning Trees Prof. Gregory Provan Department of Computer Science University College Cork 1 Sample MST 6 5 4 9 14 10 2 3 8 15 Greedy Algorithms When are
CS 4407 Algorithms Greedy Algorithms and Minimum Spanning Trees Prof. Gregory Provan Department of Computer Science University College Cork 1 Sample MST 6 5 4 9 14 10 2 3 8 15 Greedy Algorithms When are
HASHGRAPH CONSENSUS: DETAILED EXAMPLES
 HASHGRAPH CONSENSUS: DETAILED EXAMPLES LEEMON BAIRD BAIRD@SWIRLDS.COM DECEMBER 11, 2016 SWIRLDS TECH REPORT SWIRLDS-TR-2016-02 ABSTRACT: The Swirlds hashgraph consensus algorithm is explained through a
HASHGRAPH CONSENSUS: DETAILED EXAMPLES LEEMON BAIRD BAIRD@SWIRLDS.COM DECEMBER 11, 2016 SWIRLDS TECH REPORT SWIRLDS-TR-2016-02 ABSTRACT: The Swirlds hashgraph consensus algorithm is explained through a
Support Vector Machines
 Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
Support Vector Machines Linearly Separable Data SVM: Simple Linear Separator hyperplane Which Simple Linear Separator? Classifier Margin Objective #1: Maximize Margin MARGIN MARGIN How s this look? MARGIN
VOTING DYNAMICS IN INNOVATION SYSTEMS
 VOTING DYNAMICS IN INNOVATION SYSTEMS Voting in social and collaborative systems is a key way to elicit crowd reaction and preference. It enables the diverse perspectives of the crowd to be expressed and
VOTING DYNAMICS IN INNOVATION SYSTEMS Voting in social and collaborative systems is a key way to elicit crowd reaction and preference. It enables the diverse perspectives of the crowd to be expressed and
MATH4999 Capstone Projects in Mathematics and Economics Topic 3 Voting methods and social choice theory
 MATH4999 Capstone Projects in Mathematics and Economics Topic 3 Voting methods and social choice theory 3.1 Social choice procedures Plurality voting Borda count Elimination procedures Sequential pairwise
MATH4999 Capstone Projects in Mathematics and Economics Topic 3 Voting methods and social choice theory 3.1 Social choice procedures Plurality voting Borda count Elimination procedures Sequential pairwise
Connecting Voting Theory and Graph Theory
 Connecting Voting Theory and Graph Theory Karl-Dieter Crisman Gordon College Willamette University Math Colloquium, October 13, 2016 Karl-Dieter Crisman (Gordon College) Graphs and Voting WU Colloquium
Connecting Voting Theory and Graph Theory Karl-Dieter Crisman Gordon College Willamette University Math Colloquium, October 13, 2016 Karl-Dieter Crisman (Gordon College) Graphs and Voting WU Colloquium
Randomized Pursuit-Evasion in Graphs
 Randomized Pursuit-Evasion in Graphs Micah Adler Harald Räcke Ý Naveen Sivadasan Þ Christian Sohler Ý Berthold Vöcking Þ Abstract We analyze a randomized pursuit-evasion game on graphs. This game is played
Randomized Pursuit-Evasion in Graphs Micah Adler Harald Räcke Ý Naveen Sivadasan Þ Christian Sohler Ý Berthold Vöcking Þ Abstract We analyze a randomized pursuit-evasion game on graphs. This game is played
A New Method of the Single Transferable Vote and its Axiomatic Justification
 A New Method of the Single Transferable Vote and its Axiomatic Justification Fuad Aleskerov ab Alexander Karpov a a National Research University Higher School of Economics 20 Myasnitskaya str., 101000
A New Method of the Single Transferable Vote and its Axiomatic Justification Fuad Aleskerov ab Alexander Karpov a a National Research University Higher School of Economics 20 Myasnitskaya str., 101000
Voting on combinatorial domains. LAMSADE, CNRS Université Paris-Dauphine. FET-11, session on Computational Social Choice
 Voting on combinatorial domains Jérôme Lang LAMSADE, CNRS Université Paris-Dauphine FET-11, session on Computational Social Choice A key question: structure of the setx of candidates? Example 1 choosing
Voting on combinatorial domains Jérôme Lang LAMSADE, CNRS Université Paris-Dauphine FET-11, session on Computational Social Choice A key question: structure of the setx of candidates? Example 1 choosing
NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York
 NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York DEPARTMENT: Mathematics COURSE: MAT 2440/ MA 440 TITLE: DESCRIPTION: TEXTS: Discrete Structures and Algorithms I This course introduces
NEW YORK CITY COLLEGE OF TECHNOLOGY The City University of New York DEPARTMENT: Mathematics COURSE: MAT 2440/ MA 440 TITLE: DESCRIPTION: TEXTS: Discrete Structures and Algorithms I This course introduces
Homework 7 Answers PS 30 November 2013
 Homework 7 Answers PS 30 November 2013 1. Say that there are three people and five candidates {a, b, c, d, e}. Say person 1 s order of preference (from best to worst) is c, b, e, d, a. Person 2 s order
Homework 7 Answers PS 30 November 2013 1. Say that there are three people and five candidates {a, b, c, d, e}. Say person 1 s order of preference (from best to worst) is c, b, e, d, a. Person 2 s order
A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset
 A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset Sisi Xiong*, Feiyi Wang + and Qing Cao* *University of Tennessee Knoxville, Knoxville, TN, USA + Oak Ridge National Laboratory,
A Bloom Filter Based Scalable Data Integrity Check Tool for Large-scale Dataset Sisi Xiong*, Feiyi Wang + and Qing Cao* *University of Tennessee Knoxville, Knoxville, TN, USA + Oak Ridge National Laboratory,
Social welfare functions
 Social welfare functions We have defined a social choice function as a procedure that determines for each possible profile (set of preference ballots) of the voters the winner or set of winners for the
Social welfare functions We have defined a social choice function as a procedure that determines for each possible profile (set of preference ballots) of the voters the winner or set of winners for the
Chapter 9: Social Choice: The Impossible Dream
 Chapter 9: Social Choice: The Impossible Dream The application of mathematics to the study of human beings their behavior, values, interactions, conflicts, and methods of making decisions is generally
Chapter 9: Social Choice: The Impossible Dream The application of mathematics to the study of human beings their behavior, values, interactions, conflicts, and methods of making decisions is generally
Minimum Spanning Tree Union-Find Data Structure. Feb 28, 2018 CSCI211 - Sprenkle. Comcast wants to lay cable in a neighborhood. Neighborhood Layout
 Objec&ves Minimum Spanning Tree Union-Find Data Structure Feb, 0 CSCI - Sprenkle Started teasing out some algorithms. Laying Cable Focus on commonality: what should our final solution look like? Comcast
Objec&ves Minimum Spanning Tree Union-Find Data Structure Feb, 0 CSCI - Sprenkle Started teasing out some algorithms. Laying Cable Focus on commonality: what should our final solution look like? Comcast
Introduction to Computational Social Choice. Yann Chevaleyre. LAMSADE, Université Paris-Dauphine
 Introduction to Computational Social Choice Yann Chevaleyre Jérôme Lang LAMSADE, Université Paris-Dauphine Computational social choice: two research streams From social choice theory to computer science
Introduction to Computational Social Choice Yann Chevaleyre Jérôme Lang LAMSADE, Université Paris-Dauphine Computational social choice: two research streams From social choice theory to computer science
Approval Voting Theory with Multiple Levels of Approval
 Claremont Colleges Scholarship @ Claremont HMC Senior Theses HMC Student Scholarship 2012 Approval Voting Theory with Multiple Levels of Approval Craig Burkhart Harvey Mudd College Recommended Citation
Claremont Colleges Scholarship @ Claremont HMC Senior Theses HMC Student Scholarship 2012 Approval Voting Theory with Multiple Levels of Approval Craig Burkhart Harvey Mudd College Recommended Citation
arxiv: v1 [cs.gt] 11 Jul 2018
![arxiv: v1 [cs.gt] 11 Jul 2018 arxiv: v1 [cs.gt] 11 Jul 2018](/thumbs/89/99238134.jpg) Sequential Voting with Confirmation Network Yakov Babichenko yakovbab@tx.technion.ac.il Oren Dean orendean@campus.technion.ac.il Moshe Tennenholtz moshet@ie.technion.ac.il arxiv:1807.03978v1 [cs.gt] 11
Sequential Voting with Confirmation Network Yakov Babichenko yakovbab@tx.technion.ac.il Oren Dean orendean@campus.technion.ac.il Moshe Tennenholtz moshet@ie.technion.ac.il arxiv:1807.03978v1 [cs.gt] 11
AGENDAS AND SINCERITY: A SECOND RESPONSE TO SCHWARTZ
 AGENDAS AND SINCERITY: A SECOND RESPONSE TO SCHWARTZ Nicholas R. Miller Department of Political Science University of Maryland Baltimore County Baltimore MD 21250 nmiller@umbc.edu July 2010 Abstract An
AGENDAS AND SINCERITY: A SECOND RESPONSE TO SCHWARTZ Nicholas R. Miller Department of Political Science University of Maryland Baltimore County Baltimore MD 21250 nmiller@umbc.edu July 2010 Abstract An
Bribery in voting with CP-nets
 Ann Math Artif Intell (2013) 68:135 160 DOI 10.1007/s10472-013-9330-5 Bribery in voting with CP-nets Nicholas Mattei Maria Silvia Pini Francesca Rossi K. Brent Venable Published online: 7 February 2013
Ann Math Artif Intell (2013) 68:135 160 DOI 10.1007/s10472-013-9330-5 Bribery in voting with CP-nets Nicholas Mattei Maria Silvia Pini Francesca Rossi K. Brent Venable Published online: 7 February 2013
Estimating the Margin of Victory for an IRV Election Part 1 by David Cary November 6, 2010
 Summary Estimating the Margin of Victory for an IRV Election Part 1 by David Cary November 6, 2010 New procedures are being developed for post-election audits involving manual recounts of random samples
Summary Estimating the Margin of Victory for an IRV Election Part 1 by David Cary November 6, 2010 New procedures are being developed for post-election audits involving manual recounts of random samples
Agenda trees and sincere voting: a response to Schwartz
 Public Choice (2010) 145: 213 221 DOI 10.1007/s11127-009-9562-4 Agenda trees and sincere voting: a response to Schwartz Nicholas R. Miller Received: 27 July 2009 / Accepted: 30 October 2009 / Published
Public Choice (2010) 145: 213 221 DOI 10.1007/s11127-009-9562-4 Agenda trees and sincere voting: a response to Schwartz Nicholas R. Miller Received: 27 July 2009 / Accepted: 30 October 2009 / Published
Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times
 Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Objectives Proving correctness of Stable Matching algorithm Analyzing algorithms Asymptotic running times Wiki notes: Read after class; I am giving loose guidelines the point is to review and synthesize
Quality of Service in Optical Telecommunication Networks
 Quality of Service in Optical Telecommunication Networks Periodic Summary & Future Research Ideas Zhizhen Zhong 2015.08.28 @Networks Lab Group Meeting 1 Outline Ø Background Ø Preemptive Service Degradation
Quality of Service in Optical Telecommunication Networks Periodic Summary & Future Research Ideas Zhizhen Zhong 2015.08.28 @Networks Lab Group Meeting 1 Outline Ø Background Ø Preemptive Service Degradation
Tengyu Ma Facebook AI Research. Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford)
 Tengyu Ma Facebook AI Research Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford) Ø Over-parameterization: # parameters # examples Ø a set of parameters that can Ø fit to training
Tengyu Ma Facebook AI Research Based on joint work with Yuanzhi Li (Princeton) and Hongyang Zhang (Stanford) Ø Over-parameterization: # parameters # examples Ø a set of parameters that can Ø fit to training
arxiv: v2 [math.ho] 12 Oct 2018
![arxiv: v2 [math.ho] 12 Oct 2018 arxiv: v2 [math.ho] 12 Oct 2018](/thumbs/92/109875862.jpg) PHRAGMÉN S AND THIELE S ELECTION METHODS arxiv:1611.08826v2 [math.ho] 12 Oct 2018 SVANTE JANSON Abstract. The election methods introduced in 1894 1895 by Phragmén and Thiele, and their somewhat later versions
PHRAGMÉN S AND THIELE S ELECTION METHODS arxiv:1611.08826v2 [math.ho] 12 Oct 2018 SVANTE JANSON Abstract. The election methods introduced in 1894 1895 by Phragmén and Thiele, and their somewhat later versions
Manipulating Two Stage Voting Rules
 Manipulating Two Stage Voting Rules Nina Narodytska NICTA and UNSW Sydney, Australia nina.narodytska@nicta.com.au Toby Walsh NICTA and UNSW Sydney, Australia toby.walsh@nicta.com.au ABSTRACT We study the
Manipulating Two Stage Voting Rules Nina Narodytska NICTA and UNSW Sydney, Australia nina.narodytska@nicta.com.au Toby Walsh NICTA and UNSW Sydney, Australia toby.walsh@nicta.com.au ABSTRACT We study the
Supreme Court of Florida
 Supreme Court of Florida No. AOSC08-29 IN RE: JUROR SELECTION PLAN: HILLSBOROUGH COUNTY ADMINISTRATIVE ORDER Section 40.225, Florida Statutes, provides for the selection of jurors to serve within the county
Supreme Court of Florida No. AOSC08-29 IN RE: JUROR SELECTION PLAN: HILLSBOROUGH COUNTY ADMINISTRATIVE ORDER Section 40.225, Florida Statutes, provides for the selection of jurors to serve within the county
Agendas and sincerity: a second response to Schwartz
 Public Choice (2010) 145: 575 579 DOI 10.1007/s11127-010-9704-8 Agendas and sincerity: a second response to Schwartz Nicholas R. Miller Received: 9 July 2010 / Accepted: 4 August 2010 / Published online:
Public Choice (2010) 145: 575 579 DOI 10.1007/s11127-010-9704-8 Agendas and sincerity: a second response to Schwartz Nicholas R. Miller Received: 9 July 2010 / Accepted: 4 August 2010 / Published online:
Hat problem on a graph
 Hat problem on a graph Submitted by Marcin Piotr Krzywkowski to the University of Exeter as a thesis for the degree of Doctor of Philosophy by Publication in Mathematics In April 2012 This thesis is available
Hat problem on a graph Submitted by Marcin Piotr Krzywkowski to the University of Exeter as a thesis for the degree of Doctor of Philosophy by Publication in Mathematics In April 2012 This thesis is available
The Australian Society for Operations Research
 The Australian Society for Operations Research www.asor.org.au ASOR Bulletin Volume 34, Issue, (06) Pages -4 A minimum spanning tree with node index Elias Munapo School of Economics and Decision Sciences,
The Australian Society for Operations Research www.asor.org.au ASOR Bulletin Volume 34, Issue, (06) Pages -4 A minimum spanning tree with node index Elias Munapo School of Economics and Decision Sciences,
Year 1 Mental mathematics and fluency in rapid recall of number facts are one of the main aims of the new Mathematics Curriculum.
 Year 1 by the end of Year 1. Ø Recite numbers to 100 forwards and backwards from any number Ø Read and write numbers to 100 in numerals Ø Read and write numbers to 20 in words Ø Order numbers to 100 Ø
Year 1 by the end of Year 1. Ø Recite numbers to 100 forwards and backwards from any number Ø Read and write numbers to 100 in numerals Ø Read and write numbers to 20 in words Ø Order numbers to 100 Ø
c M. J. Wooldridge, used by permission/updated by Simon Parsons, Spring
 Today LECTURE 8: MAKING GROUP DECISIONS CIS 716.5, Spring 2010 We continue thinking in the same framework as last lecture: multiagent encounters game-like interactions participants act strategically We
Today LECTURE 8: MAKING GROUP DECISIONS CIS 716.5, Spring 2010 We continue thinking in the same framework as last lecture: multiagent encounters game-like interactions participants act strategically We
Introduction to Game Theory. Lirong Xia
 Introduction to Game Theory Lirong Xia Fall, 2016 Homework 1 2 Announcements ØWe will use LMS for submission and grading ØPlease just submit one copy ØPlease acknowledge your team mates 3 Ø Show the math
Introduction to Game Theory Lirong Xia Fall, 2016 Homework 1 2 Announcements ØWe will use LMS for submission and grading ØPlease just submit one copy ØPlease acknowledge your team mates 3 Ø Show the math
SMART MOTION C A T A L O G 2009:1
 SMART MOTION C A T A L O G 2009:1 Which arm do you need? To ensure that the balancing arm you order meets your expectations it is important to consider the following aspects. 1. Which type? PARALLEL ARM
SMART MOTION C A T A L O G 2009:1 Which arm do you need? To ensure that the balancing arm you order meets your expectations it is important to consider the following aspects. 1. Which type? PARALLEL ARM
Analyzing proofs Introduction to problem solving. Wiki: Everyone log in okay? Decide on either using a blog or wiki-style journal?
 Objectives Analyzing proofs Introduction to problem solving Ø Our process, through an example Wiki: Everyone log in okay? Decide on either using a blog or wiki-style journal? 1 Review What are our goals
Objectives Analyzing proofs Introduction to problem solving Ø Our process, through an example Wiki: Everyone log in okay? Decide on either using a blog or wiki-style journal? 1 Review What are our goals
How hard is it to control sequential elections via the agenda?
 How hard is it to control sequential elections via the agenda? Vincent Conitzer Department of Computer Science Duke University Durham, NC 27708, USA conitzer@cs.duke.edu Jérôme Lang LAMSADE Université
How hard is it to control sequential elections via the agenda? Vincent Conitzer Department of Computer Science Duke University Durham, NC 27708, USA conitzer@cs.duke.edu Jérôme Lang LAMSADE Université
Data 100. Lecture 9: Scraping Web Technologies. Slides by: Joseph E. Gonzalez, Deb Nolan
 Data 100 Lecture 9: Scraping Web Technologies Slides by: Joseph E. Gonzalez, Deb Nolan deborah_nolan@berkeley.edu hellerstein@berkeley.edu? Last Week Visualization Ø Tools and Technologies Ø Maplotlib
Data 100 Lecture 9: Scraping Web Technologies Slides by: Joseph E. Gonzalez, Deb Nolan deborah_nolan@berkeley.edu hellerstein@berkeley.edu? Last Week Visualization Ø Tools and Technologies Ø Maplotlib
Computational Social Choice: Spring 2017
 Computational Social Choice: Spring 2017 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today So far we saw three voting rules: plurality, plurality
Computational Social Choice: Spring 2017 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today So far we saw three voting rules: plurality, plurality
The Mathematics of Voting. The Mathematics of Voting
 1.3 The Borda Count Method 1 In the Borda Count Method each place on a ballot is assigned points. In an election with N candidates we give 1 point for last place, 2 points for second from last place, and
1.3 The Borda Count Method 1 In the Borda Count Method each place on a ballot is assigned points. In an election with N candidates we give 1 point for last place, 2 points for second from last place, and
Chapter 9: Social Choice: The Impossible Dream Lesson Plan
 Lesson Plan For All Practical Purposes An Introduction to Social Choice Majority Rule and Condorcet s Method Mathematical Literacy in Today s World, 9th ed. Other Voting Systems for Three or More Candidates
Lesson Plan For All Practical Purposes An Introduction to Social Choice Majority Rule and Condorcet s Method Mathematical Literacy in Today s World, 9th ed. Other Voting Systems for Three or More Candidates
Stackelberg Voting Games
 7 Stackelberg Voting Games Using computational complexity to protect elections from manipulation, bribery, control, and other types of strategic behavior is one of the major topics of Computational Social
7 Stackelberg Voting Games Using computational complexity to protect elections from manipulation, bribery, control, and other types of strategic behavior is one of the major topics of Computational Social
Local differential privacy
 Local differential privacy Adam Smith Penn State Bar-Ilan Winter School February 14, 2017 Outline Model Ø Implementations Question: what computations can we carry out in this model? Example: randomized
Local differential privacy Adam Smith Penn State Bar-Ilan Winter School February 14, 2017 Outline Model Ø Implementations Question: what computations can we carry out in this model? Example: randomized
Overview. Ø Neural Networks are considered black-box models Ø They are complex and do not provide much insight into variable relationships
 Neural Networks Overview Ø s are considered black-box models Ø They are complex and do not provide much insight into variable relationships Ø They have the potential to model very complicated patterns
Neural Networks Overview Ø s are considered black-box models Ø They are complex and do not provide much insight into variable relationships Ø They have the potential to model very complicated patterns
Arrow s Impossibility Theorem
 Arrow s Impossibility Theorem Some announcements Final reflections due on Monday. You now have all of the methods and so you can begin analyzing the results of your election. Today s Goals We will discuss
Arrow s Impossibility Theorem Some announcements Final reflections due on Monday. You now have all of the methods and so you can begin analyzing the results of your election. Today s Goals We will discuss
Political Districting for Elections to the German Bundestag: An Optimization-Based Multi-Stage Heuristic Respecting Administrative Boundaries
 Political Districting for Elections to the German Bundestag: An Optimization-Based Multi-Stage Heuristic Respecting Administrative Boundaries Sebastian Goderbauer 1 Electoral Districts in Elections to
Political Districting for Elections to the German Bundestag: An Optimization-Based Multi-Stage Heuristic Respecting Administrative Boundaries Sebastian Goderbauer 1 Electoral Districts in Elections to
Platform independent proc interface
 Platform independent proc interface Author: WangDi & Komal 05/07/2008 1 Introduction This document describes how to implement a platform independent proc interface for Lustre. The basic idea is that the
Platform independent proc interface Author: WangDi & Komal 05/07/2008 1 Introduction This document describes how to implement a platform independent proc interface for Lustre. The basic idea is that the
Random Forests. Gradient Boosting. and. Bagging and Boosting
 Random Forests and Gradient Boosting Bagging and Boosting The Bootstrap Sample and Bagging Simple ideas to improve any model via ensemble Bootstrap Samples Ø Random samples of your data with replacement
Random Forests and Gradient Boosting Bagging and Boosting The Bootstrap Sample and Bagging Simple ideas to improve any model via ensemble Bootstrap Samples Ø Random samples of your data with replacement
Designing a Social Network Prep for Lab 10. March 26, 2018 Sprenkle - CSCI Why classes and objects? How do we create new data types?
 Objec(ves Designing a Social Network Prep for Lab 10 March 26, 2018 Sprenkle - CSCI111 1 Review What trends did we see in the names of students at W&L? Ø What was as you expected? Ø What surprised you?
Objec(ves Designing a Social Network Prep for Lab 10 March 26, 2018 Sprenkle - CSCI111 1 Review What trends did we see in the names of students at W&L? Ø What was as you expected? Ø What surprised you?
Clause Logic Service User Interface User Manual
 Clause Logic Service User Interface User Manual Version 2.0 1 February 2018 Prepared by: Northrop Grumman 12900 Federal Systems Park Drive Fairfax, VA 22033 Under Contract Number: SP4701-15-D-0001, TO
Clause Logic Service User Interface User Manual Version 2.0 1 February 2018 Prepared by: Northrop Grumman 12900 Federal Systems Park Drive Fairfax, VA 22033 Under Contract Number: SP4701-15-D-0001, TO
Voting Criteria April
 Voting Criteria 21-301 2018 30 April 1 Evaluating voting methods In the last session, we learned about different voting methods. In this session, we will focus on the criteria we use to evaluate whether
Voting Criteria 21-301 2018 30 April 1 Evaluating voting methods In the last session, we learned about different voting methods. In this session, we will focus on the criteria we use to evaluate whether
Distributive Justice Rawls
 Distributive Justice Rawls 1. Justice as Fairness: Imagine that you have a cake to divide among several people, including yourself. How do you divide it among them in a just manner? If any of the slices
Distributive Justice Rawls 1. Justice as Fairness: Imagine that you have a cake to divide among several people, including yourself. How do you divide it among them in a just manner? If any of the slices
Randomized Pursuit-Evasion in Graphs
 Randomized Pursuit-Evasion in Graphs Micah Adler, Harald Räcke ¾, Naveen Sivadasan, Christian Sohler ¾, and Berthold Vöcking ¾ Department of Computer Science University of Massachusetts, Amherst, micah@cs.umass.edu
Randomized Pursuit-Evasion in Graphs Micah Adler, Harald Räcke ¾, Naveen Sivadasan, Christian Sohler ¾, and Berthold Vöcking ¾ Department of Computer Science University of Massachusetts, Amherst, micah@cs.umass.edu
Social Rankings in Human-Computer Committees
 Proceedings of the Twenty-Seventh AAAI Conference on Artificial Intelligence Social Rankings in Human-Computer Committees Moshe Bitan Bar-Ilan University, Israel Ya akov Gal Ben-Gurion University, Israel
Proceedings of the Twenty-Seventh AAAI Conference on Artificial Intelligence Social Rankings in Human-Computer Committees Moshe Bitan Bar-Ilan University, Israel Ya akov Gal Ben-Gurion University, Israel
Recall: Properties of ranking rules. Recall: Properties of ranking rules. Kenneth Arrow. Recall: Properties of ranking rules. Strategically vulnerable
 Outline for today Stat155 Game Theory Lecture 26: More Voting. Peter Bartlett December 1, 2016 1 / 31 2 / 31 Recall: Voting and Ranking Recall: Properties of ranking rules Assumptions There is a set Γ
Outline for today Stat155 Game Theory Lecture 26: More Voting. Peter Bartlett December 1, 2016 1 / 31 2 / 31 Recall: Voting and Ranking Recall: Properties of ranking rules Assumptions There is a set Γ
Manipulative Voting Dynamics
 Manipulative Voting Dynamics Thesis submitted in accordance with the requirements of the University of Liverpool for the degree of Doctor in Philosophy by Neelam Gohar Supervisor: Professor Paul W. Goldberg
Manipulative Voting Dynamics Thesis submitted in accordance with the requirements of the University of Liverpool for the degree of Doctor in Philosophy by Neelam Gohar Supervisor: Professor Paul W. Goldberg
LOUISIANA MECHANIC S LIEN LAW
 LOUISIANA MECHANIC S LIEN LAW 2018-2019 Go to: Louisiana Mechanic s Lien Forms More Info: www.nationallienlaw.com Section Contents Pre-lien Notice(s) Name of Notice Who Must Use This Notice When How to
LOUISIANA MECHANIC S LIEN LAW 2018-2019 Go to: Louisiana Mechanic s Lien Forms More Info: www.nationallienlaw.com Section Contents Pre-lien Notice(s) Name of Notice Who Must Use This Notice When How to
1.6 Arrow s Impossibility Theorem
 1.6 Arrow s Impossibility Theorem Some announcements Homework #2: Text (pages 33-35) 51, 56-60, 61, 65, 71-75 (this is posted on Sakai) For Monday, read Chapter 2 (pages 36-57) Today s Goals We will discuss
1.6 Arrow s Impossibility Theorem Some announcements Homework #2: Text (pages 33-35) 51, 56-60, 61, 65, 71-75 (this is posted on Sakai) For Monday, read Chapter 2 (pages 36-57) Today s Goals We will discuss
Hoboken Public Schools. Algebra II Honors Curriculum
 Hoboken Public Schools Algebra II Honors Curriculum Algebra Two Honors HOBOKEN PUBLIC SCHOOLS Course Description Algebra II Honors continues to build students understanding of the concepts that provide
Hoboken Public Schools Algebra II Honors Curriculum Algebra Two Honors HOBOKEN PUBLIC SCHOOLS Course Description Algebra II Honors continues to build students understanding of the concepts that provide
Aggregating Dependency Graphs into Voting Agendas in Multi-Issue Elections
 Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Aggregating Dependency Graphs into Voting Agendas in Multi-Issue Elections Stéphane Airiau, Ulle Endriss, Umberto
Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Aggregating Dependency Graphs into Voting Agendas in Multi-Issue Elections Stéphane Airiau, Ulle Endriss, Umberto
Math of Election APPORTIONMENT
 Math of Election APPORTIONMENT Alfonso Gracia-Saz, Ari Nieh, Mira Bernstein Canada/USA Mathcamp 2017 Apportionment refers to any of the following, equivalent mathematical problems: We want to elect a Congress
Math of Election APPORTIONMENT Alfonso Gracia-Saz, Ari Nieh, Mira Bernstein Canada/USA Mathcamp 2017 Apportionment refers to any of the following, equivalent mathematical problems: We want to elect a Congress
Polydisciplinary Faculty of Larache Abdelmalek Essaadi University, MOROCCO 3 Department of Mathematics and Informatics
 International Journal of Pure and Applied Mathematics Volume 115 No. 4 2017, 801-812 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu doi: 10.12732/ijpam.v115i4.13
International Journal of Pure and Applied Mathematics Volume 115 No. 4 2017, 801-812 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu doi: 10.12732/ijpam.v115i4.13
CS 5523: Operating Systems
 CS 5523: Operating Systems Instructor: Dr. Tongping Liu Final Reviews (Comprehensive) Final Exam: May 5, 2015, Tuesday 6:00pm 8:30pm CS5523: Operating Systems @ UTSA 1 Lecture06: Distributed Systems Distributed
CS 5523: Operating Systems Instructor: Dr. Tongping Liu Final Reviews (Comprehensive) Final Exam: May 5, 2015, Tuesday 6:00pm 8:30pm CS5523: Operating Systems @ UTSA 1 Lecture06: Distributed Systems Distributed
Louis M. Edwards Mathematics Super Bowl Valencia Community College -- April 30, 2004
 Practice Round 1. The overall average in an algebra class is described in the syllabus as a weighted average of homework, tests, and the final exam. The homework counts 10%, the three tests each count
Practice Round 1. The overall average in an algebra class is described in the syllabus as a weighted average of homework, tests, and the final exam. The homework counts 10%, the three tests each count
