Analyzing Terrorist Networks - Theories & Techniques
|
|
|
- Marcia Simpson
- 6 years ago
- Views:
Transcription
1 NYU Department of Politics April 10, 2012
2 What We Will Discuss Why I am talking to you? Where I used to work What I used to do How I used to do it Theories of terrorist organizations Sageman and Hoffman schools Empirical observations Who s right? Basic network analysis techniques used in CT Key actor analysis Detecting community structure Block modeling Exploring with real networks Illicit drug network in Hartford, CT Covert terrorist network Conclusions & Departing Thoughts New paradigms in network organization Using network analysis to address them
3 My experience in the Intelligence Community DISCLAIMER: All views and opinions expressed today are my own, and not those of U.S. Department of Defense or Office of the Director of National Intelligence Currently, a fourth year PhD student in Politics, research interests include... Terrorism, low-intensity conflict, and cyber warfare Agent-based modeling, machine learning, and network analysis Prior to entering graduate school... Worked in DC in the defense and intelligence communities for four years Official title was All-source analyst, specific role was to apply statistical and computational methods to problems of social dynamics and organization of interest to the DoD/IC. NO: If I tell what I really did I will not have to kill you...they never have the analysts do the killing
4 Organization of the IC & Where I Worked Defense Intelligence Agency Getting intelligence to the war fighter National Security Agency SIGINT and cryptology
5 The Sageman and Hoffman Schools on Terrorist Organizations Sageman School Marc Sageman - former CIA case officer for Islamabad Currently Scholar in Residence at the NYPD Terrorist groups are independent, or loosely connected cells Organization driven by a group process; result of circumstance, motivation and opportunity The types of social ties are extremely important: kinship, friendship and religious From Leaderless Jihad... The links are very interesting because it turned out that 68% joined the Jihad out of friendship, they either grew up with somebody who was already a terrorist, or there was a bunch of guys who collectively decided to join. Hoffman School Bruce Hoffman - History professor at Georgetown University Respected academic in terrorism studies, published widely read Inside Terrorism Terrorist groups are hierarchical structures Global terrorist organization are well-formed and lethal Critical information and resources flow down from the leadership to low-level operatives From Foreign Affairs Al Qaeda is much like a shark, which must keep moving forward, no matter how slowly or incrementally, or die. Al Qaeda must constantly adapt and adjust to its enemies efforts to stymie its plans while simultaneously identifying new targets.
6 Evidence in support of Sageman The Hamburg Cell Late 1998, future 9/11 hijackers Mohammed Atta, Marwan al-shehhi, and Ramzi Binalshibh moved into a three-bedroom apartment Originally intending to fight jihad in Chechnya, a chance meeting on a train in Germany caused the group to travel to Afghanistan instead. Several more contemporary examples 2004 Madrid Train Bombing al-qaeda inspired cell July 7, 2005 London bombings 4 British, 3 Pakistani and 1 Jamaican motivated by British involvement in Iraq War Alexandria 5 N. VA students travel to Pakistan to join Taliban Excerpt from The Pact This is a story about the power of friendship. Of joining forces and beating the odds...
7 Evidence in Support of Hoffman 2002 Bali Bombings Coordinated attack carried out by Jemaah Islamiyah (JI), Southeast Asian militant Islamic group Deadliest attack in Indonesia s history, killed 202 people Organized as a hierarchy, though many leaders have since been killed or captured International terrorist organizations remain lethal 2008 Mumbai attacks 10 coordinated attacks perpetrated by Lashkar-e-Taiba militants from Pakistan Beslan school hostage crisis Chechan militants seize school with 1,100 people (including 777 children) for three days. Ultimately, 334 hostages were killed, including 186 children. Richard Reid (shoe bomber) admitted member of al-qaeda 2007 NIE The Terrorist Threat to the US Homeland Al-Qaida is and will remain the most serious terrorist threat to the Homeland, as its central leadership continues to plan high-impact plots, while pushing others in extremist Sunni communities to mimic its efforts and to supplement its capabilities.
8 Sorting out the debate Who s right? Spoiler: Both men are correct, and wrong Karen J. Greenberg, Executive Director of NYU Center on Law and Security Sometimes it seems like this entire field is stepping into a boys-with-toys conversation. Here are two guys, both of them respected, saying that there is only one truth and only one occupant of the sandbox. Thats ridiculous. Both of them are valuable. Since 9/11, the persistent, coordinated and international effort to kill or capture terrorist leaders has decimated the structure of transnational terrorist organization For those left, movement, communication and planning has become incredibly strained Enter the age of the al-qaeda Affiliates Model has moved away from strictly hierarchical or cellular to a franchise Leadership provide inspiration, rather than resources and ideas Umar Farouk Abdulmutallab and the al-qaeda in the Arabian Peninsula
9 Why study networks for CT? 9/11 Commission Report - Chapter 12 Our enemy is twofold: al Qaeda, a stateless network of terrorists that struck us on 9/11; and a radical ideological movement in the Islamic world, inspired in part by al Qaeda, which has spawned terrorist groups and violence across the globe. The first enemy is weakened, but continues to pose a grave threat. The second enemy is gathering, and will menace Americans and American interests long after Usama Bin Ladin and his cohorts are killed or captured. Thus our strategy must match our means to two ends: dismantling the al Qaeda network and prevailing in the longer term over the ideology that gives rise to Islamist terrorism. After 9/11, the IC becomes focused on understanding networked organizations, with a specific focus on dismantling and disrupting Primary focus is one three aspects of network analysis 1. Identifying leadership and key actors 2. Revealing underlying structure and intra-network community structure 3. Evolution and decay of social networks We will review 1-2; however, 3 is where most cutting edge network research is focused
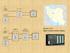
10 Comparing two network metrics to find key actors Often social network analysis is used to identify key actors within a social group. To identify these actors, various centrality metrics can be computed based on a network s structure Degree (number of connections) Betweenness (number of shortest paths an actor is on) Closeness (relative distance to all other actors) Eigenvector centrality (leading eigenvector of sociomatrix) One method for using these metrics to identify key actors is to plot actors scores for Eigenvector centrality versus Betweenness. Theoretically, these metrics should be approximately linear; therefore, any non-linear outliers will be of note. An actor with very high betweenness but low EC may be a critical gatekeeper to a central actor Likewise, an actor with low betweenness but high EC may have unique access to central actors
11 Highlighting Key Actors Using data collected on a network of drug users in Hartford, CT we will attempt to identify the identity and location of the key actors First, visualize the data 1. Clear bifurcation within the network 2. Each region of the network appears to cluster around central communities 3. Sparse peripheral structure with long pendant chains Given these structural features we will want to identify actors both inside the network s core, but also those with unique structural positions
12 Finding Key Actors with R Perform a linear regression of Eig Bet Capture residuals from regression Use this data to resize and color the actors in the plot Identify key actors: Pulse takers Gate-keepers Actor 44 is a significant outlier, and likely part of the central leadership, while actors 50, 28 and 53 are pulse takers and 67, 102, and 79 are gate-keepers....now add this visualizations together Eigenvector Centrality Key Actor Analysis for Hartford Drug Users Betweenness Centrality 67 res abs(res)
13 Key Actor Plot Plot with key actor data Good Very easily identify core leadership Mid-level actors, pulse-takers, layer Highlight some bridges, gate-keepers Bad Several key actors not highlighted Over-emphasis on one community due to data asymmetry
14 Identifying Network Sub-Structure The Hoffman School posits that terrorist networks will contain layers of connectivity and leadership. To identify these layers, we will examine an actual covert network Covert networks often exhibit a core-periphery structure We may want to identify clusters of actors based on various structural features
15 Methods for Community Detection Identifying community structure within a network is an entire sub-discipline of network science. Google Scholar search for [ community detection networks] returns 3,380 articles since 2001 There is an incredible diversity of methods Statistical Spectral Node and edge context and/or attributes We will be using a very basic method from the statistical category: hierarchical clustering of geodesic distance Clusters nodes together based on their distance (closer nodes clustered together) Returns several possible partitions Method is both art and science
16 Hierarchical Clustering of Geodesic Distance First, we will generate a matrix of the distance between all node pairs Clustering this data hierarchically, we can produce a dendrogram of all the community cuts within our covert network Each break in the tree represents a cut in the community structure Further down the tree, the more granular the communities To find a good set of community partitions we can step through them visually
17 Introduction Theories of terrorist organizations Network Analysis and CT Stepping through the partitions We will now visualize each community cut. Partition: Conclusions
18 Block Modeling Covert Network To reveal the underlying structure of these communities, we will collapse these communities into single nodes using a technique know as block modeling Suppose we wanted to view partition 8 as a block model In the block model, each colored group will become a single node We can also take advantage of additional data generated by the block model Each block represents some number of nodes with ties to each other, as well as actors in other blocks We can use that data to uncover both the underlying structure, as well as the tie dynamics within and among blocks in the model This is best revealed by combining this data into a visualization
19
20 Block Model of Partition 8 With the added data we can alter the visualization Blocks sized by internal density Edges sized by tie strength We can now see some distinct underlying structural dynamics Ignore block 8 Central leadership very tightly connected Middle layer sparsely, but strongly connected
21 Developing New Theories of Terrorist Organizations What is the influence of information technology on terrorism and terrorist organizations? Cyber-terrorism blurs the lines among transnational terrorism, state-sponsored attacks, rogue actors and homegrown threats Is it possible to distinguish among these threat? Is attribution possibly in cyber? The barriers to influence approach zero through the Internet Recruitment still primarily through in-person connections, but significant push to online How does the franchise model change theories of organization? With the vanishing operational importance of terrorist leadership, how can resources be maximized for CT? Is there more value in disrupting communication networks (e.g., inspiration/influence) than operation (e.g., franchise cells)? Can network analysis mitigate these new problems?
22 subsection new theories(end)
23 Thank you Thank you!
WCAML Forum. The Challenges of Terrorist Financing in 2014 and Beyond. May 7, Dennis M. Lormel President & CEO DML Associates, LLC
 The Challenges of Terrorist Financing in 2014 and Beyond May 7, 2014 Dennis M. Lormel President & CEO DML Associates, LLC Al-Qaeda s Most Dangerous Member: Nasir al-wuhayshi 2 Terrorist Threats 2014 Introduction
The Challenges of Terrorist Financing in 2014 and Beyond May 7, 2014 Dennis M. Lormel President & CEO DML Associates, LLC Al-Qaeda s Most Dangerous Member: Nasir al-wuhayshi 2 Terrorist Threats 2014 Introduction
A Behavioral Perspective on Money Laundering
 A Behavioral Perspective on Money Laundering Hendi Yogi Prabowo, SE, MForAccy, PhD Seminar Antikorupsi & Call for Proposals Jurnal Integritas Universitas Sriwijaya Palembang 3 Oktober 2017 Short CV Name:
A Behavioral Perspective on Money Laundering Hendi Yogi Prabowo, SE, MForAccy, PhD Seminar Antikorupsi & Call for Proposals Jurnal Integritas Universitas Sriwijaya Palembang 3 Oktober 2017 Short CV Name:
Combating Terrorism Center at West Point. Success, Lethality, and Cell Structure Across the Dimensions of Al Qaeda
 Combating Terrorism Center at West Point Occasional Paper Series Success, Lethality, and Cell Structure Across the Dimensions of Al Qaeda May 2, 2011 Scott Helfstein, Ph.D. Dominick Wright, Ph.D. The views
Combating Terrorism Center at West Point Occasional Paper Series Success, Lethality, and Cell Structure Across the Dimensions of Al Qaeda May 2, 2011 Scott Helfstein, Ph.D. Dominick Wright, Ph.D. The views
Following the Money to Combat Terrorism, Crime and Corruption
 Following the Money to Combat Terrorism, Crime and Corruption ACAMS Houston Chapter April 19, 2017 Celina B. Realuyo Professor of Practice William J. Perry Center for Hemispheric Defense Studies, National
Following the Money to Combat Terrorism, Crime and Corruption ACAMS Houston Chapter April 19, 2017 Celina B. Realuyo Professor of Practice William J. Perry Center for Hemispheric Defense Studies, National
NBER WORKING PAPER SERIES DESIGNING INSTITUTIONS TO DEAL WITH TERRORISM IN THE UNITED STATES. Martin S. Feldstein
 NBER WORKING PAPER SERIES DESIGNING INSTITUTIONS TO DEAL WITH TERRORISM IN THE UNITED STATES Martin S. Feldstein Working Paper 13729 http://www.nber.org/papers/w13729 NATIONAL BUREAU OF ECONOMIC RESEARCH
NBER WORKING PAPER SERIES DESIGNING INSTITUTIONS TO DEAL WITH TERRORISM IN THE UNITED STATES Martin S. Feldstein Working Paper 13729 http://www.nber.org/papers/w13729 NATIONAL BUREAU OF ECONOMIC RESEARCH
August 2013 Security Threat to Americans Abroad
 Number of Attacks BACKGROUND REPORT August 2013 Security Threat to Americans Abroad On Aug. 2, 2013 the U.S. State Department issued an alert 1 to Americans traveling abroad, particularly in the Middle
Number of Attacks BACKGROUND REPORT August 2013 Security Threat to Americans Abroad On Aug. 2, 2013 the U.S. State Department issued an alert 1 to Americans traveling abroad, particularly in the Middle
Follow this and additional works at: Part of the International Law Commons
 Indiana Journal of Global Legal Studies Volume 12 Issue 2 Article 1 Summer 2005 Fighting Terrorism Lee Hamilton Indiana University Follow this and additional works at: http://www.repository.law.indiana.edu/ijgls
Indiana Journal of Global Legal Studies Volume 12 Issue 2 Article 1 Summer 2005 Fighting Terrorism Lee Hamilton Indiana University Follow this and additional works at: http://www.repository.law.indiana.edu/ijgls
Radicalization/De-radicalization:
 Center on Global Counterterrorism Cooperation Project on U.S. Global Engagement Radicalization/De-radicalization: Lessons for the Next U.S. President 4 December 2008 SUMMARY In the third installment in
Center on Global Counterterrorism Cooperation Project on U.S. Global Engagement Radicalization/De-radicalization: Lessons for the Next U.S. President 4 December 2008 SUMMARY In the third installment in
Cover Story. - by Shraddha Bhandari. 24 JANUARY-FEBRUARY 2016 FSAI Journal
 - by Shraddha Bhandari 24 JANUARY-FEBRUARY 2016 FSAI Journal Following the spate of terror attacks in Paris, Beirut, and downing of the Russian Metrojet liner in November 2015, concerns have been raised
- by Shraddha Bhandari 24 JANUARY-FEBRUARY 2016 FSAI Journal Following the spate of terror attacks in Paris, Beirut, and downing of the Russian Metrojet liner in November 2015, concerns have been raised
Modern Terrorism and Counter-Terrorism Strategies
 Modern Terrorism and Counter-Terrorism Strategies Dr. Boaz Ganor Ronald Lauder Chair for Counter Terrorism, Founder & Executive Director, ICT The International Policy Institute for Counter-Terrorism, Deputy
Modern Terrorism and Counter-Terrorism Strategies Dr. Boaz Ganor Ronald Lauder Chair for Counter Terrorism, Founder & Executive Director, ICT The International Policy Institute for Counter-Terrorism, Deputy
Analyzing and Representing Two-Mode Network Data Week 8: Reading Notes
 Analyzing and Representing Two-Mode Network Data Week 8: Reading Notes Wasserman and Faust Chapter 8: Affiliations and Overlapping Subgroups Affiliation Network (Hypernetwork/Membership Network): Two mode
Analyzing and Representing Two-Mode Network Data Week 8: Reading Notes Wasserman and Faust Chapter 8: Affiliations and Overlapping Subgroups Affiliation Network (Hypernetwork/Membership Network): Two mode
Social Network Analysis in the Study of Terrorism and Insurgency: From Organization to Politics 1
 Zech, S.T., and M. Gabbay, "Social network analysis in the study of terrorism and insurgency: From organization to politics," Int. Stud. Rev., 18, 214-243, doi:10.1093/isr/viv011, 2016. http://isr.oxfordjournals.org/content/18/2/214
Zech, S.T., and M. Gabbay, "Social network analysis in the study of terrorism and insurgency: From organization to politics," Int. Stud. Rev., 18, 214-243, doi:10.1093/isr/viv011, 2016. http://isr.oxfordjournals.org/content/18/2/214
confronting terrorism in the pursuit of power
 strategic asia 2004 05 confronting terrorism in the pursuit of power Edited by Ashley J. Tellis and Michael Wills Regional Studies South Asia: A Selective War on Terrorism? Walter K. Andersen restrictions
strategic asia 2004 05 confronting terrorism in the pursuit of power Edited by Ashley J. Tellis and Michael Wills Regional Studies South Asia: A Selective War on Terrorism? Walter K. Andersen restrictions
Al Qaeda: Corporate hierarchy or biological entity?
 initiative for interdisciplinary research http://www.i2r.org Al Qaeda: Corporate hierarchy or biological entity? by Wojciech Gryc (wojciech@gmail.com) 1 / 9 Al Qaeda: Corporate hierarchy or biological
initiative for interdisciplinary research http://www.i2r.org Al Qaeda: Corporate hierarchy or biological entity? by Wojciech Gryc (wojciech@gmail.com) 1 / 9 Al Qaeda: Corporate hierarchy or biological
Statement for the Record. House Judiciary Subcommittee on Crime, Terrorism and Homeland Security. Hearing on Reauthorizing the Patriot Act
 Statement for the Record House Judiciary Subcommittee on Crime, Terrorism and Homeland Security Hearing on Reauthorizing the Patriot Act Statement for the Record Robert S. Litt General Counsel Office of
Statement for the Record House Judiciary Subcommittee on Crime, Terrorism and Homeland Security Hearing on Reauthorizing the Patriot Act Statement for the Record Robert S. Litt General Counsel Office of
An Assessment of 516 Combatant Status Review Tribunal (CSRT) Unclassified Summaries. 25 July 2007
 A RESPONSE TO THE SETON HALL STUDY An Assessment of 516 Combatant Status Review Tribunal (CSRT) Unclassified Summaries 25 July 2007 1 LTC JOSEPH FELTER, PH.D. DIRECTOR, COMBATING TERRORISM CENTER JARRET
A RESPONSE TO THE SETON HALL STUDY An Assessment of 516 Combatant Status Review Tribunal (CSRT) Unclassified Summaries 25 July 2007 1 LTC JOSEPH FELTER, PH.D. DIRECTOR, COMBATING TERRORISM CENTER JARRET
White Paper of the Interagency Policy Group's Report on U.S. Policy toward Afghanistan and Pakistan INTRODUCTION
 White Paper of the Interagency Policy Group's Report on U.S. Policy toward Afghanistan and Pakistan INTRODUCTION The United States has a vital national security interest in addressing the current and potential
White Paper of the Interagency Policy Group's Report on U.S. Policy toward Afghanistan and Pakistan INTRODUCTION The United States has a vital national security interest in addressing the current and potential
Protecting Australia Against Terrorism 2006
 Protecting Australia Against Terrorism 2006 Australia s National Counter-Terrorism Policy and Arrangements Commonwealth of Australia 2006 ISBN 0-9752387-9-5 This work is copyright. You may download, display,
Protecting Australia Against Terrorism 2006 Australia s National Counter-Terrorism Policy and Arrangements Commonwealth of Australia 2006 ISBN 0-9752387-9-5 This work is copyright. You may download, display,
Any response to Uri must factor in the Pakistani state s relationship with non-state actors.
 Inside, outside Any response to Uri must factor in the Pakistani state s relationship with non-state actors. Soldiers guard outside the army base which was attacked suspected militants in Uri, Jammu and
Inside, outside Any response to Uri must factor in the Pakistani state s relationship with non-state actors. Soldiers guard outside the army base which was attacked suspected militants in Uri, Jammu and
NATIONAL STRATEGY FOR COUNTERTERRORISM
 NATIONAL STRATEGY FOR COUNTERTERRORISM June 2011 THE WHITE HOUSE WASHINGTON June 28, 20 II As we approach the 10th anniversary ofal-qa'ida's terrorist attacks against the United States on September 11,2001,
NATIONAL STRATEGY FOR COUNTERTERRORISM June 2011 THE WHITE HOUSE WASHINGTON June 28, 20 II As we approach the 10th anniversary ofal-qa'ida's terrorist attacks against the United States on September 11,2001,
India-US Counterterrorism Cooperation: The Way Forward
 India-US Counterterrorism Cooperation: The Way Forward by Vinay Kaura BESA Center Perspectives Paper No. 555, August 8, 2017 EXECUTIVE SUMMARY: Narendra Modi s visit to the Trump White House in June was
India-US Counterterrorism Cooperation: The Way Forward by Vinay Kaura BESA Center Perspectives Paper No. 555, August 8, 2017 EXECUTIVE SUMMARY: Narendra Modi s visit to the Trump White House in June was
Terrorism and New Security Challenges Implications for European-Japanese Security Cooperation
 Terrorism and New Security Challenges Implications for European-Japanese Security Cooperation Volker STANZEL Federal Foreign Office There is general agreement among observers of international relations
Terrorism and New Security Challenges Implications for European-Japanese Security Cooperation Volker STANZEL Federal Foreign Office There is general agreement among observers of international relations
Terrorism in South Asia; Challenges for the West. Junaid Qureshi
 Terrorism in South Asia; Challenges for the West von Junaid Qureshi Dokument aus der Internetdokumentation des Deutschen Präventionstages www.praeventionstag.de Herausgegeben von Hans-Jürgen Kerner und
Terrorism in South Asia; Challenges for the West von Junaid Qureshi Dokument aus der Internetdokumentation des Deutschen Präventionstages www.praeventionstag.de Herausgegeben von Hans-Jürgen Kerner und
Montgomery County Community College CJS/EMP/POL/SOC 250 Terrorism & Counter-terrorism 3-3-0
 Montgomery County Community College CJS/EMP/POL/SOC 250 Terrorism & Counter-terrorism 3-3-0 AY17-18 COURSE DESCRIPTION: Terrorism in the 21 st century is a global phenomenon. This course is designed to
Montgomery County Community College CJS/EMP/POL/SOC 250 Terrorism & Counter-terrorism 3-3-0 AY17-18 COURSE DESCRIPTION: Terrorism in the 21 st century is a global phenomenon. This course is designed to
INTERNATIONAL TERRORISM AND COUNTERTERRORISM. Spring Political Science MWF , Maybank 316. Dr. Mary Desjeans
 INTERNATIONAL TERRORISM AND COUNTERTERRORISM Spring 2014 Political Science 379-01 MWF 1200-1250, Maybank 316 Dr. Mary Desjeans Office Hours: MW1100-1145 and by arrangement. Office Address: 26 Coming Street,
INTERNATIONAL TERRORISM AND COUNTERTERRORISM Spring 2014 Political Science 379-01 MWF 1200-1250, Maybank 316 Dr. Mary Desjeans Office Hours: MW1100-1145 and by arrangement. Office Address: 26 Coming Street,
Pakistan on the Brink: The Future of America, Pakistan, and Afghanistan. By Ahmed Rashid. New York, N.Y.: Viking, 2012.
 Volume 5 Number 4 Volume 5, No. 4: Winter 2012 Article 5 Pakistan on the Brink: The Future of America, Pakistan, and Afghanistan. By Ahmed Rashid. New York, N.Y.: Viking, 2012. Mark J. Roberts Follow this
Volume 5 Number 4 Volume 5, No. 4: Winter 2012 Article 5 Pakistan on the Brink: The Future of America, Pakistan, and Afghanistan. By Ahmed Rashid. New York, N.Y.: Viking, 2012. Mark J. Roberts Follow this
Transnational Justice on the Example of Countering the Financing of Terrorism in the USA and in Europe
 Transnational Justice on the Example of Countering the Financing of Terrorism in the USA and in Europe Dr. István László GÁL PhD, dr. habil. associate professor University of Pécs Faculty of Law Department
Transnational Justice on the Example of Countering the Financing of Terrorism in the USA and in Europe Dr. István László GÁL PhD, dr. habil. associate professor University of Pécs Faculty of Law Department
The Importance of Internal Security for Outlier Nations
 Countering Foreign Terrorist Fighters: The Importance of Internal Security for Outlier Nations By: Brittani Howell, J.D. Candidate 2017 Law 882 Research Center Research Questions and Thesis Research Questions
Countering Foreign Terrorist Fighters: The Importance of Internal Security for Outlier Nations By: Brittani Howell, J.D. Candidate 2017 Law 882 Research Center Research Questions and Thesis Research Questions
the notion that poverty causes terrorism. Certainly, economic theory suggests that it would be
 he Nonlinear Relationship Between errorism and Poverty Byline: Poverty and errorism Walter Enders and Gary A. Hoover 1 he fact that most terrorist attacks are staged in low income countries seems to support
he Nonlinear Relationship Between errorism and Poverty Byline: Poverty and errorism Walter Enders and Gary A. Hoover 1 he fact that most terrorist attacks are staged in low income countries seems to support
Building Global Alliances in the Fight against Terrorism
 Building Global Alliances in the Fight against Terrorism By Alistair Mill ar and Eric Rosand November 2007 This paper was commissioned by the Better World Campaign, a sister organization of the United
Building Global Alliances in the Fight against Terrorism By Alistair Mill ar and Eric Rosand November 2007 This paper was commissioned by the Better World Campaign, a sister organization of the United
TERRORISM Fervour is the weapon of choice of the impotent. FRANZ FANON, B l a c k S k i n, White Ma s k s (1952)
 TERRORISM Fervour is the weapon of choice of the impotent. FRANZ FANON, B l a c k S k i n, White Ma s k s (1952) Until the 1990s, terrorism was widely considered to be a security concern of the second
TERRORISM Fervour is the weapon of choice of the impotent. FRANZ FANON, B l a c k S k i n, White Ma s k s (1952) Until the 1990s, terrorism was widely considered to be a security concern of the second
WINTER. March 24. Template
 March 24 WINTER EQ- What are the different state shapes and types of boundaries? Agenda: 1. Daily Sheet 2. Review 3. Nation, State, Nation-States Gallery walk 4. Types of Boundaries Notes 4. Shapes of
March 24 WINTER EQ- What are the different state shapes and types of boundaries? Agenda: 1. Daily Sheet 2. Review 3. Nation, State, Nation-States Gallery walk 4. Types of Boundaries Notes 4. Shapes of
2014 GLOBAL TERRORISM INDEX
 2014 GLOBAL TERRORISM INDEX Institute for Economics and Peace Wednesday, 26 th November 2014 #TerrorismIndex INSTITUTE FOR ECONOMICS AND PEACE The Institute for Economics and Peace is an independent, not-for-profit,
2014 GLOBAL TERRORISM INDEX Institute for Economics and Peace Wednesday, 26 th November 2014 #TerrorismIndex INSTITUTE FOR ECONOMICS AND PEACE The Institute for Economics and Peace is an independent, not-for-profit,
Counter Terrorism Committee (CTC)
 Counter Terrorism Committee (CTC) Director: Renata Blanco Moderator: Andre Junele Secretary: Pamela Javelly Topic A: Combating self-funding terrorist organizations Description of The Committee Counter-Terrorism
Counter Terrorism Committee (CTC) Director: Renata Blanco Moderator: Andre Junele Secretary: Pamela Javelly Topic A: Combating self-funding terrorist organizations Description of The Committee Counter-Terrorism
REPUBLICAN NATIONAL COMMITTEE RESEARCH BRIEFING BOOK AUGUST 7, 2015
 REPUBLICAN NATIONAL COMMITTEE RESEARCH BRIEFING BOOK AUGUST 7, 2015 Paid For By The Republican National Committee. Not Authorized By Any Candidate Or Candidate s Committee. 310 First Street 1 SE, Washington
REPUBLICAN NATIONAL COMMITTEE RESEARCH BRIEFING BOOK AUGUST 7, 2015 Paid For By The Republican National Committee. Not Authorized By Any Candidate Or Candidate s Committee. 310 First Street 1 SE, Washington
What the Trump Administration Needs to Know: Lessons Learned from Fifteen Years of Counterterrorism Campaigns
 The Georgetown Security Studies Review (GSSR) ISSN: 2474-8552 (Print) 2474-8560 (Online) Journal homepage: http://www.georgetownsecuritystudiesreview.org/ What the Trump Administration Needs to Know: Lessons
The Georgetown Security Studies Review (GSSR) ISSN: 2474-8552 (Print) 2474-8560 (Online) Journal homepage: http://www.georgetownsecuritystudiesreview.org/ What the Trump Administration Needs to Know: Lessons
Terrorism in Africa: Challenges and perspectives
 African Training and Research Centre in Administration for Development Hanns Seidel Foundation The Governance of National Security: Challenges and Prospects New Strategies to Address Growing Security Threats
African Training and Research Centre in Administration for Development Hanns Seidel Foundation The Governance of National Security: Challenges and Prospects New Strategies to Address Growing Security Threats
Hyo-Shin Kwon & Yi-Yi Chen
 Hyo-Shin Kwon & Yi-Yi Chen Wasserman and Fraust (1994) Two important features of affiliation networks The focus on subsets (a subset of actors and of events) the duality of the relationship between actors
Hyo-Shin Kwon & Yi-Yi Chen Wasserman and Fraust (1994) Two important features of affiliation networks The focus on subsets (a subset of actors and of events) the duality of the relationship between actors
After the Cold War. Europe and North America Section 4. Main Idea
 Main Idea Content Statements: After the Cold War The Soviet Union collapsed in 1991 and the Cold War came to an end, bringing changes to Europe and leaving the United States as the world s only superpower.
Main Idea Content Statements: After the Cold War The Soviet Union collapsed in 1991 and the Cold War came to an end, bringing changes to Europe and leaving the United States as the world s only superpower.
The Terror OCTOBER 18, 2001
 The Terror OCTOBER 18, 2001 Philip C. Wilcox Jr. Font Size: A A A The author, a retired US Foreign Service officer, served as US Ambassador at Large for Counterterrorism between 1994 and 1997. The Bush
The Terror OCTOBER 18, 2001 Philip C. Wilcox Jr. Font Size: A A A The author, a retired US Foreign Service officer, served as US Ambassador at Large for Counterterrorism between 1994 and 1997. The Bush
Joe Wippl Spring 2017
 Joe Wippl Spring 2017 Fred Pardee School of Global Studies Boston University IR 556: PRESENT AND FUTURE INTELLIGENCE ISSUES: TERRORISM, PROLIFERATION, COUNTERINTELLIGENCE, ROGUE STATES AND NATIONAL/REGIONAL
Joe Wippl Spring 2017 Fred Pardee School of Global Studies Boston University IR 556: PRESENT AND FUTURE INTELLIGENCE ISSUES: TERRORISM, PROLIFERATION, COUNTERINTELLIGENCE, ROGUE STATES AND NATIONAL/REGIONAL
Criminological Theories
 Criminological Theories Terrorists have political goals, while criminal organizations pursue personal profit goals; but some analysts see growing convergence. Mexican drug smuggling cartels are engaged
Criminological Theories Terrorists have political goals, while criminal organizations pursue personal profit goals; but some analysts see growing convergence. Mexican drug smuggling cartels are engaged
Civil War and Political Violence. Paul Staniland University of Chicago
 Civil War and Political Violence Paul Staniland University of Chicago paul@uchicago.edu Chicago School on Politics and Violence Distinctive approach to studying the state, violence, and social control
Civil War and Political Violence Paul Staniland University of Chicago paul@uchicago.edu Chicago School on Politics and Violence Distinctive approach to studying the state, violence, and social control
Severing the Web of Terrorist Financing
 Severing the Web of Terrorist Financing Severing the Web of Terrorist Financing By Lee Wolosky Al Qaeda will present a lethal threat to the United States so long as it maintains a lucrative financial network,
Severing the Web of Terrorist Financing Severing the Web of Terrorist Financing By Lee Wolosky Al Qaeda will present a lethal threat to the United States so long as it maintains a lucrative financial network,
Counter-Terrorism as Crime Prevention: A Holistic Approach
 Center for Research on Extremism Counter-Terrorism as Crime Prevention: A Holistic Approach Tore Bjørgo Director of Center for Research on Extremism (C-REX), University of Oslo and Professor of Police
Center for Research on Extremism Counter-Terrorism as Crime Prevention: A Holistic Approach Tore Bjørgo Director of Center for Research on Extremism (C-REX), University of Oslo and Professor of Police
Joint open briefing for interested Member States, international, regional and subregional organizations on Central Asia
 Joint open briefing for interested Member States, international, regional and subregional organizations on Central Asia Counter-Terrorism Committee 1267 and 1988 Sanctions Committees Monday, 2 July 2018
Joint open briefing for interested Member States, international, regional and subregional organizations on Central Asia Counter-Terrorism Committee 1267 and 1988 Sanctions Committees Monday, 2 July 2018
Support RAND. For More Information RAND-INITIATED RESEARCH
 RAND-INITIATED RESEARCH CHILD POLICY CIVIL JUSTICE EDUCATION ENERGY AND ENVIRONMENT HEALTH AND HEALTH CARE INTERNATIONAL AFFAIRS NATIONAL SECURITY POPULATION AND AGING PUBLIC SAFETY SCIENCE AND TECHNOLOGY
RAND-INITIATED RESEARCH CHILD POLICY CIVIL JUSTICE EDUCATION ENERGY AND ENVIRONMENT HEALTH AND HEALTH CARE INTERNATIONAL AFFAIRS NATIONAL SECURITY POPULATION AND AGING PUBLIC SAFETY SCIENCE AND TECHNOLOGY
Transnational Terrorism: The Threat to Australia
 Transnational Terrorism: The Threat to Australia Transnational Terrorism: The Threat to Australia Commonwealth of Australia 2004 ISBN 1 920959 04 1 This work is copyright. Apart from any use as permitted
Transnational Terrorism: The Threat to Australia Transnational Terrorism: The Threat to Australia Commonwealth of Australia 2004 ISBN 1 920959 04 1 This work is copyright. Apart from any use as permitted
A Bayesian Model for Determining Crew Affiliation with Terrorist Organizations
 A Bayesian Model for Determining Crew Affiliation with Terrorist Organizations Quantitative Methods in Defense and National Security 21 Rick Haberlin May 25-26, 21 Agenda Background Research Model Case
A Bayesian Model for Determining Crew Affiliation with Terrorist Organizations Quantitative Methods in Defense and National Security 21 Rick Haberlin May 25-26, 21 Agenda Background Research Model Case
Building Global Alliances in the Fight Against Terrorism
 DON T GO IT ALONE: America s Interest in International Cooperation Building Global Alliances in the Fight Against Terrorism By Alistair Millar and Eric Rosand Center on Global Counterterrorism Cooperation
DON T GO IT ALONE: America s Interest in International Cooperation Building Global Alliances in the Fight Against Terrorism By Alistair Millar and Eric Rosand Center on Global Counterterrorism Cooperation
U.S. TREASURY DEPARTMENT OFFICE OF PUBLIC AFFAIRS
 U.S. TREASURY DEPARTMENT OFFICE OF PUBLIC AFFAIRS EMBARGOED UNTIL 8:30 AM EST: January 28, 2010 CONTACT: Marti Adams, Treasury Public Affairs (202) 622-2960 Assistant Secretary for Terrorist Financing
U.S. TREASURY DEPARTMENT OFFICE OF PUBLIC AFFAIRS EMBARGOED UNTIL 8:30 AM EST: January 28, 2010 CONTACT: Marti Adams, Treasury Public Affairs (202) 622-2960 Assistant Secretary for Terrorist Financing
The following text is an edited transcript of Professor. Fisher s remarks at the November 13 meeting. Afghanistan: Negotiation in the Face of Terror
 1 The following text is an edited transcript of Professor Fisher s remarks at the November 13 meeting. Afghanistan: Negotiation in the Face of Terror Roger Fisher Whether negotiation will be helpful or
1 The following text is an edited transcript of Professor Fisher s remarks at the November 13 meeting. Afghanistan: Negotiation in the Face of Terror Roger Fisher Whether negotiation will be helpful or
Freedom vs. Security: Guaranteeing Civil Liberties in a World of Terrorist Threats
 Freedom vs. Security: Guaranteeing Civil Liberties in a World of Terrorist Threats Speech by the Federal Minister of the Interior Dr Wolfgang Schäuble for the Bucerius Summer School on Global Governance
Freedom vs. Security: Guaranteeing Civil Liberties in a World of Terrorist Threats Speech by the Federal Minister of the Interior Dr Wolfgang Schäuble for the Bucerius Summer School on Global Governance
Foreign Fighter Interdiction: Stability Operations as Countermeasures
 by Major M. Daniel Kolva, U.S. Forces- Iraq April 1, 2011 Executive Summary Foreign fighters fuel the world s conflicts. They make conflicts more costly for host nations and peacekeepers. These extremists
by Major M. Daniel Kolva, U.S. Forces- Iraq April 1, 2011 Executive Summary Foreign fighters fuel the world s conflicts. They make conflicts more costly for host nations and peacekeepers. These extremists
Disrupting & Dismantling Transnational Criminal Organizations
 Disrupting & Dismantling Transnational Criminal Organizations Brandon Behlendorf, Ph.D. College of Emergency Preparedness, Homeland Security, and Cybersecurity University at Albany (State University of
Disrupting & Dismantling Transnational Criminal Organizations Brandon Behlendorf, Ph.D. College of Emergency Preparedness, Homeland Security, and Cybersecurity University at Albany (State University of
PC.DEL/764/08 15 September ENGLISH only
 PC.DEL/764/08 15 September 2008 ENGLISH only Statement by the United States Opening Session OSCE Follow-up Public-Private Partnership Conference: Partnership of State Authorities, Civil Society and the
PC.DEL/764/08 15 September 2008 ENGLISH only Statement by the United States Opening Session OSCE Follow-up Public-Private Partnership Conference: Partnership of State Authorities, Civil Society and the
Crisis Watch: An Assessment of Al Qaeda and Recommendations for the United Kingdom s Overseas Counter Terrorism Strategy
 Crisis Watch: An Assessment of Al Qaeda and Recommendations for the United Kingdom s Overseas Counter Terrorism Strategy In the United Kingdom s National Security Strategy (NSS) the National Security Council
Crisis Watch: An Assessment of Al Qaeda and Recommendations for the United Kingdom s Overseas Counter Terrorism Strategy In the United Kingdom s National Security Strategy (NSS) the National Security Council
M.S. in Criminology. B.S. in Criminology OFF CAMPUS CRIMINOLOGY DEGREE PROGRAMS
 OFF CAMPUS CRIMINOLOGY DEGREE PROGRAMS Information and new on-line applications are now available at the following web pages: M.S. in Criminology http://zimmer.csufresno.edu/~haralds/downtow ngraduateprogram08.htm
OFF CAMPUS CRIMINOLOGY DEGREE PROGRAMS Information and new on-line applications are now available at the following web pages: M.S. in Criminology http://zimmer.csufresno.edu/~haralds/downtow ngraduateprogram08.htm
C I E D C O E. Legal tools for prosecution of threat network agents May 26 th, This report can be downloaded from: BICES NATO CIED PORTAL
 Legal tools for prosecution of threat network agents May 26 th, 2017 C I E D C O E This report can be downloaded from: BICES NATO CIED PORTAL BICES COE CIED PORTAL http://www.ciedcoe.org/documents/documents/
Legal tools for prosecution of threat network agents May 26 th, 2017 C I E D C O E This report can be downloaded from: BICES NATO CIED PORTAL BICES COE CIED PORTAL http://www.ciedcoe.org/documents/documents/
PSC/IR 273 The Politics of Terrorism Fall :40am-10:55am, Dewey Alexander Lee
 Instructor: Email: alexander.mark.lee@rochester.edu Office: Harkness Hall 327 Office Hours: Tuesday 11:30-2 PSC/IR 273 The Politics of Terrorism Fall 2014 9:40am-10:55am, Dewey 2162 Alexander Lee Course
Instructor: Email: alexander.mark.lee@rochester.edu Office: Harkness Hall 327 Office Hours: Tuesday 11:30-2 PSC/IR 273 The Politics of Terrorism Fall 2014 9:40am-10:55am, Dewey 2162 Alexander Lee Course
US DRONE ATTACKS INSIDE PAKISTAN TERRITORY: UN CHARTER
 US DRONE ATTACKS INSIDE PAKISTAN TERRITORY: UN CHARTER Nadia Sarwar * The US President, George W. Bush, in his address to the US. Military Academy at West point on June 1, 2002, declared that America could
US DRONE ATTACKS INSIDE PAKISTAN TERRITORY: UN CHARTER Nadia Sarwar * The US President, George W. Bush, in his address to the US. Military Academy at West point on June 1, 2002, declared that America could
The Department of State s Annual Report on Terrorism
 The Department of State s Annual Report on Terrorism Testimony of Raphael F. Perl Specialist in International Affairs Foreign Affairs, Defense, and Trade Division Congressional Research Service Before
The Department of State s Annual Report on Terrorism Testimony of Raphael F. Perl Specialist in International Affairs Foreign Affairs, Defense, and Trade Division Congressional Research Service Before
Global Interdependence. Chapter Present
 Global Interdependence Chapter 36 1960-Present 1 Space The Impact of Science + Technology: Soviets launched 1 st satellite + had the 1 st man to orbit Earth 1969, US astronauts landed on the moon Later
Global Interdependence Chapter 36 1960-Present 1 Space The Impact of Science + Technology: Soviets launched 1 st satellite + had the 1 st man to orbit Earth 1969, US astronauts landed on the moon Later
Stopping the banned groups
 Stopping the banned groups Mehwish Rani Mehwish Rani is M.Phil in Psychology and an independent research analyst in the field of countering violent extremism. W hile the NAP lays down a comprehensive framework
Stopping the banned groups Mehwish Rani Mehwish Rani is M.Phil in Psychology and an independent research analyst in the field of countering violent extremism. W hile the NAP lays down a comprehensive framework
one time. Any additional use of this file, whether for
 one time. Any additional use of this file, whether for Islamabad and The Taliban sales, alterations or copying is strictly prohibited without written permission and fair compensation to BENAZIR BHUTTO,
one time. Any additional use of this file, whether for Islamabad and The Taliban sales, alterations or copying is strictly prohibited without written permission and fair compensation to BENAZIR BHUTTO,
The Transnational Threats Project at CSIS, in cooperation with the Center on Global Counterterrorism Cooperation. 5 June 2008
 Panel Discussion UN TERRORIST DESIGNATIONS AND SANCTIONS: A FAIR PROCESS AND EFFECTIVE REGIME? The Transnational Threats Project at CSIS, in cooperation with the Center on Global Counterterrorism Cooperation
Panel Discussion UN TERRORIST DESIGNATIONS AND SANCTIONS: A FAIR PROCESS AND EFFECTIVE REGIME? The Transnational Threats Project at CSIS, in cooperation with the Center on Global Counterterrorism Cooperation
EPP Policy Paper 1 A Secure Europe
 EPP Policy Paper 1 A Secure Europe We Europeans want to live in freedom, prosperity and security. Over more than 60 years, European integration and transatlantic cooperation has enabled us to achieve these
EPP Policy Paper 1 A Secure Europe We Europeans want to live in freedom, prosperity and security. Over more than 60 years, European integration and transatlantic cooperation has enabled us to achieve these
Supplementary Material for Preventing Civil War: How the potential for international intervention can deter conflict onset.
 Supplementary Material for Preventing Civil War: How the potential for international intervention can deter conflict onset. World Politics, vol. 68, no. 2, April 2016.* David E. Cunningham University of
Supplementary Material for Preventing Civil War: How the potential for international intervention can deter conflict onset. World Politics, vol. 68, no. 2, April 2016.* David E. Cunningham University of
Example 8.2 The Economics of Terrorism: Externalities and Strategic Interaction
 Example 8.2 The Economics of Terrorism: Externalities and Strategic Interaction ECONOMIC APPROACHES TO TERRORISM: AN OVERVIEW Terrorism would appear to be a subject for military experts and political scientists,
Example 8.2 The Economics of Terrorism: Externalities and Strategic Interaction ECONOMIC APPROACHES TO TERRORISM: AN OVERVIEW Terrorism would appear to be a subject for military experts and political scientists,
strategic asia asian aftershocks Richard J. Ellings and Aaron L. Friedberg with Michael Wills
 strategic asia 2002 03 asian aftershocks Edited by Richard J. Ellings and Aaron L. Friedberg with Michael Wills Regional Studies Southeast Asia Sheldon W. Simon restrictions on use: This PDF is provided
strategic asia 2002 03 asian aftershocks Edited by Richard J. Ellings and Aaron L. Friedberg with Michael Wills Regional Studies Southeast Asia Sheldon W. Simon restrictions on use: This PDF is provided
Weekly Geopolitical Report
 August 17, 2009 Pakistan and the Death of Baitullah Mehsud Reports indicated that on Aug. 5, Baitullah Mehsud, the notorious leader of the Taliban in Pakistan, died from a U.S. missile strike. In this
August 17, 2009 Pakistan and the Death of Baitullah Mehsud Reports indicated that on Aug. 5, Baitullah Mehsud, the notorious leader of the Taliban in Pakistan, died from a U.S. missile strike. In this
Second Interim Report of the National Commission on Terrorist Attacks Upon the United States. Thomas H. Kean, Chair, and Lee H. Hamilton, Vice Chair
 Second Interim Report of the National Commission on Terrorist Attacks Upon the United States Thomas H. Kean, Chair, and Lee H. Hamilton, Vice Chair September 23, 2003 The National Commission on Terrorist
Second Interim Report of the National Commission on Terrorist Attacks Upon the United States Thomas H. Kean, Chair, and Lee H. Hamilton, Vice Chair September 23, 2003 The National Commission on Terrorist
Continuing Conflict in SW Asia. EQ: What are the causes and effects of key conflicts in SW Asia that required U.S. involvement?
 Continuing Conflict in SW Asia EQ: What are the causes and effects of key conflicts in SW Asia that required U.S. involvement? Directions Today, we will be looking at the causes of important ongoing conflicts
Continuing Conflict in SW Asia EQ: What are the causes and effects of key conflicts in SW Asia that required U.S. involvement? Directions Today, we will be looking at the causes of important ongoing conflicts
National Strategy. for. of the United States of America
 National Strategy for Counterterrorism of the United States of America OCTOBER 2018 THE WHITE HOUSE WASHINGTON, DC My fellow Americans: I made a solemn promise to the American people to spare no effort
National Strategy for Counterterrorism of the United States of America OCTOBER 2018 THE WHITE HOUSE WASHINGTON, DC My fellow Americans: I made a solemn promise to the American people to spare no effort
Press Conference June
 Press Conference PRESS CONFERENCE (near verbatim transcript) Ambassador Peter Wittig, Germany s Permanent Representative to the United Nations; Chair of the UN Security Council Working Group on Children
Press Conference PRESS CONFERENCE (near verbatim transcript) Ambassador Peter Wittig, Germany s Permanent Representative to the United Nations; Chair of the UN Security Council Working Group on Children
INTERNATIONAL JOURNAL OF RESEARCH AND ANALYSIS VOLUME 4 ISSUE 2 ISSN
 THE LEGALITY OF ASSASSINATION OF OSAMA BIN LADEN UNDER INTERNATIONAL HUMANITARIAN LAW INTRODUCTION On 2 nd * ROMMYEL RAJ May 2011, the U.S Navy Seal Team 6 undertook a covert operation, Operation Geronimo
THE LEGALITY OF ASSASSINATION OF OSAMA BIN LADEN UNDER INTERNATIONAL HUMANITARIAN LAW INTRODUCTION On 2 nd * ROMMYEL RAJ May 2011, the U.S Navy Seal Team 6 undertook a covert operation, Operation Geronimo
UN Security Council Resolution on Foreign Terrorist Fighters (FTFs)
 Friday September 19 - V7 - BLUE UN Security Council Resolution on Foreign Terrorist Fighters (FTFs) 1. Reaffirming that terrorism in all forms and manifestations constitutes one of the most serious threats
Friday September 19 - V7 - BLUE UN Security Council Resolution on Foreign Terrorist Fighters (FTFs) 1. Reaffirming that terrorism in all forms and manifestations constitutes one of the most serious threats
Government Research Priorities for TSAS
 Government Research Priorities for TSAS TSAS works with a number of departments in government. This document alerts academic researchers to the questions that policy analysts find most interesting and
Government Research Priorities for TSAS TSAS works with a number of departments in government. This document alerts academic researchers to the questions that policy analysts find most interesting and
Democracy Corps - Third Way Frequency Questionnaire
 Democracy Corps - Third Way Frequency Questionnaire February 20-24, 2010 1,001 2008 Voters 851 Likely 2010 Voters (878 unweighted) 1 150 Drop-Off Voters (123 unweighted) 2 Q.3 First of all, are you registered
Democracy Corps - Third Way Frequency Questionnaire February 20-24, 2010 1,001 2008 Voters 851 Likely 2010 Voters (878 unweighted) 1 150 Drop-Off Voters (123 unweighted) 2 Q.3 First of all, are you registered
CRS Report for Congress
 Order Code RS21584 Updated November 3, 2003 CRS Report for Congress Received through the CRS Web Summary Pakistan: Chronology of Events K. Alan Kronstadt Analyst in Asian Affairs Foreign Affairs, Defense,
Order Code RS21584 Updated November 3, 2003 CRS Report for Congress Received through the CRS Web Summary Pakistan: Chronology of Events K. Alan Kronstadt Analyst in Asian Affairs Foreign Affairs, Defense,
Addressing Emerging Terrorist Threats and the Role of UNODC
 Addressing Emerging Terrorist Threats and the Role of UNODC Ms. Dolgor Solongo, Officer-in-Charge, ISS1 (Asia and Europe)/ Terrorism Prevention Branch 14 April 2015 Terrorism Evolving Global Threat Terrorism
Addressing Emerging Terrorist Threats and the Role of UNODC Ms. Dolgor Solongo, Officer-in-Charge, ISS1 (Asia and Europe)/ Terrorism Prevention Branch 14 April 2015 Terrorism Evolving Global Threat Terrorism
Twenty-Four Theses on Intelligence (Notes for OSS '02, 10 May 2002) by Martin van Creveld
 Twenty-Four Theses on Intelligence (Notes for OSS '02, 10 May 2002) by Martin van Creveld The purpose of these notes is to provide a brief, schematic, comparison between the problems facing intelligence
Twenty-Four Theses on Intelligence (Notes for OSS '02, 10 May 2002) by Martin van Creveld The purpose of these notes is to provide a brief, schematic, comparison between the problems facing intelligence
Soft Power and the War on Terror Remarks by Joseph S. Nye, Jr. May 10, 2004
 Soft Power and the War on Terror Remarks by Joseph S. Nye, Jr. May 10, 2004 Thank you very much for the kind introduction Bob. It s a pleasure to be with the Foreign Policy Association. I m going to try
Soft Power and the War on Terror Remarks by Joseph S. Nye, Jr. May 10, 2004 Thank you very much for the kind introduction Bob. It s a pleasure to be with the Foreign Policy Association. I m going to try
International Legal Framework on Counter-Terrorism As applicable to Pakistan
 International Legal Framework on Counter-Terrorism As applicable to Pakistan Mr. Jamal Aziz, Executive Director, RSIL Mr. Fahd Qaisrani, Research Associate, RSIL Day 3 Wednesday, 19 July 2017 What is
International Legal Framework on Counter-Terrorism As applicable to Pakistan Mr. Jamal Aziz, Executive Director, RSIL Mr. Fahd Qaisrani, Research Associate, RSIL Day 3 Wednesday, 19 July 2017 What is
Southeast Asia and the Brotherhood of Terrorism
 No. 860 Delivered November 19, 2004 December 20, 2004 Southeast Asia and the Brotherhood of Terrorism Dana R. Dillon Throughout Asia there are terrorist organizations, insurgencies, and revolutionaries
No. 860 Delivered November 19, 2004 December 20, 2004 Southeast Asia and the Brotherhood of Terrorism Dana R. Dillon Throughout Asia there are terrorist organizations, insurgencies, and revolutionaries
Weekly Geopolitical Report
 January 19, 2010 Reflections on Terrorism On December 25 th, Umar Farouk Abdulmutallab attempted to detonate an improvised explosive device (IED) on a Northwest Airlines flight. The flight, which originated
January 19, 2010 Reflections on Terrorism On December 25 th, Umar Farouk Abdulmutallab attempted to detonate an improvised explosive device (IED) on a Northwest Airlines flight. The flight, which originated
Conference on Use of the Internet to Counter the Appeal of Extremist Violence AGENDA
 Naif Arab University for Security Sciences Supported By In Partnership With Conference on Use of the Internet to Counter the Appeal of Extremist Violence Naif Arab University for Security Sciences, Riyadh,
Naif Arab University for Security Sciences Supported By In Partnership With Conference on Use of the Internet to Counter the Appeal of Extremist Violence Naif Arab University for Security Sciences, Riyadh,
Blockmodels/Positional Analysis Implementation and Application. By Yulia Tyshchuk Tracey Dilacsio
 Blockmodels/Positional Analysis Implementation and Application By Yulia Tyshchuk Tracey Dilacsio Articles O Wasserman and Faust Chapter 12 O O Bearman, Peter S. and Kevin D. Everett (1993). The Structure
Blockmodels/Positional Analysis Implementation and Application By Yulia Tyshchuk Tracey Dilacsio Articles O Wasserman and Faust Chapter 12 O O Bearman, Peter S. and Kevin D. Everett (1993). The Structure
Agenda: Protecting and Promoting Human Rights to Prevent and Counter Violent Extremism
 Agenda: Protecting and Promoting Human Rights to Prevent and Counter Violent Extremism Committee: Human Rights Council Student Officer: Soo Young Yun, President from Wikimedia Commons Introduction: With
Agenda: Protecting and Promoting Human Rights to Prevent and Counter Violent Extremism Committee: Human Rights Council Student Officer: Soo Young Yun, President from Wikimedia Commons Introduction: With
Authorizing the Use of Military Force: S.J. Res. 59
 May 16, 2018 Authorizing the Use of Military Force: S.J. Res. 59 Prepared statement by John B. Bellinger III Partner, Arnold & Porter Adjunct Senior Fellow in International and National Security Law, Council
May 16, 2018 Authorizing the Use of Military Force: S.J. Res. 59 Prepared statement by John B. Bellinger III Partner, Arnold & Porter Adjunct Senior Fellow in International and National Security Law, Council
Testimony of Lee S. Wolosky, Esq. Of Counsel, Boies, Schiller & Flexner LLP. U.S. Senate Committee on Banking, Housing, and Urban Affairs
 Testimony of Lee S. Wolosky, Esq. Of Counsel, Boies, Schiller & Flexner LLP U.S. Senate Committee on Banking, Housing, and Urban Affairs September 29, 2004 Mr. Chairman, Senator Sarbanes and Distinguished
Testimony of Lee S. Wolosky, Esq. Of Counsel, Boies, Schiller & Flexner LLP U.S. Senate Committee on Banking, Housing, and Urban Affairs September 29, 2004 Mr. Chairman, Senator Sarbanes and Distinguished
CIVILIAN TREATMENT AND THE WAR ON TERRORISM 2
 CIVILIAN TREATMENT AND THE WAR ON TERRORISM 2 The Effect of Civilian Treatment on the War on Terrorism Charles Midkiff Radford University CIVILIAN TREATMENT AND THE WAR ON TERRORISM 3 The Effect of Civilian
CIVILIAN TREATMENT AND THE WAR ON TERRORISM 2 The Effect of Civilian Treatment on the War on Terrorism Charles Midkiff Radford University CIVILIAN TREATMENT AND THE WAR ON TERRORISM 3 The Effect of Civilian
After the Fall of Daesh in Syria and Iraq: Counter-Radicalisation
 After the Fall of Daesh in Syria and Iraq: Implications for Radicalisation and Counter-Radicalisation Professor Peter R. Neumann King s College London @PeterRNeumann peter.neumann@kcl.ac.uk POSITIVE DEVELOPMENTS
After the Fall of Daesh in Syria and Iraq: Implications for Radicalisation and Counter-Radicalisation Professor Peter R. Neumann King s College London @PeterRNeumann peter.neumann@kcl.ac.uk POSITIVE DEVELOPMENTS
Statement of. Michael P. Downing Assistant Commanding Officer Counter-Terrorism/Criminal Intelligence Bureau Los Angeles Police Department.
 Statement of Michael P. Downing Assistant Commanding Officer Counter-Terrorism/Criminal Intelligence Bureau Los Angeles Police Department Before the Committee on Homeland Security s Subcommittee on Intelligence,
Statement of Michael P. Downing Assistant Commanding Officer Counter-Terrorism/Criminal Intelligence Bureau Los Angeles Police Department Before the Committee on Homeland Security s Subcommittee on Intelligence,
Confronting the Terror Finance Challenge in Today s Middle East
 AP PHOTO/MANU BRABO Confronting the Terror Finance Challenge in Today s Middle East By Hardin Lang, Peter Juul, and Trevor Sutton November 2015 WWW.AMERICANPROGRESS.ORG Introduction and summary In the
AP PHOTO/MANU BRABO Confronting the Terror Finance Challenge in Today s Middle East By Hardin Lang, Peter Juul, and Trevor Sutton November 2015 WWW.AMERICANPROGRESS.ORG Introduction and summary In the
UN Presentation- Combating the Evolving Threat from Foreign Terrorist Fighters
 UN Presentation- Combating the Evolving Threat from Foreign Terrorist Fighters Introduction Terrorist groups are increasingly radicalizing and inciting individuals worldwide to leave their homes and become
UN Presentation- Combating the Evolving Threat from Foreign Terrorist Fighters Introduction Terrorist groups are increasingly radicalizing and inciting individuals worldwide to leave their homes and become
Stuxnet, 2010 Target: Iranian Reactor, Natanz
 Stuxnet, 2010 Target: Iranian Reactor, Natanz DEFINITIONS DRONE: A machine that performs a preprogrammed task with or without human interaction. DEFINITIONS ROBOTIC SYSTEM: A machine with a limited degree
Stuxnet, 2010 Target: Iranian Reactor, Natanz DEFINITIONS DRONE: A machine that performs a preprogrammed task with or without human interaction. DEFINITIONS ROBOTIC SYSTEM: A machine with a limited degree
Lecture 2: What is Terrorism? Is this man a Terrorist or a Freedom Fighter?
 Lecture 2: What is Terrorism? Is this man a Terrorist or a Freedom Fighter? International Terrorism: What is Terrorism? A. Dr. Jim Ray (2010) argues that terrorism has been around for a long time- terrorist
Lecture 2: What is Terrorism? Is this man a Terrorist or a Freedom Fighter? International Terrorism: What is Terrorism? A. Dr. Jim Ray (2010) argues that terrorism has been around for a long time- terrorist
PRESS BRIEFING BY SECRETARY OF STATE HILLARY CLINTON ON HUMANITARIAN AID TO PAKISTAN James S. Brady Press Briefing Room
 PRESS BRIEFING BY SECRETARY OF STATE HILLARY CLINTON ON HUMANITARIAN AID TO PAKISTAN James S. Brady Press Briefing Room 11:25 A.M. EDT MR. GIBBS: A renewed guest appearance. Thank you all for coming. As
PRESS BRIEFING BY SECRETARY OF STATE HILLARY CLINTON ON HUMANITARIAN AID TO PAKISTAN James S. Brady Press Briefing Room 11:25 A.M. EDT MR. GIBBS: A renewed guest appearance. Thank you all for coming. As
Good afternoon. I want to thank Dr. Robert Satloff for his invitation to speak to you today.
 Remarks by David T. Johnson Assistant Secretary of State for the Bureau of International Narcotics and Law Enforcement Affairs Washington Institute for Near East Policy January 19, 2010 The Escalating
Remarks by David T. Johnson Assistant Secretary of State for the Bureau of International Narcotics and Law Enforcement Affairs Washington Institute for Near East Policy January 19, 2010 The Escalating
